🚨 Shadowv2 Mirai variant hits vulnerable IoT ShadowV2 is a new Mirai spin targeting exposed IoT devices via weak creds and known flaws, adding persistence and stronger DDoS functions. Infections rise through mass scanning of consumer routers and cameras. #ransomNews #iot #mirai
#mirai
New #Mirai variant ShadowV2 tests IoT exploits amid AWS disruption
https://securityaffairs.com/185135/malware/new-mirai-variant-shadowv2-tests-iot-exploits-amid-aws-disruption.html
#securityaffairs #hacking
最古の調 Saiko no Shirabe
Радіо Поiзон_Райка.
Yakusokusareta an'nei no chi
https://www.pixiv.net/novel/show.php?id=25422049
<>
#learn_japanese #Japanese_learning #radio #natsuki_karin #cevio_ai #cool_Japan #kawaii #cute #free_resource #Poison_Raika #eien #toki #oeru #saiko #shirabe #ima #shunkan #yomigaeru #hibiku #kuroki #hieru #katamaru #kokoro #shin #shimiru #neiro #mirai #terasu
Angriff: ShadowV2- & RondoDox gegen IoT‑Geräte
Die hinter dem Mirai‑basierten ShadowV2‑Botnet stehenden Bedrohungsakteure wurden durch FortiGuard Lab-Forschende dabei beobachtet, IoT‑Geräte in verschiedenen Branchen und Kontinenten zu infizieren. Die Kampagne war offenbar nur während des Ausfalls von Amazon Web Services (AWS) Ende Oktober 2025 aktiv. Fortinet stuft die Aktivität als „ein Testlauf im Vorfeld zukünftiger Angriffe“ ein.
Mehr: https://maniabel.work/archiv/586
#Botnetz, #Malware, #Mirai, #RondoDox, #ShadowV2
#infosec #infosecnews
ShadowV2 Casts a Shadow Over IoT Devices
A new Mirai variant called ShadowV2 has been observed spreading through IoT vulnerabilities during a global AWS disruption. The malware targeted multiple countries and industries worldwide, exploiting vulnerabilities in devices from vendors like DD-WRT, D-Link, Digiever, TBK, and TP-Link. ShadowV2 is designed for IoT devices and uses a XOR-encoded configuration to connect to a C2 server for receiving DDoS attack commands. The malware supports various attack methods, including UDP floods, TCP-based floods, and HTTP-level floods. This incident highlights the ongoing vulnerability of IoT devices and the need for timely firmware updates, robust security practices, and continuous threat monitoring.
Pulse ID: 6927ffd2068d6127f3387514
Pulse Link: https://otx.alienvault.com/pulse/6927ffd2068d6127f3387514
Pulse Author: AlienVault
Created: 2025-11-27 07:37:54
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AWS #CyberSecurity #DDoS #DoS #HTTP #InfoSec #IoT #Malware #Mirai #OTX #OpenThreatExchange #RAT #TCP #UDP #Vulnerability #bot #AlienVault
最古の調 Saiko no Shirabe
Радіо Поiзон_Райка.
Yakusokusareta an'nei no chi
https://note.com/poison_raika/n/n0c0c7ea91291
<>
#learn_japanese #Japanese_learning #radio #natsuki_karin #cevio_ai #cool_Japan #kawaii #cute #free_resource #Poison_Raika #eien #toki #oeru #saiko #shirabe #ima #shunkan #yomigaeru #hibiku #kuroki #hieru #katamaru #kokoro #shin #shimiru #neiro #mirai #terasu
Tracking RondoDox: Malware Exploiting Many IoT Vulnerabilities
A new threat actor is distributing the RondoDox malware, a variant of Mirai, targeting IoT devices. The actor uses residential IP addresses for distribution and employs over a dozen exploits to target various IoT vulnerabilities. The malware's first stage is a shell script that attempts to disable security measures, remove competing malware, and download architecture-specific second-stage binaries. The campaign has been active since July 2025, with consistent use of a handful of distribution points. The actor targets home routers and other IoT devices using multiple CVEs and generic command injection attempts.
Pulse ID: 6926ce4acf381a3fb07c9efb
Pulse Link: https://otx.alienvault.com/pulse/6926ce4acf381a3fb07c9efb
Pulse Author: AlienVault
Created: 2025-11-26 09:54:18
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #InfoSec #IoT #Malware #Mirai #OTX #OpenThreatExchange #bot #AlienVault
紅きベール Akaki Beeru
Радіо Poison_Raika
Akaki beeru no nukumori de tsutsumita mae
https://www.pixiv.net/novel/show.php?id=24377621
<>
#Poison_Raika #channel #radio #natsuki_karin #cevio_ai #mayoibito #akaki #tsuki #michibiiku #beeru #nukumori #tsutsumu #tami #kokoro #kizami_komu #kibou #michi_afureru #akaruki #mirai #oku
紅きベール Akaki Beeru
Це канал, де читають вголос твори Poison_Raika.
Honjitsu goshoukai suru sakuhin wa Akaki Beeru desu
https://note.com/poison_raika/n/n7fb67483ae7f
<>
#Poison_Raika #channel #radio #natsuki_karin #cevio_ai #mayoibito #akaki #tsuki #michibiiku #beeru #nukumori #tsutsumu #tami #kokoro #kizami_komu #kibou #michi_afureru #akaruki #mirai #oku
https://companydata.tsujigawa.com/press-20251109-002/
株式会社DATAREIN(本社:愛知県名古屋市)は、浜松地域初となる子ども向け生成AI活用スクール「AIスクール mirAI(ミライ)浜松校」を2025年12月1日(日)に開校します。
個別メンタリングとライブ型グループ授業を組み合わせたハイブリッド学習により、子どもが「好き」を原動力に学び続けられる教育環境を提供します。
■プレスリリース配信元-株式会社DATAREIN
https://companydata.tsujigawa.com/company/7180003026761/
Attacks to exploit router vulnerabilities to execute commands and spread malware account for 75% of all attacks, according to Zscaler report
https://www.admin-magazine.com/News/Routers-Remain-Top-Target-for-IoT-Attacks-Per-Zscaler-Report?utm_source=mam
#router #vulnerabilities #IoT #malware #Mirai #Mozi #Android #spyware #Zscaler
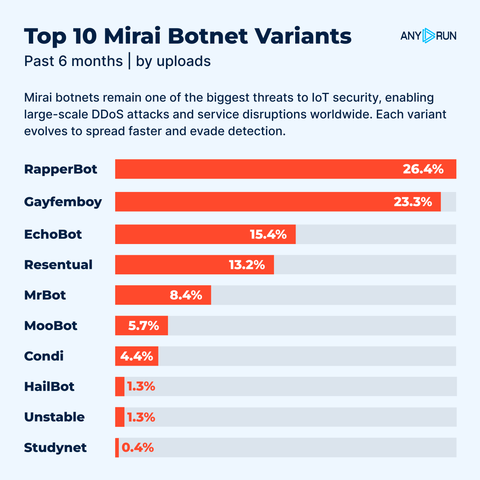
🚨 Top 10 #Mirai Botnet Variants.
Mirai is one of the most persistent IoT #malware families, powering large-scale DDoS attacks through infected devices like routers and smart cameras. Its source code was leaked back in 2016, giving rise to countless modified versions.
⚠️ Each variant adapts Mirai’s original code to spread faster, evade defenses, or launch stronger attacks.
📊 Based on #ANYRUN detections over the past six months, here are the 10 most active Mirai variants, along with live analysis sessions:
RapperBot: https://app.any.run/tasks/6c7702a2-2f08-45b7-b6b0-99310e166d2a/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
Gayfemboy: https://app.any.run/tasks/68cb3a16-8075-439a-be53-649ead73367c/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
EchoBot: https://app.any.run/tasks/8ff81508-8ffc-44cd-aa39-97bb659c2fce/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
Resentual: https://app.any.run/tasks/5135a499-2d21-4a0c-a39b-ebe144781e02/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
MrBot: https://app.any.run/tasks/6f64d319-b59c-41eb-b176-84e7a3b90c64/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
MooBot: https://app.any.run/tasks/1891e8f4-7812-40f9-b94a-7086ae2d47d6/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
Condi: https://app.any.run/tasks/f6c05a49-68bc-462f-bd51-e2eb856e749e/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
HailBot: https://app.any.run/tasks/dc43faf7-66cb-40de-864e-38f1871ab6cb/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
Unstable: https://app.any.run/tasks/33270057-c0e5-4513-9257-5664ae99f2f8/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
Studynet: https://app.any.run/tasks/403ea090-6323-4575-856a-31d1f6a57314/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoservice
A single Mirai infection can turn corporate IoT into a weapon, causing outages and costly downtime. Equip your team with real-time analysis and full visibility across Linux, Windows, and Android to accelerate detection & response.
🔍 Use this TI Lookup search query to monitor botnet activity and enrich detection logic with live threat data: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_content=linktotilookup&utm_term=121125#%7B%2522query%2522:%2522threatName:%255C%2522botnet%255C%2522%2522,%2522dateRange%2522:60%7D%20
🎯 Boost resilience and visibility #ANYRUN. Start today: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_mirai_variants&utm_term=121125&utm_content=linktoregister#register
哲学に扱かれた
汝、哲学の金槌を頭に
振り下ろされる覚悟は宜しくて?
https://www.deviantart.com/deadly-poison-0/art/Tetsu-gaku-ni-Shigokareta-jp-1253818934
<>
#AI小説 #hiru_yasumi #shukuzu #bentou #kakomu #djugyou #yoshuu #gamen #mirai #kibou #takusu #kousha #kioku #netto #koufun #yousu #kagayaku #koukoku #gazou #miru #hitomi #kaiwa #daihyou #kinou #kimatsu #tesuto
Філософська прочуханка
Чи готові ви до того, щоб молот філософії
обрушився на вашу голову?
https://www.deviantart.com/deadly-poison-0/art/Tetsu-gaku-ni-Shigokareta-ua-1253819448
<>
#AI小説 #hiru_yasumi #shukuzu #bentou #kakomu #djugyou #yoshuu #gamen #mirai #kibou #takusu #kousha #kioku #netto #koufun #yousu #kagayaku #koukoku #gazou #miru #hitomi #kaiwa #daihyou #kinou #kimatsu #tesuto
Філософська прочуханка
Чи готові ви до того, щоб молот філософії
обрушився на вашу голову?
https://www.pixiv.net/novel/show.php?id=26223706
<>
#AI小説 #hiru_yasumi #shukuzu #bentou #kakomu #djugyou #yoshuu #gamen #mirai #kibou #takusu #kousha #kioku #netto #koufun #yousu #kagayaku #koukoku #gazou #miru #hitomi #kaiwa #daihyou #kinou #kimatsu #tesuto
Філософська прочуханка
Чи готові ви до того, щоб молот філософії
обрушився на вашу голову?
https://note.com/deadly_poison_0/n/n40c583137814
<>
#AI小説 #hiru_yasumi #shukuzu #bentou #kakomu #djugyou #yoshuu #gamen #mirai #kibou #takusu #kousha #kioku #netto #koufun #yousu #kagayaku #koukoku #gazou #miru #hitomi #kaiwa #daihyou #kinou #kimatsu #tesuto
Teja Sajja Speech at MIRAI Celebration Meet | Manchu Manoj | Karthik Gattamneni | Ritika | BIG TV ET
Teja Sajja Speech at MIRAI Celebration Meet | Manchu Manoj | Karthik Gattamneni | Ritika | BIG TV ET #tejasajja #mirai #karthikgattamneni #manchumanoj #celebrationmeet #bigtventertainment Watch LIVE Stream : 🔔 Subscribe to our channel ✅ Stay Connected to Us. 👉 Website: 👉 Facebook: 👉 Twitter: 👉 WhatsApp: 👉 Instagram: BIG TV Entertainment channel dedicated to all things…