Sharpening the knife: strategic evolution of GOLD BLADE
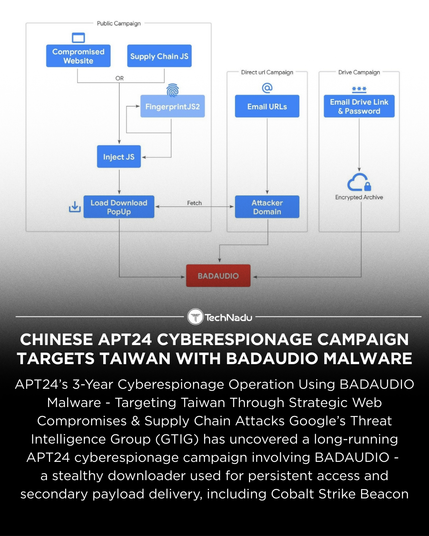
GOLD BLADE, a threat group previously focused on cyberespionage, has evolved into a hybrid operation combining data theft with selective ransomware deployment. The group has refined its intrusion methods, shifting from traditional phishing to abusing recruitment platforms for delivering weaponized resumes. Their operations follow cycles of dormancy and sudden activity bursts, introducing new tradecraft in each wave. GOLD BLADE has modified its RedLoader infection chain multiple times, implemented a Bring Your Own Vulnerable Driver approach, and developed a custom ransomware called QWCrypt. The group's targeting has narrowed to focus primarily on Canadian organizations across various sectors. Their sophisticated tactics and continual refinement demonstrate a level of operational maturity uncommon among financially motivated actors.
Pulse ID: 6933dbed9899a12d1dd9ae53
Pulse Link: https://otx.alienvault.com/pulse/6933dbed9899a12d1dd9ae53
Pulse Author: AlienVault
Created: 2025-12-06 07:31:57
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Canadian #CyberSecurity #Cyberespionage #DataTheft #Espionage #ICS #InfoSec #OTX #OpenThreatExchange #Phishing #RAT #RansomWare #bot #AlienVault