the next generation of stalebots
He/him. Previously twitter.com/mnordhoff.
@xtaran @karotte @casandro @GossiTheDog
That's an old one! We came up with it for IPv6 when I was working at Microsoft. I think it was introduced in Windows XP SP1. We were worried that typing addresses like 2001:2:3::abcd was not going to work well in a variety of user interfaces, hence the "2001-2-3--abcd.ipv6-literal.net" hack. One of the team members (maybe me, not sure now) registered it on a personal account, and then transferred ownership to Microsoft before shipping.
I wish Internet scanners would spontaneously combust but, in the meantime, I wish they would operate more efficiently.
Sending 200 HTTP requests looking for WordPress exploits or variations of "/env" is godawful, and sending DNS queries to a different open resolver for each request so none of them are ever cached is even worse.
* Disclosure: Sometimes the call is coming from inside the house, but still.
Tailscale recently sent out a notification that they're moving their API at controlplane.tailscale.com, hosted on AWS EC2, to BYOIP addresses. RIP very neat IP 52.28.255.255. I hope they keep it if they have anything to use it for.
Though, really, Amazon has loads of /16s, so there must be other customers with similar IPs.
Edit: Also their control panel at https://login.tailscale.com/ runs on the same IPs.
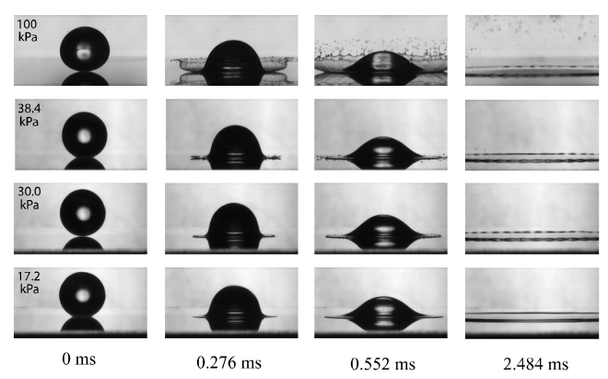
@fanf fig 1 in the referenced paper is cool
liquids don’t splash in a vacuum ?! https://youtu.be/aXTcYa7u12k
Wake up bae, new attack surface just dropped. Works outside UNC paths too, and MS don’t appear to own the domain 🤣
https://chaos.social/@karotte/114875319621020657
If an important DNS company simultaneously does a successful (though non-conservative) algorithm rollover of a customer zone, and completely botches some of their own corporate reverse DNS zones... I don't know whether to be impressed or not.
Akamai/Linode has been having a bad time since yesterday.
https://status.linode.com/incidents/wql6tnp1xgh7
They run approximately 2 object storage platforms—an older, lower-capacity one and a newer, higher-capacity one—divided into 4 "endpoint types" based on data center age and cluster size, and the newer platform is... down... with knock-on effects on k8s and some other services.
You may've seen @bagder 's post about mails he gets about CRA compliance from large companies asking him to answer all kinds of questions. I just saw a similar one to the maintainer of another important FOSS library. The kicker: The company uses a version from 2000. (Yes, no typo, 25 years old. I think it has some unfixed vulnerabilities.)
One of my domain names is expiring next month. It has a subdomain with a DNSSEC key with the tag "40". (Totally random, I didn't do anything.) RIP. :(
(I know I could copy it to another zone, but I don't think I will... maybe...)
@tychotithonus According to the announcement, you could get it from ftp://mhd3.moorhead.msus.edu/pub/linux/slackware at the time.
We need a version of The Unix Heritage Society for Linux.
On July 16, 1993, Patrick Volkerding announced Slackware Linux 1.0 to the comp.os.linux newsgroup.
Unfortunately, it's been lost from the Internet. The beta exists as does 1.0.1, but 1.0 is gone forever.
https://www.whalebone.io/aura-infrastructure Wait did Whalebone name their commercial DNS resolver product "Aura Infrastructure" as a marketing hack so it would have the acronym "AI"? :blobthinkingfast:
Unbound 1.23.1 in now available. This security release fixes the Rebirthday Attack CVE-2025-5994.
The vulnerability re-opens up #DNS resolvers to a birthday paradox, for EDNS client subnet servers that respond with non-ECS answers. The #CVE is described here:
https://nlnetlabs.nl/downloads/unbound/CVE-2025-5994.txt
We would like to thank Xiang Li (AOSP Lab, Nankai University) for discovering and responsibly disclosing the vulnerability.
https://github.com/NLnetLabs/unbound/releases/tag/release-1.23.1
@hanno I'm 99% sure some 2000s-era Windows had trouble with the apostrophe in the old "Let's Encrypt Authority X3" intermediates.* They really lucked out by avoiding that in the roots.
* More things had trouble with the name constraints...
https://blog.cloudflare.com/cloudflare-1-1-1-1-incident-on-july-14-2025/
Summary: Most of 1.1.1.1's IP addresses were accidentally included in the configuration for some new service, thus the routes were withdrawn globally when the service was deployed to a test data center.
Just a quickie from one of our @DomainTools researchers today that I know @cR0w will enjoy.
Malware in DNS - specifically, malware seen being assembled from DNS TXT records.
Not a "zomg new thing!" so much as a neat example in the wild.
How many parked (unused) domains do you own? I have an idea and want to know if my assumption is correct.
Boost generously, please.