@NemoJmeno
Pas de pression! Ça s'arrêterait là que personne serait déçu, on a déjà eu plein d'anecdotes insolites et de jolis dessins 😉
OSINT, CTI, adict to graphs and python scripts. ISO 3103 compliant.
Love to learn, learning is the beginning towards becoming a better human.
Not an English native, hope I don't sound too harsh.
He/him - 30 - Cyber Threat Analyst
@planina
I just love this rolodex use 😁
@NemoJmeno
Vraiment cette série est trop chouette! 😃
I had the [mis?]fortune of being awake just as attackers decided to slam the public internet with React2Shell exploits. GreyNoise had a tag up for it yesterday afternoon.
Full write-up of the initial spate of attacks:
https://www.greynoise.io/blog/cve-2025-55182-react2shell-opportunistic-exploitation-in-the-wild-what-the-greynoise-observation-grid-is-seeing-so-far
1/3
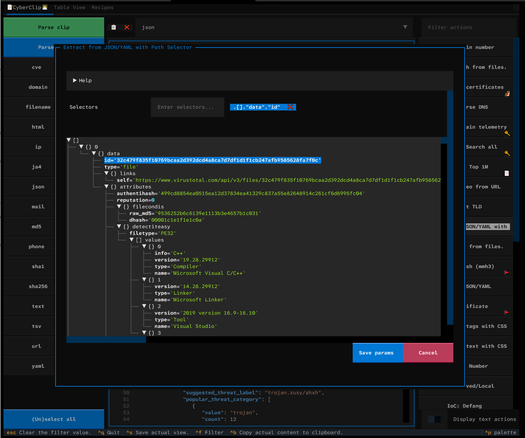
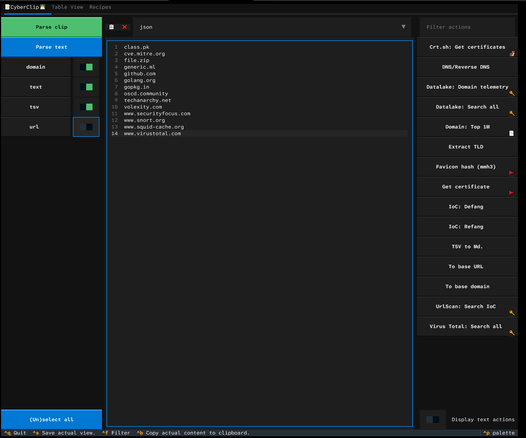
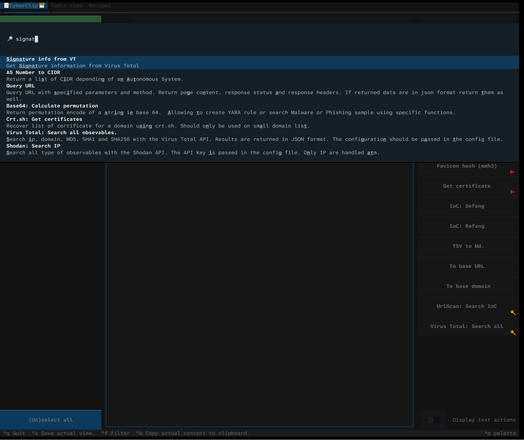
I just improved some features and fixed some bugs in Cyberclip.
- JSON data extraction
- Command palette search speed
- Hidden par default the text-related actions, as they clutter the UI. They are still accessible through the command palette (Ctrl+P).
Take a look at the images and alt text for more context. Feel free to reach out if you have any questions.
@NemoJmeno je sais pas si ca a déjà été mis, mais ça peut être?
https://fr.wikiquote.org/wiki/%C3%80_la_crois%C3%A9e_des_mondes#Le_Miroir_d'ambre
I just improved some features and fixed some bugs in Cyberclip.
- JSON data extraction
- Command palette search speed
- Hidden par default the text-related actions, as they clutter the UI. They are still accessible through the command palette (Ctrl+P).
Take a look at the images and alt text for more context. Feel free to reach out if you have any questions.
Support for PEP 723 (inline script metadata) has landed on pip's main branch thanks to some helpful guidance from the maintainers.
https://github.com/pypa/pip/commit/36987b0c31b97ffb9fb7949ded628e9a6b10c016
Here's hoping it'll smooth out some distribution wrinkles for people who have been getting along with just-pip and single-file scripts paired with requirements files 🤞
I'm offering a rare public, online session of my Applied #CTI #CyberThreatIntelligence training course in January for an evening North America/morning Australia/Asia timeframe, regiter your interest today!
https://forms.gle/i3n4srD6hWzfaX999
The Correct Incantation
The new issue of CTI Zine is about UrlScan, a URL scanning service. However, UrlScan is also useful for discovering more infrastructure related to phishing or malware.
So here it is:
https://github.com/BongoKnight/CTI-Zine/blob/main/20251120-Zine-Urlscan.pdf
You can also find a one-page A4 version that you can print and keep near your desk!
https://github.com/BongoKnight/CTI-Zine/blob/main/20251120-Zine-Urlscan-onepage.pdf
Feedbacks are welcome!
Over the last 12 months, watchTowr Labs uncovered thousands of leaked credentials: cloud keys, AD creds, API tokens, even KYC data - already being abused.
Join us on our journey into “innocent” developer tools.
@erin
(More on resip ecosystem here : https://blog.sekoia.io/unveiling-the-depths-of-residential-proxies-providers/
Or about Badbox one of the biggest ones that come preinstalled on Andoid TV ans is used as residential proxy
https://www.ncsc.gov.ie/pdfs/AndroidBadbox2-0.pdf
)
@erin
For the botnet part, I'm pretty sure that the use of residential proxy for trainning have been documented. I struggle for now to find a good source.
But as an example, LumiProxy, which is a shaddy residential proxy that publish ads on cybercrime forum and that is backed by botnets, advertise that it can be used to scrap for LLM training.
[nouveau sur la forge]
"Dessin Texte", qui permet de dessiner dans le navigateur, mais au lieu de juste faire un trait, le dessin est composé par les lettres d'un texte.
Plus on va vite, plus la police grossit. De quoi aborder la découverte des lettres de façons artistique en maternelle, et même après.
Une ressource (parmi 5768 autres) de la forge des communs numériques éducatifs que l'on doit à l'ERUN Hervé Allesant @Professeurherve
https://professeurherve.forge.apps.education.fr/dessintexte/
@Daniii
J'espère qu'il en restera quelque chose! Mais oui, tellement de gens sont subjugués et ne cherchent pas à verifier ce qui en sort.
Ça me terrifie d'autant plus que je bosse dans un secteur qui est ultra perméable aux LLM alors que dans mon taf on doit vérifier tout ce qu'on dit. Du coup, je lutte avec nos stagiaires.
On dirait que prendre son temps et rechercher la rigueur ça intéresse de moins en moins de monde!
@Daniii
L'IA ce fléau... Courage!
There are too many emojis, but you could think of it as a tribute to Screaminggoat. The investigation was made by a teammate and me (for IoC extraction)!
This week was super busy, but it started out really nice with attending #BSidesMunich together with a bunch of my colleagues. Fully enjoyed my time there, seeing folks from last editions and also #osco25 again, learning together. Many thanks to the organizers for giving us this space! Finally, here are the #sketchnotes I took during the #BSidesMunich2025 conference day. Thread. 🧵
Here is an article produced by my colleague Marine Pichon. It explore and merge many aliases of known malware tied to the North Korean Operation DreamJob.