Happy Monday, folks! It's time to shake off the cobwebs, so strap yourselves in and get your reading glasses out - here's a wrap-up of the week's infosec news, just for you: https://opalsec.substack.com/p/soc-goulash-weekend-wrap-up-4fe
Australia's mandatory reporting laws for Critical infrastructure operators got its first win last week, with the CISC revealing 47 cyber incidents were reported in the 8 months to December last year. Congrats, but what does that actually mean?
#GoDaddy finally twigged to a multi-year compromise of their networks, after users reported odd redirects impacting their website visitors. Turns out they'd likely been owned since at least March 2020, and appear to have failed to evict the attackers at least twice.
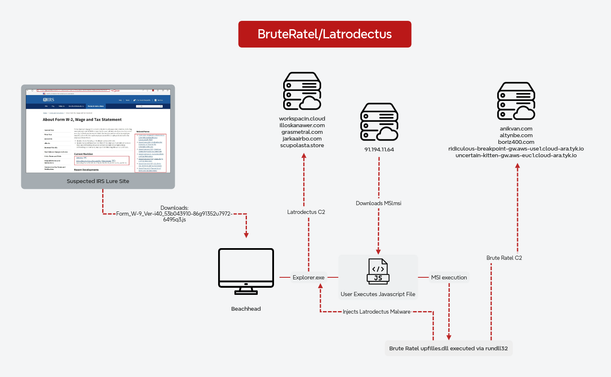
Havoc is the latest C2 framework to be thrown in anger, this time against a government target and in a multi-staged delivery chain which featured several evasive measures. Seems like Sliver and Brute Ratel may soon be in good company!
Symantec researchers have unearthed Frebniis - a stealthy IIS backdoor novel for it's hooking of a legitimate feature to covertly intercept attacker tasking.
A number of critical bugs in #Fortinet, #Apple, and #Citrix have been squashed - just make sure you know which ones, and apply those patches!
#redteam members are in for a treat, with a new Nim-based implant to play with and the OffensivePipeline tool to help automate obfuscation.
The #blueteam can look forward to a detailed look at attacks on #ESXi and how to mitigate it, as well as Hunt recommendations for evilginx2, and an update to Microsoft #Defender for Identity to help identify #ADCS abuse.
As always, there's literally dozens more research articles on threat actor activity and tradecraft that I can't summarise here, so make sure you take a look at this week's issue of SOC Goulash and get yourself up to speed!
https://opalsec.substack.com/p/soc-goulash-weekend-wrap-up-4fe
#infosec #CyberAttack #Hacked #cyber #news #cybernews #infosec #infosecnews #informationsecurity #cybersecurity #hacking #security #technology #hacker #vulnerability #vulnerabilities #malware #ransomware #dfir #soc #threatintel #threatintelligence #SliverC2 #BruteRatel #criticalinfrastructure