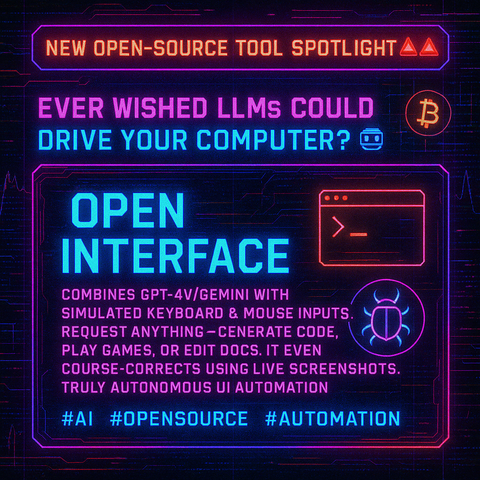
Ever thought of tunneling traffic over Azure Blob Storage? 🤔☁️
ProxyBlob lets you run a SOCKS5 proxy using Azure Storage as the communication channel. Useful in restrictive networks where only `*.blob.core.windows.net` is accessible. #Azure #Proxy #Networking
---
Why does ProxyBlob need Azure Storage? 💡📦
It creates a clever detour: Agents in target networks poll Azure Blob for tasks, while the proxy writes requests there. This avoids direct network connections for environments with strict rules. #Tech #CloudComputing
---
Missing direct network access but have Azure? Try Azurite! 🖥️🔨
ProxyBlob's agent also supports testing with Azurite, an open-source Azure Storage emulator. Use Docker or a VS Code extension to simulate an Azure Blob environment locally. #DevOps #Testing
---
How do SOCKS proxies over Azure even work? Let's simplify: 🎯
1. Proxy writes packets to Blob Storage.
2. Agent polls Blob, handles requests, and writes responses back.
3. Proxy retrieves responses, keeping the SOCKS5 flow alive. Smart and efficient. #Networking #Azure
---
Using ProxyBlob on-prem? Here's an essential setup note:
Test with `Azurite` before deploying on actual Azure. It emulates storage accounts with default credentials, helping validate configurations without cloud costs or risks. #CloudTools
🔗 Project link on #GitHub 👉 https://github.com/quarkslab/proxyblob
#Infosec #Cybersecurity #Software #Technology #News #CTF #Cybersecuritycareer #hacking #redteam #blueteam #purpleteam #tips #opensource #cloudsecurity
— ✨
🔐 P.S. Found this helpful? Tap Follow for more cybersecurity tips and insights! I share weekly content for professionals and people who want to get into cyber. Happy hacking 💻🏴☠️