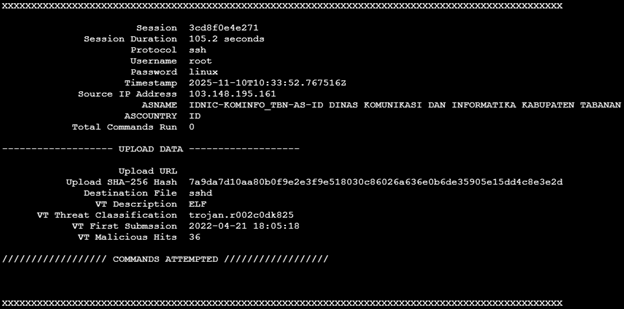
ISC Diary: ClickFix Attacks Still Using the Finger https://isc.sans.edu/diary/32566
http://isc.sans.edu - Global Network Security Information Sharing Community - honeypots, firewall logs, malware. SANS Technology Institute college research project
Apple Patches Everything: December 2025 Edition https://isc.sans.edu/diary/32564
Abusing DLLs EntryPoint for the Fun https://isc.sans.edu/diary/32562
SANS Stormcast Friday, December 12th, 2025: Local AI Models; Mystery Chrome 0-Day; SOAPwn Attack
https://isc.sans.edu/podcastdetail/9736
Using AI Gemma 3 Locally with a Single CPU https://isc.sans.edu/diary/32556
SANS Stormcast Thursday, December 11th, 2025: Possible CVE-2024-9042 variant; react2shell exploits; notepad++ update hijacking; macOS priv escalation
https://isc.sans.edu/podcastdetail/9734
Possible exploit variant for CVE-2024-9042 (Kubernetes OS Command Injection) https://isc.sans.edu/diary/32554
SANS Stormcast Wednesday, December 10th, 2025: Microsoft, Adobe, Ivanti, Fortinet, and Ruby patches.
https://isc.sans.edu/podcastdetail/9732
Microsoft Patch Tuesday December 2025 https://isc.sans.edu/diary/32550
SANS Stormcast Tuesday, December 9th, 2025: nanoKVM Vulnerabilities; Ghostframe Phishing; WatchGuard Advisory
https://isc.sans.edu/podcastdetail/9730
SANS Stormcast Monday, December 8th, 2025: AutoIT3 FileInstall; React2Shell Update; Tika Vuln
https://isc.sans.edu/podcastdetail/9728
No surprise: We do see active hits of the React Vulnerability (CVE-2025-55182) against our honeypots.
The initial exploit attempts we are seeing originate from the following two IP addresses: 193.142.147.209 and 95.214.52.170. The payloads are either "ping -c 1 45.157.233.80" or "console.log('CVE-2025-55182-VULN')"
If you find an unpatched React app in your environment, you should assume that it has been compromised at this point. Also be careful with apps that may have pinned older versions fo React/Next.js
AutoIT3 Compiled Scripts Dropping Shellcodes https://isc.sans.edu/diary/32542
SANS Stormcast Friday, December 5th, 2025: Compromised Govt System; React Vuln Update; Array Networks VPN Attacks
https://isc.sans.edu/podcastdetail/9726
SANS Stormcast Thursday, December 4th, 2025: CDN Headers; React Vulnerabiity; PickleScan Patch
https://isc.sans.edu/podcastdetail/9724
Nation-State Attack or Compromised Government? [Guest Diary] https://isc.sans.edu/diary/32536
Attempts to Bypass CDNs https://isc.sans.edu/diary/32532
SANS Stormcast Wednesday, December 3rd, 2025: SmartTube Compromise; NPM Malware Prompt Injection Attempt; Angular XSS Vulnerability
https://isc.sans.edu/podcastdetail/9722
SANS Stormcast Tuesday, December 2nd, 2025: Analyzing ToolShell from Packets; Android Update; Long Game Malicious Browser Ext.
https://isc.sans.edu/podcastdetail/9720
[Guest Diary] Hunting for SharePoint In-Memory ToolShell Payloads https://isc.sans.edu/diary/32524