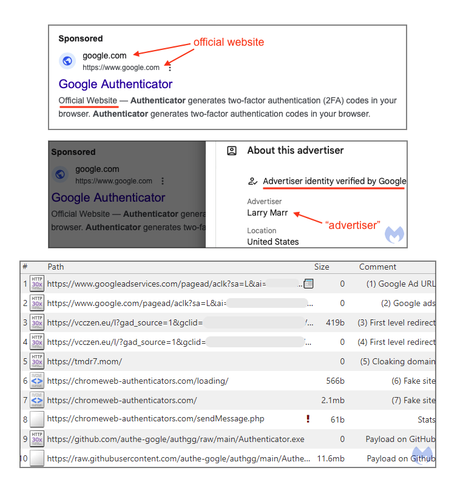
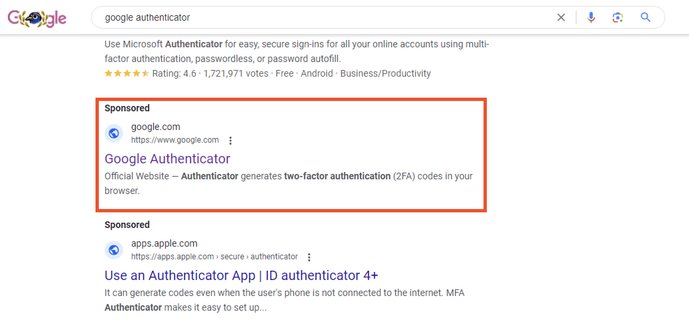
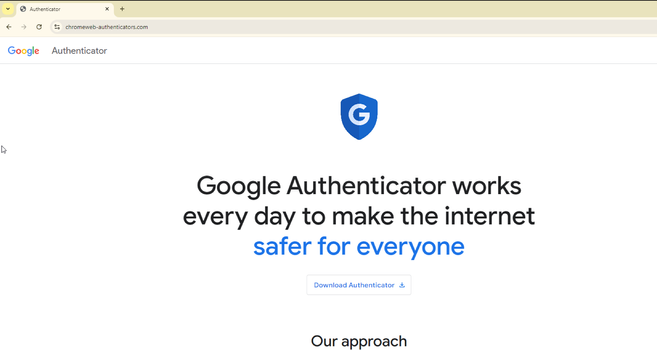
I wrote a quick blog post on this ongoing #malvertising campaign disguised as Google Authenticator and using.... Google ads.
🏴☠️ OFFENSIVE-INTEL 🏴☠️ Cyber Threat Intelligence by Hackers | Security Researcher en CronUp.com | @CuratedIntel Member | 🥷🧠🇨🇱
@th3_protoCOL + https://github[.]com/authe-gogle/authgg
Google #malvertising impersonating google authenticator
🎣 chromeweb-authenticators[.]com
📂 "Authenticator.exe"
Delivers digitally signed malware with a low detection ratio on #virustotal
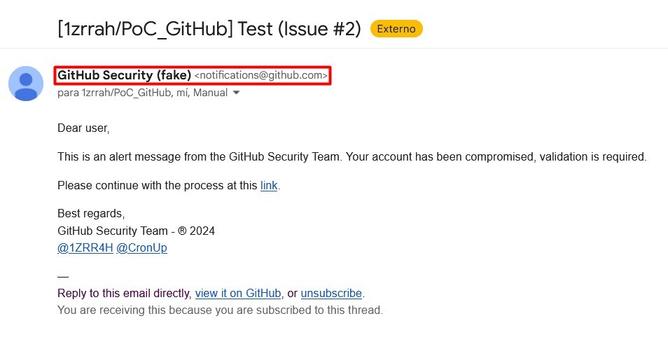
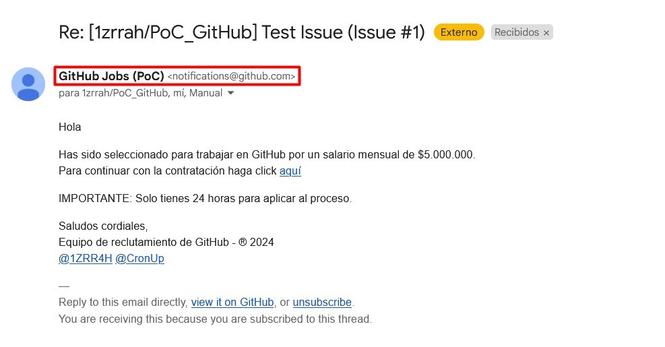
🚨 Watch out, threat actors are exploiting another GitHub feature related to the commenting and notification system.
With the above, they manage to deliver #phishing emails through the legitimate account "notifications@github[.]com". In addition, the sender's name can be manipulated by renaming the attacker's GitHub account.
Two campaigns seen:
1⃣ New Gitloker attacks wipe GitHub repos in extortion scheme > https://bleepingcomputer.com/news/security/new-gitloker-attacks-wipe-github-repos-in-extortion-scheme/
2⃣ Crypto scams on GitHub > https://github.com/orgs/community/discussions/83803
Damn, I really thought the Recall database security would at least be, you know, secure. Turns out Microsoft did pretty much what I blogged about for WindowsApps, except you need to find a specific WIN://SYSAPPID instead. So to bypass the security just get the token for the AIXHost.exe process, then impersonate that and you can access the database, no admin required. Or, as the files are owned by the user, just grant yourself access using icacls etc :D
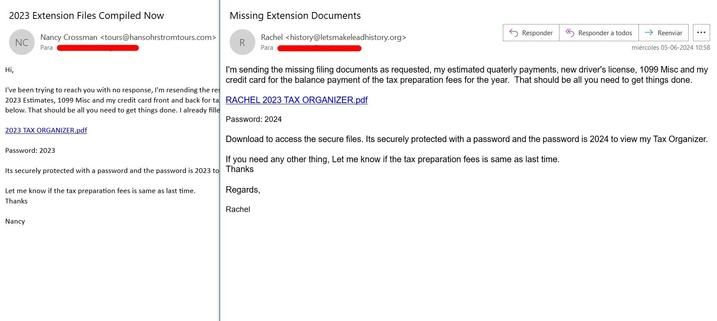
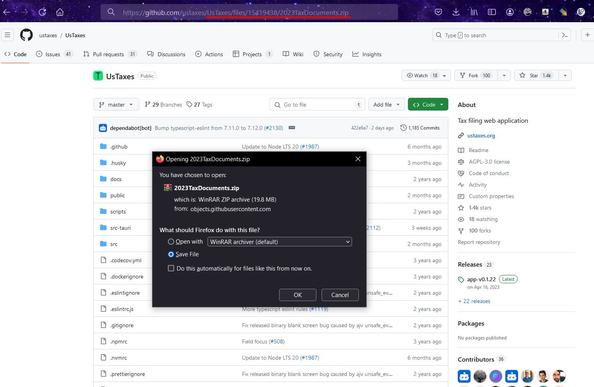
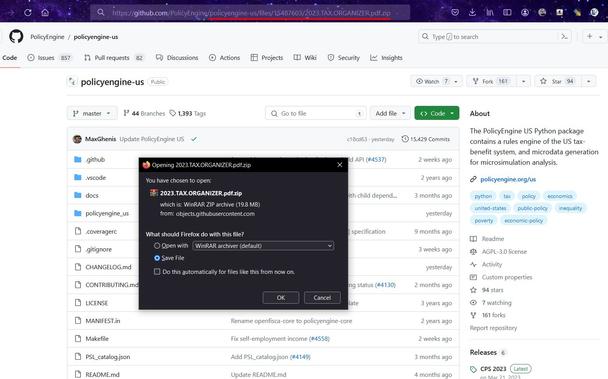
🚩 Active #RemcosRAT campaign is distributed via GitHub through abuse of comments in legitimate repositories.
Some malicious links:
- https://github[.]com/ustaxes/UsTaxes/files/15421286/2022and2023TaxDocuments[.]zip
- https://github[.]com/ustaxes/UsTaxes/files/15419438/2023TaxDocuments[.]zip
- https://github[.]com/PolicyEngine/policyengine-us/files/15487603/2023.TAX.ORGANIZER.pdf[.]zip
- https://github[.]com/hmrc/claim-tax-refund/files/15487332/TaxrefundlistPDF[.]zip
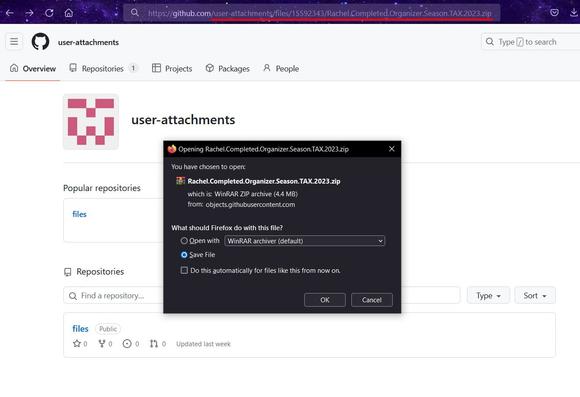
They also got creative and registered the user "user-attachments" on GitHub 😄
- https://github[.]com/user-attachments/files/15592343/Rachel.Completed.Organizer.Season.TAX.2023[.]zip
Remcos C2 servers:
- pattreon.duckdns[.]org:7035
- deytrycooldown.duckdns[.]org:7070
- newlink.duckdns[.]org:5111
* Botnet: RemoteHost
FIN7 #malvertising #threatintel
concuur[.]net
concuur[.]org
concuur[.]com
concur2024[.]com
96dfb6337647d890875919334a8dfc1f8f6e887f4b9ff6afedfb3574c7b444a3
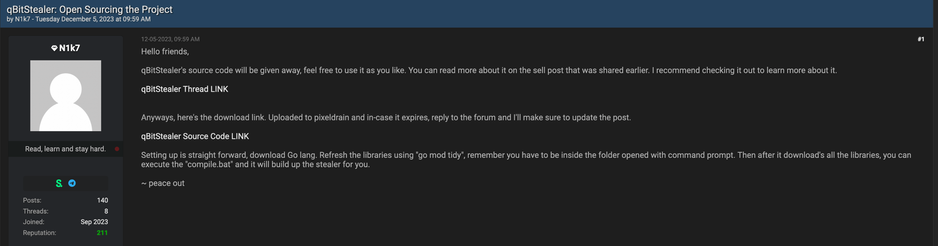
Today: Detecting the "qBit Stealer" exfiltration tool
qBit Stealer was developed by the "qBit #Ransomware-as-a-Service" group to exfiltrate victim data to the MEGA file sharing service. It is implemented in #Golang.
About two months ago the source code of qBit Stealer was published on BreachForums for anyone to use and repurpose (Image 1).
Based on the source code and the sample shared by @1ZRR4H (https://twitter.com/1ZRR4H/status/1751656174515098023), we created a YARA rule to look for qBit Stealer samples (Image 2).
Interestingly, most of the in-the-wild samples contain build artifacts of the "XFiltr8" variant, compiled by a user named "187ir".
We only found two other public samples that contain different path artifacts (Image 3).
Paths and hashes:
C:/Users/187ir/Golang-Projects/XFiltr8/Builder/XFiltr8.go
089ba2fb4eaa13b572ba558288592ed9
de2e25d217d28d1f360068048b5e4d54
bef9a0031387e0841166d41b047f8a13
fec2f286abc06554f68e5586a44662d5
03a18e5842e08a32d08703fe0c563687
e3211f650d932848a544d4da6f9fd599
1e6dca21cb0249525375e87358ff4fbc
4738ddef9cc4cd33dbbd616c722d5f46
97d87da8e4b22863681ef8eeef685826
C:/Users/benign_os/Desktop/malware_samples/3086/SMW3086/payloads/windows/qBitStealer/qBitStealer.go
f06c4a0af2181eb43a7b3763e8f5d5ea
C:/Users/lilia/Downloads/Telegram Desktop/qBitStealer/qBitStealer.go
b4247d41d89972d3a3cf34bca30c16f1
Samples will be shared via @abuse_ch Malware Bazar
The rules will be pushed to the 100DaysOfYARA and our detection repo :)
🍪
Malicious slack ad leading to #Pikabot malware ⚠️ Pikabot is closely associated with ransomware intrusions.
Redirection Infrastructure:
slalk.onelink[.]me
anewreseller[.]top
Fake Site:
siack.ovmv[.]net
.msi payload hosted on dropbox:
https://www.virustotal.com/gui/file/f1bc547091f9a2447fd16c804aa568707ca323e3d20c90e5568b303480ae7a03
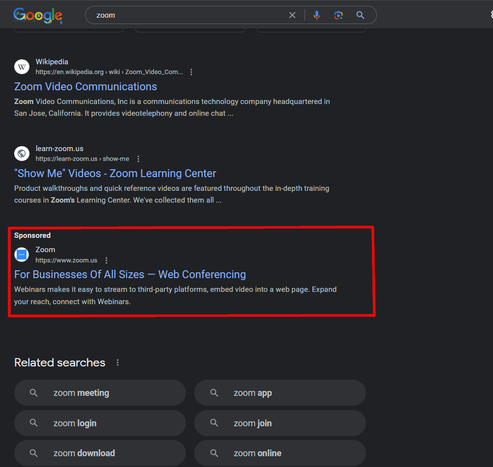
Malicious advertisement spoofing zooms website⚠️
Redirects the user to a fake site:
zoomus.onelink[.]me ->
zoonn.virtual-meetings.cn[.]com
Downloads .msix payload and launches it with ms-appinstaller:
ms-appinstaller:?source=https[:]//scheta[.]site/apps.store/ZoomInstaller.msix
Drops digitally signed malware "install.exe" (GlobalSign Code Signin)
Delivers #Batloader payload
#IOCs
🔗 https://www.virustotal.com/gui/file/462df2e4a633e57de0d5148060543576d7c1165bf90e6aec4183f430d8925a1c/
🔗 https://www.virustotal.com/gui/file/48aa2393ef590bab4ff2fd1e7d95af36e5b6911348d7674347626c9aaafa255e
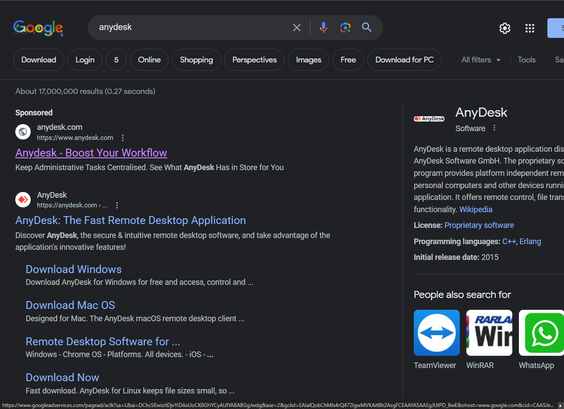
How can anyone reasonably expect a user to detect google ad abuse without visiting the malicious site?
Here's an example of a malicious google ad spoofing anydesk today.
This one redirects users to https[:]//anyowpdesk[.]com before downloading .msi malware:
https://www.virustotal.com/gui/file/9d85ae9e45556067d0b833144e7d9935936a3a3098fe65fc198409083a3a33a6/relations
Low detection #SolarMarker infostealer
C2: 91.206.178.106
C2: 193.29.56.179
Signed: "CHILL ANAESTHESIA LTD."
MB: https://bazaar.abuse.ch/sample/82600121c6678c2fc313d8e94031b65ac5ff0e0c1b5e0fac00410f222ca747ac
Backdoor: https://bazaar.abuse.ch/sample/511637bf26adb8ac42cec6f38da7cc25ceee118e4a5f09e61bfc39defbc97809/
New #SolarMarker malware! 🌞
Bing SEO poisoning -> fake website impersonating @internetarchive -> .exe malware (298.09 MB) -> walkymanki[.]com
#IOCs #Malware #CTI
https://www.virustotal.com/gui/file/7a8d7d470cf8980a25e25b5de5e121892304ed86b9ab66e39d323637402235e9
I used this script for extracting the C2 value from the sample: https://github.com/RussianPanda95/Configuration_extractors/blob/main/solarmarker_payload_extractor.py
#RaspberryRobin 🪱 (REF: https://blog.sekoia.io/raspberry-robins-botnet-second-life/)
'Clean' C2 domains:
/a7k.ro
/a5az.com
/v4a3.com
/4w.pm
/hlv1.com
/ubv5.com
/c43p.com
/2ipn.com
'Clean' compromised QNAP:
151.83.67.5
84.97.18.146
88.130.94.229
188.10.57.97
'New' exploited QNAP:
61.93.39.13
94.14.45.160
Monday Botnet 😍
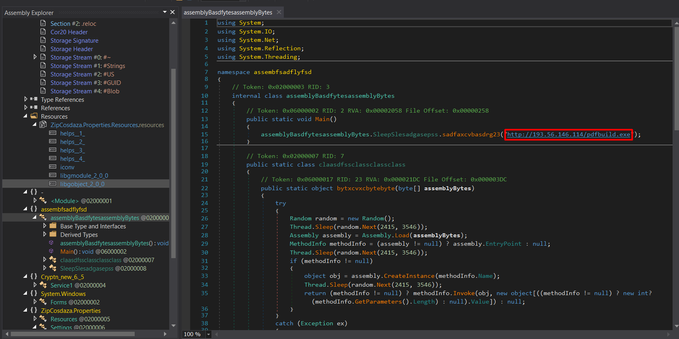
Current #payloads:
-ZipCosdaz.exe (#RedLine)
C2: 193.56.146.114:44271
Botnet: NewBuild
- ZipCosdaz1.exe (#Ursnif aka #Gozi)
C2 servers:
45.11.182.97
79.132.128.108
91.241.93.98
79.132.128.109
91.242.217.28
91.241.93.111
Botnet: 2503
- ConsoleDWS.exe (Destroy Windows 10 Spying)
GitHub repo: https://github.com/spinda/Destroy-Windows-10-Spying
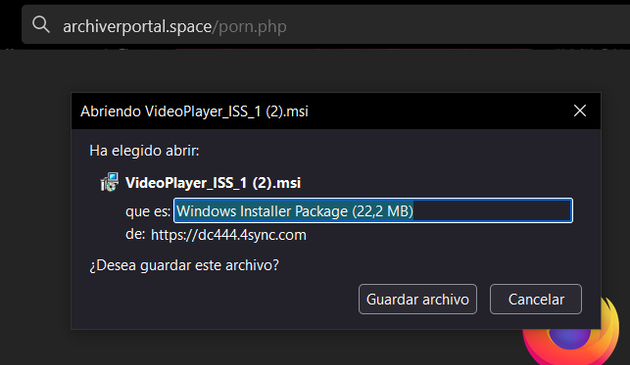
+ And another download URL: archiverportal[.]space/porn.php
@th3_protoCOL Interesting, the C2 endpoints are different from the ones I knew.
The flow of connections is:
http://archiverportal[.]space/start.php ↓
https://www[.]win-rar[.]com/fileadmin/winrar-versions/winrar/winrar-x64-611.exe ↓
https://raw[.]githubusercontent[.]com/swagkarna/Bypass-Tamper-Protection/main/NSudo.exe ↓
http://qtorrent[.]space/7z.zip (Payloads: ZipCosdaz.exe, ZipCosdaz1.exe and ConsoleDWS.exe) ↓
http://archiverportal[.]space/install.php
Unfortunately, the server with the payloads is now down ¬¬