We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: https://volatilityfoundation.org/announcing-the-official-parity-release-of-volatility-3/
DFIR / digital archaeologist / codez / vetz / hamz.
I'm an archaeologist who digs through digital dirt to find artifacts of battles with mercenaries fought within corporate empires. I often analyze fragments of rotting logs to reconstruct historical events.
"As long as you are green, you will grow; when you are ripe, you will rot" (4eva a n00b).
Laserkittens! Blockchain tacoz!
All my opinionz are belong to me (and are typically goofy).
#DFIR #BlueTeam #infosec #cybersecurity #ThreatIntel #TTPs #IOCs #ReverseEngineering #reversing #malware #MalwareAnalysis #ransomware #HamRadio #PrivacyLaw #privacy #hacking
#programming :: #python :python: && #golang :go: && #csharp && (begrudgingly) #cpp #cplusplus :cpp: && (learning) #rust #rustlang :rust:
I boosted several posts about this already, but since people keep asking if I've seen it....
MITRE has announced that its funding for the Common Vulnerabilities and Exposures (CVE) program and related programs, including the Common Weakness Enumeration Program, will expire on April 16. The CVE database is critical for anyone doing vulnerability management or security research, and for a whole lot of other uses. There isn't really anyone else left who does this, and it's typically been work that is paid for and supported by the US government, which is a major consumer of this information, btw.
I reached out to MITRE, and they confirmed it is for real. Here is the contract, which is through the Department of Homeland Security, and has been renewed annually on the 16th or 17th of April.
https://www.usaspending.gov/award/CONT_AWD_70RCSJ23FR0000015_7001_70RSAT20D00000001_7001
MITRE's CVE database is likely going offline tomorrow. They have told me that for now, historical CVE records will be available at GitHub, https://github.com/CVEProject
Yosry Barsoum, vice president and director at MITRE's Center for Securing the Homeland, said:
“On Wednesday, April 16, 2025, funding for MITRE to develop, operate, and modernize the Common Vulnerabilities and Exposures (CVE®) Program and related programs, such as the Common Weakness Enumeration (CWE™) Program, will expire. The government continues to make considerable efforts to support MITRE’s role in the program and MITRE remains committed to CVE as a global resource.”
Not every day you see snail mail paper extortion letters claiming to be #BianLian https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2025-03-04-group-likely-impersonating-BIanLian.md
TIL there are two ssh binaries in macOS: /usr/bin/ssh and /usr/libexec/ssh-apple-pkcs11 https://jamesd4.github.io/CVE-2023-42829/
VM escape. Patch ESXi. Now. https://doublepulsar.com/use-one-virtual-machine-to-own-them-all-active-exploitation-of-esxicape-0091ccc5bdfc
In the eternal quest for increased revenue, YouTube is introducing a feature where rich people can like videos more than poor people, and I am about to throw up.
It is called the hype button, and it is similar to the like button. But where likes are democratic, hypes are for pay, allowing rich kids to add as many hypes to videos as they can afford.
This is Elon’s enshittification of Twitter all over again.
Please criticize this feature and hit 👎 while it is free:
In the old #ASCII days, you could change a letter between upper and lower case by XORing its character code with 0x20. Of course, if you tried this with anything that wasn't a letter, you'd get nonsense results.
If you try that with #Unicode code points, it sometimes works, and sometimes doesn't. But Unicode can deliver much more impressive nonsense when it doesn't.
A fun example I just found: the "lower-case" version of CAR is NO PEDESTRIANS.
>>> chr(ord('🚗') ^ 0x20)
'🚷'
Was looking for a good Awesome list on Living Off the Land ( #LOL #LOtL ) tools/techniques. Found some helpful sites / repos but either nothing I could contribute to or it was limited.
So... I made one: https://github.com/danzek/awesome-lol-commonly-abused
Contributions welcome, whether by replying to this post or sending a PR on GitHub.
Interesting read: Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platforms https://gist.github.com/hackermondev/45a3cdfa52246f1d1201c1e8cdef6117
Americans think they're free because they have opinions;
but they don't get to have choices.
TrustWave did a great job of outlining the operations of Rockstar2FA, a phishing-as-a-service platform with the ability to capture second-factor authentication tokens, a few weeks ago. But just before their report went out, Rockstar did a stage dive: most of their back-end infrastrucure got disconnected from Cloudflare's CDN. Given that they had started hosting a whole bunch of their phishing portals on Cloudflare itself through the pages.dev service, that was not good for them; abusing Cloudflare is a key element of their operations.
While they've been floundering, we saw another phish service with very similar TTPs step up their operations. At least one researcher had been tracking this group as "FlowerStorm." It's clear from our analysis of their front-end stuff that FlowerStorm and Rockstar share at least a common ancestor, if they're not just outright stealing code from each other or are somehow connected.
FlowerStorm has some subtle differences in their operation. We've done an analysis of those in a blot I pushed out today with the help of Mark Parsons, Johua Rawles, Mark Parsons, Jordon Olness, and Colin Cowie. We're continuing to dig into Flowerstorm as they've made some OpSec boo-boos, but never stop your enemy when they're making a mistake.
Read the report here: https://news.sophos.com/en-us/2024/12/19/phishing-platform-rockstar-2fa-trips-and-flowerstorm-picks-up-the-pieces/
in switzerland you aren't allowed to have a train with exactly 256 axles because of an integer overflow in the axle counting machine
i wish i could fix my software bugs by making it illegal to cause them
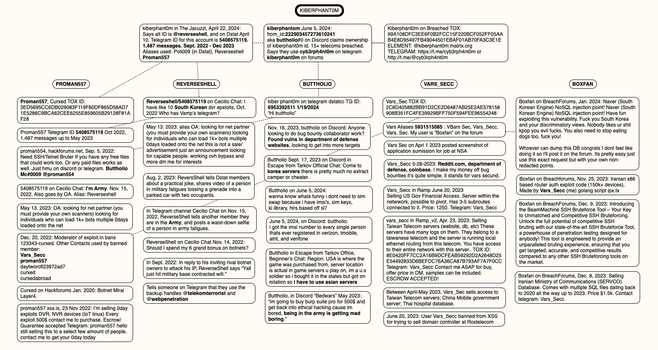
Might be my best sleuthing scoop this year (ah still 30+ days to go!):
Hacker in Snowflake Extortions May Be a U.S. Soldier
Two men have been arrested for allegedly stealing data from and extorting dozens of companies that used the cloud data storage company Snowflake, but a third suspect — a prolific hacker known as Kiberphant0m — remains at large and continues to publicly extort victims. However, this person’s identity may not remain a secret for long: A careful review of Kiberphant0m’s daily chats across multiple cybercrime personas suggests they are a U.S. Army soldier who is or was recently stationed in South Korea.
https://krebsonsecurity.com/2024/11/hacker-in-snowflake-extortions-may-be-a-u-s-soldier/
Novel (and clever) attack technique using an external org in physical proximity to the target org to join corporate WiFi since often RADIUS setups don’t require MFA for on-premises auth to WiFi. Dubbed “Nearest Neighbor Attack”: https://www.volexity.com/blog/2024/11/22/the-nearest-neighbor-attack-how-a-russian-apt-weaponized-nearby-wi-fi-networks-for-covert-access/
"CARTWHEEL" Tower, Fort Reno, Washington, DC, 2020.
All the top secret pixels at https://www.flickr.com/photos/mattblaze/49576247768/
So Python in Excel is here. As a data guy, this is simultaneously exciting and concerning. But I wanted to remind all the security folks that the Python code doesn't run locally. It runs in an ad-hoc Azure container whether you like it or not.
Python code used by Excel runs on the Microsoft Cloud with enterprise-level security as a compliant Microsoft 365 connected experience, just like OneDrive. The Python code runs in its own hypervisor isolated container using Azure Container Instances and secure, source-built packages from Anaconda through a secure software supply chain. Python in Excel keeps your data private by preventing the Python code from knowing who you are, and opening workbooks from the internet in further isolation within their own separate containers. Data from your workbooks can only be sent via the built-in xl() Python function, and the output of the Python code can only be returned as the result of the =PY() Excel function. The containers stay online as long as the workbook is open or until a timeout occurs. Your data does not persist in the Microsoft Cloud.techcommunity.microsoft.com/t5/excel-blog/python-in-excel-available-now/ba-p/4240212