#Regulatory
It's been a busy 24 hours in the cyber world with significant updates on high-profile breaches, new malware campaigns, and some notable regulatory shifts. Let's dive into the latest cyber intel:
Recent Cyber Attacks & Breaches ⚠️
- Crisis24's OnSolve CodeRED emergency notification system was permanently shut down following a ransomware attack by INC ransomware, which led to the leak of PII including names, addresses, emails, phone numbers, and passwords.
- Gainsight customers, and potentially Zendesk users, have been impacted by the Scattered Lapsus$ Hunters (aka ShinyHunters) group, who are exploiting SaaS platforms with typosquatted domains and malicious helpdesk tickets to steal credentials and potentially deploy RATs.
- Asahi Group Holdings confirmed a September ransomware attack by Qilin group likely exposed personal data of nearly 2 million people, including customers, current/former employees, and their families, leading to significant operational delays and costs.
- OpenAI API users had limited identifying information exposed due to a smishing attack on their third-party analytics provider, Mixpanel; OpenAI has since terminated its relationship with Mixpanel and is notifying affected users.
- A Scottish council, Comhairle nan Eilean Siar, is still recovering two years after a ransomware attack, with several critical systems remaining unrestored and auditors highlighting persistent weaknesses in IT infrastructure and incident response.
- The FCC issued a warning after US radio stations were hijacked, with attackers exploiting unsecured broadcasting equipment to broadcast offensive content, including fake Emergency Alert System (EAS) tones.
🤫 CyberScoop | https://cyberscoop.com/crisis24-onsolve-codered-emergency-system-ransomware/
📰 The Hacker News | https://thehackernews.com/2025/11/gainsight-expands-impacted-customer.html
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/27/asahi_ransomware_numbers/
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/openai-discloses-api-customer-data-breach-via-mixpanel-vendor-hack/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/27/scottish_council_still_rebuilding_systems_two_years_after_ransomware_attack/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/27/fcc_radio_hijack/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/27/openai_cuts_off_mixpanel_after_analytics_leak_exposes_api_users/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/27/zendesk_users_targeted_as_scattered_lapsus_hunters_spin_up_fake_support_sites/
New Threat Research on Threat Actors/Groups, Ransomware, Malware, or Techniques and Tradecraft 🛡️
- A new Mirai-based botnet, ShadowV2, was observed exploiting multiple vulnerabilities in IoT devices (D-Link, TP-Link, etc.) for DDoS attacks, with activity potentially being a test run during an AWS outage.
- ESET uncovered QuietEnvelope, a sophisticated toolset likely from a state-sponsored actor (simplified Chinese debug strings), specifically designed to target OpenFind MailGates email protection systems with Perl scripts and stealthy backdoors for remote access.
- The Russia-aligned APT group Water Gamayun (aka EncryptHub) is exploiting the MSC EvilTwin flaw (CVE-2025-26633) via compromised websites and malicious JavaScript redirects to deploy loaders for backdoors or stealers.
- Microsoft identified Tycoon 2FA (Storm-1747) as the most prolific Phishing-as-a-Service (PaaS) platform, leveraging Adversary-in-the-Middle (AitM) techniques to steal credentials and session tokens from Microsoft 365, Gmail, and Outlook users.
- Xillen Stealer v5 introduces AI-evasion capabilities by mimicking legitimate user behaviour and adjusting resource usage, and includes an incomplete feature to use AI for identifying high-value targets based on weighted indicators.
- Bloody Wolf, an APT group, has expanded its Java-based NetSupport RAT campaigns to Kyrgyzstan and Uzbekistan, using spear-phishing with fake government documents to deliver JAR loaders and establish persistence in finance, government, and IT sectors.
- The Chinese-speaking Smishing Triad group is expanding its global smishing campaigns to Egypt, impersonating local financial and postal services using their Panda phishing kit and PhaaS platforms like Lighthouse.
- Threat actors are employing EtherHiding and ClickFix techniques, using compromised legitimate websites and blockchain-hosted JavaScript payloads (on Binance Smart Chain) to deliver infostealers like AMOS, Vidar, and Lumma Stealer after fake CAPTCHA checks.
- Kaspersky reports that threat actors continue to abuse NTLM, exploiting vulnerabilities (CVE-2024-43451, CVE-2025-24054, CVE-2025-33073) to leak hashes, escalate privileges, and move laterally, highlighting its ongoing security liability despite Microsoft's phase-out plans.
- Malicious Android APKs are impersonating legitimate services and using obfuscation to evade detection, exfiltrating stolen data to compromised legitimate websites that serve as command-and-control (C2) infrastructure.
- A new threat actor named NetMedved is targeting Russian companies with phishing emails containing ZIP archives with LNK files to drop NetSupport RAT.
- Kaspersky's analysis of the dark web job market reveals a parallel economy with high demand for IT specialists like developers, penetration testers, and reverse engineers (commanding highest salaries), with many teenagers seeking quick earnings.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/new-shadowv2-botnet-malware-used-aws-outage-as-a-test-opportunity/
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
📰 The Hacker News | https://thehackernews.com/2025/11/bloody-wolf-expands-java-based.html
Vulnerabilities 🚨
- A new Mirai-based botnet, ShadowV2, is actively exploiting at least eight known vulnerabilities in IoT devices from D-Link, TP-Link, DD-WRT, DigiEver, and TBK, including CVE-2024-10914 (a critical, known-to-be-exploited flaw in EoL D-Link devices).
- An unpatched security vulnerability in the Retell AI API allows AI voice agents with excessive permissions to be exploited for large-scale social engineering, phishing, and misinformation campaigns due to insufficient guardrails in its large language model (LLM).
- The Russia-aligned APT group Water Gamayun is exploiting the MSC EvilTwin flaw (CVE-2025-26633) to inject code into mmc.exe, leading to the deployment of loaders for backdoors or stealers.
- Threat actors continue to leverage multiple vulnerabilities in Microsoft Windows, including CVE-2024-43451, CVE-2025-24054, and CVE-2025-33073, to leak NTLM hashes, escalate privileges, and facilitate lateral movement within networks.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/new-shadowv2-botnet-malware-used-aws-outage-as-a-test-opportunity/
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
Threat Landscape Commentary 🌍
- Australia's ASIO chief, Mike Burgess, warned that Chinese state-backed threat actors are actively probing the country's telecoms networks and critical infrastructure, indicating a growing willingness by authoritarian regimes to use cyber sabotage.
- Kaspersky identified nearly 6.4 million phishing attacks in the first ten months of 2025, with 48.2% targeting online shoppers and over 2 million related to online gaming, highlighting a significant surge during the shopping season.
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
Data Privacy 🔒
- Thailand's data regulators have ordered TIDC Worldverse (representing Worldcoin) to halt the collection of iris biometrics and delete data from 1.2 million Thai citizens, following similar bans in other countries over privacy concerns.
- Mozilla is discontinuing its Monitor Plus service, which helped users remove data from data brokers, due to its partnership with Onerep, whose CEO was found to be operating numerous people search engine services.
- The Tor Project is implementing a major upgrade called Counter Galois Onion (CGO), replacing the long-standing relay encryption method to enhance privacy by raising the cost of active attacks, preventing traffic tampering, and adding forward secrecy.
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
Regulatory Issues & Changes ⚖️
- Singapore has mandated Apple and Google to implement new anti-spoofing protections on iMessage and RCS-supported Messages app for Android, aiming to block messages that impersonate government agencies or use the "gov.sg" sender ID.
- The Federal Communications Commission (FCC) has scrapped a set of telecom cybersecurity rules introduced after the Salt Typhoon espionage campaign, citing improved cybersecurity postures from carriers, though details on monitoring and enforcement remain unclear.
- The UK's National Crime Agency (NCA) exposed a billion-dollar money laundering network involving companies Smart and TGR, which laundered funds from cybercrime, drugs, and firearms, and acquired a bank in Kyrgyzstan to create "clean" cryptocurrency for Russian sanctions evasion.
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
Government Staffing & Program Changes 🏛️
- Polish authorities have detained a Russian citizen suspected of hacking local companies' IT systems and manipulating databases, linking the incident to broader Russian sabotage and espionage efforts in Poland and the EU.
- A 21-year-old Russian tech entrepreneur and cybersecurity specialist, Timur Kilin, was arrested in Moscow on treason charges, with suspicions that his criticism of state-backed messaging apps or government cyber legislation may have led to his detention.
- Two British teenagers have pleaded not guilty to Computer Misuse Act offenses in connection with a cyber attack on Transport for London (TfL) last year.
🗞️ The Record | https://therecord.media/poland-detains-russian-citizen-accused-of-hacks
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
Everything Else 💡
- Microsoft Defender for Office 365 has been updated to automatically remove associated calendar entries when malicious meeting invite emails are hard deleted, ensuring full eradication of threats from both inboxes and calendars.
- Microsoft plans to enhance Entra ID authentication security by blocking unauthorized script injection attacks from late October 2026, enforcing a Content Security Policy (CSP) that only allows scripts from trusted Microsoft domains as part of its Secure Future Initiative (SFI).
📰 The Hacker News | https://thehackernews.com/2025/11/threatsday-bulletin-ai-malware-voice.html
📰 The Hacker News | https://thehackernews.com/2025/11/microsoft-to-block-unauthorized-scripts.html
#CyberSecurity #ThreatIntelligence #Ransomware #APT #Malware #Vulnerability #DataBreach #IoT #Phishing #SocialEngineering #DataPrivacy #InfoSec #CyberAttack #IncidentResponse #Regulatory
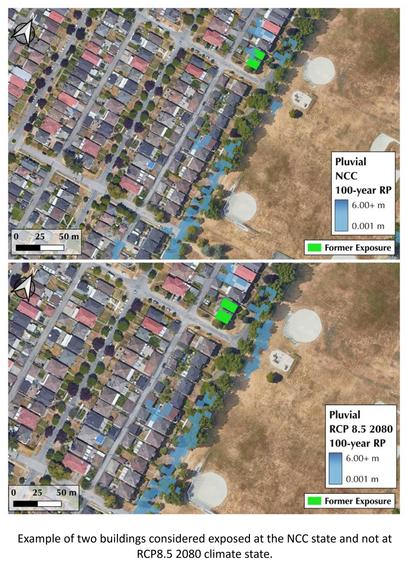
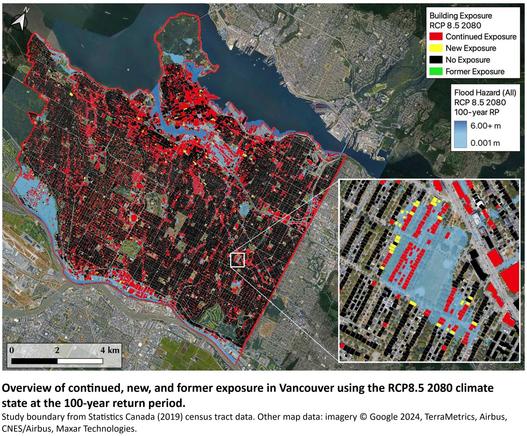
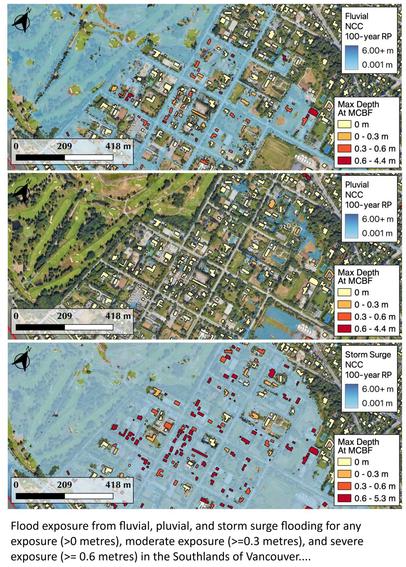
Mapping Current And Future Flood Exposure Using A 5 Metre Flood Model And Climate Change Projections [Vancouver, Canada]
--
https://nhess.copernicus.org/articles/24/699/2024/ <-- shared technical article
--
https://www.theguardian.com/environment/2021/nov/17/pacific-north-west-flooding-british-columbia-washington-state-canada <-- shared 2021 technical media article, PNW flooding
--
[this post should not be considered an endorsement of a specific vendor, etc]
#water #hydrology #flood #flooding #risk #hazard #Vancouver #BritishColumbia #Canada #climatechange #extremeweather #localfloods #GIS #spatial #mapping #riskassessment #spatialanalysis #floodexposure #riskmapping #model #modeling #floodriskmanagement #riskmanagement #naturaldisaster #rainfall #precipitation #stormsurge #hazardmapping #floodmapping #floodrisk #infrastructure #cost #economics #fluvial #pluvial #geomorphology #elevation #geomorphometry #regulatory #regulations #spatiotemporal
AI in Finance & Banking, 11/15/25 - https://www.llrx.com/2025/11/ai-in-finance-and-banking-november-15-2025/ Price of Intelligence: How Should Socially-minded Firms Price & Deploy AI?; The use of #AI 4 policy purposes; How #Tech Is Reshaping #Finance; How #Financial Firms Can Modernize Legacy Systems w/out Disrupting Core Operations; Central #banks, other supervisory #regulatory authorities need to “raise their game” due to effects of #AI on #economy; How #banks are laying foundation 4 #agenticAI; Gemini Deep Research comes to #Google Finance
The continuous rise of #AI is rapidly transforming business operations while dramatically expanding #cybersecurity threats and #regulatory needs! 🫣
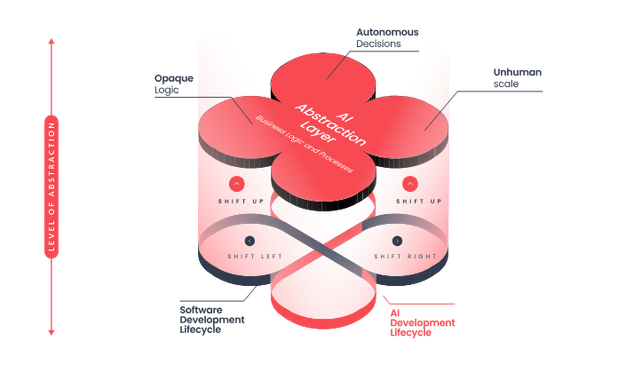
"Build Your AI Security Roadmap With the SAIL Framework" - The SAIL Framework provides a practical, lifecycle-oriented strategy to manage AI-specific risks and build trustworthy AI systems. Developed by practitioners, for practitioners. https://cybersec.pillar.security/s/build-your-ai-security-roadmap-with-the-sail-framework-23553
Alright team, it's been a busy 24 hours in the cyber world! We've got updates on recent breaches, some interesting new threat actor TTPs, critical vulnerabilities under active exploitation, and a few policy shifts to keep an eye on. Let's dive in:
Recent Cyber Attacks and Breaches 🚨
- The University of Pennsylvania confirmed a data breach affecting development and alumni systems, with hackers stealing 1.71 GB of internal documents and 1.2 million donor records after a successful social engineering attack on an employee's SSO account.
- SonicWall's September security breach, which exposed customer firewall configuration backup files, has been attributed to a state-sponsored threat actor. The investigation confirmed no impact on SonicWall products, firmware, or source code, but customers were advised to reset credentials.
- International law enforcement, in "Operation Chargeback," dismantled three credit card fraud and money laundering networks that stole over €300 million from 4.3 million cardholders across 193 countries, exploiting German payment service providers to process fake online subscriptions.
- The Apache Software Foundation is disputing claims by the Akira ransomware gang that it breached OpenOffice and stole 23 GB of data, stating they do not possess the types of data claimed, and their investigation found no evidence of compromise.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/university-of-pennsylvania-confirms-data-stolen-in-cyberattack/
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/sonicwall-says-state-sponsored-hackers-behind-security-breach-in-september/
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/europol-credit-card-fraud-rings-stole-eur-300-million-from-43-million-cardholders/
🗞️ The Record | https://therecord.media/europe-police-bust-global-fraud-ring-payment-firms
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/apache-openoffice-disputes-data-breach-claims-by-ransomware-gang/
New Threat Research on Actors, Malware, and TTPs 🕵🏼
- A new threat cluster, UNK_SmudgedSerpent, is targeting US academics and foreign policy experts with phishing attacks leveraging domestic political lures related to Iran, deploying legitimate RMM software like PDQ Connect, and mimicking Iranian cyber espionage groups like TA455 and TA453.
- Russia-linked Curly COMrades are innovating their cyber-espionage campaigns by hiding custom malware (CurlyShell and CurlCat) within lightweight Alpine Linux virtual machines running on Hyper-V, a tactic designed to bypass traditional endpoint detection tools.
- Google's Threat Intelligence Group (GTIG) reports a significant shift towards AI-powered malware, with new families like PromptFlux (a VBScript dropper using Gemini for obfuscation) and PromptSteal (a data miner) emerging, alongside various state-backed actors abusing LLMs for reconnaissance, malware development, and phishing.
📰 The Hacker News | https://thehackernews.com/2025/11/mysterious-smudgedserpent-hackers.html
🗞️ The Record | https://therecord.media/virtual-machines-cyber-espionage-russia-linked-curly-comrades
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/google-warns-of-new-ai-powered-malware-families-deployed-in-the-wild/
📰 The Hacker News | https://thehackernews.com/2025/11/researchers-find-chatgpt.html
Vulnerabilities and Active Exploitation ⚠️
- CISA has added two critical flaws to its KEV catalog due to active exploitation: CVE-2025-11371, a local file inclusion in Gladinet CentreStack/Triofox, and CVE-2025-48703, an unauthenticated RCE in Control Web Panel (CWP) via shell command injection. Federal agencies must patch by November 25th.
- Hackers are actively exploiting CVE-2025-11833, a critical 9.8-severity vulnerability in the Post SMTP WordPress plugin (affecting over 400,000 sites), allowing unauthenticated attackers to read email logs, including password reset messages, to hijack administrator accounts.
- OpenAI's ChatGPT has been found vulnerable to several indirect prompt injection techniques, including via trusted sites, search context, and conversation injection, which could lead to data leakage from user memories and chat histories.
- AMD is set to release microcode patches for CVE-2025-62626 (CVSS 7.2), a high-severity flaw in Zen 5 Epyc and Ryzen CPUs where the RDSEED function can return zero instead of a random number, potentially weakening cryptographic keys if an attacker has local privileges.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/hackers-exploit-wordpress-plugin-post-smtp-to-hijack-admin-accounts/
📰 The Hacker News | https://thehackernews.com/2025/11/cisa-adds-gladinet-and-cwp-flaws-to-kev.html
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/cisa-warns-of-critical-centos-web-panel-bug-exploited-in-attacks/
📰 The Hacker News | https://thehackernews.com/2025/11/researchers-find-chatgpt.html
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/05/amd_promises_to_fix_chips/
Threat Landscape Commentary 📉
- The US federal cybersecurity posture is facing a "perfect storm" due to the F5 security breach (attributed to a nation-state actor), proposed CISA job and funding cuts, and the ongoing government shutdown, collectively eroding cyber readiness and creating an expanded attack surface.
- House GOP leaders are pushing the Commerce Department to investigate and restrict Chinese government-connected tech products across critical industries like AI, energy, and industrial control systems, citing China's view of information technology as a battlefield.
- Congressional leaders are also urging federal agencies to develop a clear strategy to compete with China in 6G telecommunications and secure US tech supply chains, learning from past mistakes that allowed Chinese companies to gain significant global influence in 5G.
🤫 CyberScoop | https://cyberscoop.com/us-cyber-readiness-crisis-f5-breach-cisa-job-cuts-shutdown-op-ed/
🤫 CyberScoop | https://cyberscoop.com/house-gop-leaders-seek-government-probe-restrictions-on-chinese-made-tech/
🤫 CyberScoop | https://cyberscoop.com/exclusive-china-6g-letter-krishnamoorthi-congress-state-commerce-letters/
Data Privacy Concerns 🔒
- The US Department of Homeland Security (DHS) is proposing a sweeping expansion of biometric data collection for immigration applications, including iris scans, voice prints, and DNA, from immigrants and even some US citizens associated with these cases, raising significant privacy concerns.
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/04/dhs_wants_to_collect_biometric_data/
Regulatory Issues and Changes 🏛️
- The US Treasury Department has sanctioned two North Korean financial institutions and eight individuals for laundering over $12.7 million in cryptocurrency from cybercrime and fraudulent IT worker schemes, aiming to disrupt funding for Pyongyang's weapons programs.
- UK mobile carriers have committed to upgrading their networks within a year to block spoofed phone numbers, a key tactic used by scammers impersonating banks and government agencies, as part of a new Telecoms Charter to combat fraud.
- A House lawmaker predicts that Democratic support for the reauthorization of FISA Section 702, a key US national security surveillance power, will be a "heavier lift" in 2026 due to concerns over its use for warrantless searches of American data.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/us-treasury-sanctions-north-korean-bankers-linked-to-cybercrime-it-worker-fraud/
📰 The Hacker News | https://thehackernews.com/2025/11/us-sanctions-10-north-korean-entities.html
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/uk-carriers-to-block-spoofed-phone-numbers-in-fraud-crackdown/
🗞️ The Record | https://therecord.media/section-702-surveillance-powers-renewal-jim-himes-house-democrats
Other Noteworthy Updates 💡
- The UK's Department for Environment, Food & Rural Affairs (Defra) spent £312 million upgrading its IT estate, including replacing Windows 7 laptops with Windows 10, just as Windows 10 reached end-of-support, highlighting significant technical debt and potential future costs for extended security updates.
- Famed cryptographer and software engineer Daniel J. Bernstein (DJB) has given a favourable report on Fil-C, a new memory-safe C/C++ compiler based on Clang, noting its compatibility and ability to trap categories of C errors, despite performance drawbacks.
- Google's $32 billion acquisition of cloud security firm Wiz has received clearance from the US Department of Justice after an antitrust investigation, marking Google's largest-ever acquisition and a significant move to enhance Google Cloud's security offerings.
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/05/uk_defra_dept_spent_312m_window_10/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/05/djb_tries_filc_and_approves/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/11/05/googles_32b_wiz_acquisition_its/
#CyberSecurity #ThreatIntelligence #Vulnerabilities #ActiveExploitation #RCE #Malware #Ransomware #NationState #APT #AI #DataPrivacy #Regulatory #InfoSec #CyberAttack #IncidentResponse #SupplyChainSecurity
Alright team, it's been a pretty active 24 hours in the cyber world! We've got some significant law enforcement actions against ransomware and infostealer groups, several actively exploited zero-days to keep an eye on, and some important discussions around government policy and critical infrastructure security. Let's dive in:
Recent Cyber Attacks and Law Enforcement Action 🚨
- Oleksii Lytvynenko, an alleged Conti ransomware member, has been extradited from Ireland to the US, facing up to 25 years for wire fraud and computer fraud conspiracy. He's accused of involvement in data theft and ransom note deployment, with Conti extorting over $150 million globally.
- The University of Pennsylvania experienced a security incident where offensive "We got hacked" emails were sent to students and alumni, criticising the university's security and admission policies. The emails originated from a Penn mailing list platform hosted on Salesforce Marketing Cloud, which is currently under investigation.
- This extradition highlights ongoing international efforts to bring cybercriminals to justice, while the Penn incident serves as a reminder of the impact of even seemingly simple compromises on an organisation's reputation and operations.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/ukrainian-extradited-from-ireland-on-conti-ransomware-charges/
🤫 CyberScoop | https://cyberscoop.com/ukrainian-oleksii-lytvynenko-conti-ransomware-extradited/
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/offensive-we-got-hacked-emails-sent-in-penn-security-incident/
New Threat Research & Law Enforcement Crackdowns 🛡️
- Russian authorities have arrested three individuals suspected of developing and distributing Meduza Stealer, an info-stealing malware capable of "reviving" expired Chrome authentication cookies and linked to Aurora Stealer. This rare domestic crackdown follows the group's targeting of a Russian institution, signalling a potential shift in Russia's long-standing tolerance for cybercrime that avoids local targets.
- A new malware family, Airstalk, has been identified, deployed by a suspected nation-state actor (CL-STA-1009) in what appears to be a supply chain attack. Airstalk misuses the AirWatch MDM API for covert command-and-control, harvesting browser data and screenshots, with some samples signed by a likely stolen certificate.
- The Eclipse Foundation has revoked leaked tokens from Open VSX VS Code extensions after a Wiz report found them exposed in public repositories due to developer errors. New security measures, including a token prefix "ovsxp_" and automated scanning, are being implemented to bolster supply chain security.
🗞️ The Record | https://therecord.media/meduza-stealer-malware-suspected-developers-arrested-russia
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/alleged-meduza-stealer-malware-admins-arrested-after-hacking-russian-org/
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/10/31/russia_arrests_three_meduza_cyber_suspects/
🌐 The Hacker News | https://thehackernews.com/2025/10/nation-state-hackers-deploy-new.html
🌐 The Hacker News | https://thehackernews.com/2025/10/eclipse-foundation-revokes-leaked-open-vsx-tokens-following-wiz-discovery.html
Actively Exploited Vulnerabilities and Zero-Days ⚠️
- A Windows LNK zero-day (CVE-2025-9491) is being actively exploited by China-linked threat actor UNC6384 (Mustang Panda) in spearphishing campaigns targeting European diplomats. The flaw allows remote code execution via malicious LNK files to deploy the PlugX RAT, with no official Microsoft patch available yet.
- CISA has added a high-severity privilege escalation flaw in Broadcom VMware Tools and VMware Aria Operations (CVE-2025-41244) to its KEV catalog, noting active exploitation as a zero-day by China-linked UNC5174. This vulnerability allows unprivileged local actors to escalate to root.
- Unpatched Cisco IOS XE devices are still being targeted with BadCandy webshells, exploiting CVE-2023-20198 for unauthenticated root access. Australia warns of ongoing infections, attributing spikes to state-sponsored actors like China's Salt Typhoon, and advises immediate patching and hardening.
- A high-severity Linux kernel privilege escalation flaw (CVE-2024-1086) in netfilter: nf_tables is now actively exploited in ransomware attacks. CISA has added it to the KEV catalog, urging federal agencies to patch or apply mitigations like blocklisting 'nf_tables' or restricting user namespaces.
- Separately, CISA and NSA also highlighted active exploitation of CVE-2025-59287, a re-patched RCE flaw in Windows Server Update Services (WSUS), used by threat actors to harvest sensitive data from US organisations.
🌐 The Hacker News | https://thehackernews.com/2025/10/cisa-flags-vmware-zero-day-exploited-by.html
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/chinese-hackers-exploit-windows-zero-day-to-spy-on-european-diplomats/
🌐 The Hacker News | https://thehackernews.com/2025/10/china-linked-hackers-exploit-windows.html
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/australia-warns-of-badcandy-infections-on-unpatched-cisco-devices/
🗞️ The Record | https://therecord.media/chinese-hackers-scan-exploit-firewalls-government
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/cisa-linux-privilege-escalation-flaw-now-exploited-in-ransomware-attacks/
🌐 The Hacker News | https://thehackernews.com/2025/10/cisa-and-nsa-issue-urgent-guidance-to.html
Threat Landscape & Best Practices 🛡️
- CISA, NSA, and international partners have released a security blueprint for hardening on-premises Microsoft Exchange Servers, reiterating best practices like restricting admin access, MFA, strict TLS, zero-trust, and regular patching. This guidance is a response to the constant threat and complexity of Exchange security, which remains a prime target for nation-state and criminal actors.
- The UK's NHS is facing significant cybersecurity risks as 2% of its medical devices remain on unsupported Windows 10, with suppliers resisting upgrades to Windows 11 due to compatibility and cost issues. This situation forces trusts to quarantine devices and highlights the critical need for vendor cooperation and proactive patching to avoid past incidents like WannaCry.
- A US House Homeland Security Committee chairman's op-ed stresses the urgent need for government and industry collaboration to secure America's cyber future. Key priorities include strong information sharing, reducing duplicative compliance standards, bolstering the cyber workforce, and safely leveraging AI, while criticising the impact of government shutdowns on critical cybersecurity tools.
🤫 CyberScoop | https://cyberscoop.com/cisa-nsa-microsoft-exchange-server-guidance/
🌐 The Hacker News | https://thehackernews.com/2025/10/cisa-and-nsa-issue-urgent-guidance-to.html
🕵🏼 The Register | https://go.theregister.com/feed/www.theregister.com/2025/10/31/nhs_windows_11_issues/
🤫 CyberScoop | https://cyberscoop.com/defending-america-cybersecurity-national-security-private-sector-andrew-garbarino-op-ed/
Data Privacy & Regulatory Updates ⚖️
- Sling TV's parent company has settled with California's Attorney General for $530,000 over violations of the California Consumer Privacy Protection Act (CCPA). The streaming service allegedly failed to provide an easy opt-out for data sales and inadequately protected children's privacy, highlighting the need for clear, accessible privacy controls.
- The FCC plans to vote on removing cybersecurity regulations for telecommunications companies, which were initially implemented after Chinese hackers (Salt Typhoon) breached multiple providers to steal sensitive data from high-profile US officials. The FCC argues these regulations are "legally erroneous" and that voluntary industry efforts and partnerships are sufficient.
- The Consumer Financial Protection Bureau (CFPB) has closed its probe into Meta's practices regarding the use of consumer financial data for targeted advertising. The investigation had explored potential violations of the Consumer Financial Protection Act, which protects against unfair and deceptive financial practices.
🗞️ The Record | https://therecord.media/sling-tv-california-data-protection-settlement
🗞️ The Record | https://therecord.media/fcc-plans-vote-rescind-biden-era-ruling-telecoms-cyber
🗞️ The Record | https://therecord.media/cfpb-meta-probe-advertising
Government Staffing & Program Changes 🏛️
- Participants in the CyberCorps: Scholarship for Service program are facing significant debt, with job and internship offers rescinded due to federal hiring freezes and budget cuts. This situation forces students to convert their scholarships into loans if they cannot secure government employment within 18 months, raising concerns about the program's future and the government's cyber workforce pipeline.
- Students criticise the lack of clear communication and support from overseeing agencies, with some being told to "get creative" in their job searches. This "bait-and-switch" scenario is seen as undermining trust and future recruitment efforts for federal cyber talent.
Sponsored Content 🤝
- ThreatLocker has launched Defense Against Configurations (DAC) for macOS, currently in Beta, to help organisations identify and remediate security misconfigurations before they are exploited. DAC scans Macs up to four times daily, flagging risky settings like unencrypted drives, disabled firewalls, and permissive sharing, and provides remediation guidance aligned with frameworks like CIS and NIST.
- This new feature aims to provide Mac administrators with the same level of security insight and control previously available for Windows, addressing a common attack vector often overlooked in macOS environments.
🌐 The Hacker News | https://thehackernews.com/2025/10/a-new-security-layer-for-macos-takes.html
#CyberSecurity #ThreatIntelligence #Ransomware #NationState #APT #ZeroDay #Vulnerability #Malware #IncidentResponse #DataPrivacy #Regulatory #Government #InfoSec #CyberAttack #MicrosoftExchange #WSUS #VMware #Cisco #Linux #MeduzaStealer #Airstalk #SupplyChainSecurity
But #BigTech’s donations for #Trump’s pet cause come at a time when the industry’s giants have a lot riding on their relationships with the #WhiteHouse. In a marked shift from Trump’s first term, #tech leaders have spent most of the last 12 months singing the president’s praises as they navigate #antitrust cases, #tariffs, & #regulatory hurdles; fight for #contracts; & push for #policies that benefit their bottom lines.
2/2
🧐"LTA is involved in auditing a #system it had designed & approved, which might present an inherent #conflictofinterest.. When te matter is abt whether #LTA is performing its #regulatory functions effectively, its best done by an #independent body tt can look at issues objectively & fr a detached perspective. It shldn't be done by a #taskforce chaired by te CEO of te same organization, as is now te case.. Its been >13 years since #COI raised these questions, and.. te problem keeps recurring"