Golang extravaganza in an exploratory video where we make example "malware" with hidden "secrets" and dig into it with different tools-- between Binja, IDA, GHIDRA, then Redress, GoReSym & finally obfuscate with garble. Then GoStringUngarbler and more! 🤪 https://youtu.be/gewnAzaZXQo
Hacker. Friends. Cybersecurity Researcher.
Big thanks to @KeeperSecurity for sponsoring this video and their continued support of the channel! Keeper PAM offers a solution for enterprise grade protection all in one unified platform -- keep your users, data, and environment secure with Keeper! https://jh.live/keeper-pam
I had a conversation with Pete Allor, a CVE Board member and Co-Chair of the CVE Vulnerability Conference and Events Working Group -- now helping put together The CVE Foundation (learn more at thecvefoundation[.]org) following the recent CVE conundrum: https://youtu.be/Ofy0LxkwkT8
HELLO NAHAMCON 2025 CTF IS MAY 23 TO MAY 25
BEN ASKED ME TO HELP PROMOTE AND I FORRGOOTTT
PLEASE REGISTER AND PLAY OUR GAME
https://ctf.nahamcon.com
I WILL CONTINUE TO SPAM UNTIL SHOWTIME AND DURING EVENT SORRY BUT IT WILL BE FUN I PINKY PROMISE
Reading up on "Gremlin Stealer," allegedly a new infostealer malware variant described by Unit 42 -- and snooping around ye ol' cheesy dark web to see what cybercrime kiddos are talking about it 🥴 https://youtu.be/t7vBdvfBG-Q
Big thanks to @FlareSystems for sponsoring this video and their continued support of the channel! Track data on the dark web and manage threat intelligence for your exposed attack surface with Flare -- try a free trial and see what info is out there: https://jh.live/flare
Password palooza in a scrappy showcase of DPAPI fundamentals! With a simple PowerShell demo to start and then some Mimikatz fun to dump my own Brave browser passwords -- love to SharpDPAPI, dploot, and other tools MITRE ATT&CK says the baddies are using 👀 https://youtu.be/Wf520OJDzfs
Big BIG thanks to @specopssoftware for sponsoring this video and their continued support of the channel! Protect your organization with stronger passwords, and continuously scan and block over FOUR BILLION breached passwords with SpecOps Software! https://jh.live/specops
Reading recap of the phish that got Troy Hunt, the owner of the "Have I Been Pwned?" database and service -- and a focus on how anyone can be compromised, cybersecurity folks are no exception -- myself included: https://youtu.be/pJ1UQsW0EqQ
Big thanks to @PowerDMARC for sponsoring this video! Stop email spoofing and phishing threats, improve email deliverability, and protect your domain reputation with PowerDMARC! Get started with a 15-day free trial: https://jh.live/powerdmarc
hey check out my new DUMB ‼️ video where I write STUPID 👏 PowerShell code to block BAD 🤬 living off the land binaries outbound NETWORK 🌐 connections with the LOCAL 😤 Windows Firewall and make MANY 👿 mistakes because i am DUMB 🔥🚀 ETCETERA ETCETERA 🫡 https://youtu.be/x7L-F4yDXvI
Big thanks to @DropzoneAI for sponsoring this video! Try COACH from Dropzone AI and get a free AI-powered security alert mentor for SOC analysts! https://jh.live/dropzone-ai-coach
I got a chance to try out @Burp_Suite Burp AI, and it's... honestly really cool 😅 Video showcase where we cruise through a web app scan, crawl and audit, and it rips through findings including an explicit UNION SQL injection vulnerability and more 🤩 https://youtu.be/v-McepNOrTQ
Needless to say, big thanks to our channel partner @PortSwigger for sponsoring this video! Hunt for bugs and perform web app pentests with Burp AI -- an AI assistant not meant to replace human effort, but augment your workflow 😎 https://jh.live/burpai
Big big thanks to @PlexTrac for sponsoring this video and their continued support of the channel! Save time and effort on pentest reports with PlexTrac's premiere reporting & collaborative platform: https://jh.live/plextrac-408 😎
I Backdoored Cursor AI 😎 https://youtu.be/FYok3diZY78 Finally getting a chance to play with Loki C2, the super cool Node JS C2 framework for backdooring Electron applications (think Discord, Slack, too!) -- put together by the incredible @0xBoku 🔥We even got to nerd out over DMs to add a new feature, keeping the target app alive and adding persistence! 🤩
An MP3 file as malware!?! Actually an HTA polyglot -- with some clever error handling tricks, slick PowerShell sub sessions, and an annoyingly obfuscated C# .NET assembly across like seven stages of payloads. The song has a good beat, too! https://youtu.be/25NvCdFSkA4
PS, big thanks to @TrustVanta for sponsoring this video! Automate and prove your security compliance with Vanta! Get $1,000 off with my link to cruise through compliance across SOC 2, ISO 27001, ISO 42001, NIST AI RMF, HIPAA, GDPR, and more! https://jh.live/vanta
The 9.1 CVSS CVE-2025-29927 authentication bypass vulnerability in Next.js middleware -- covered in a rambling video and teeny tiny demo showcase,
✨ V I B E C O D I N G✨ a vulnerable proof-of-concept app. https://youtu.be/dL1a0KcAW3Y
Big props to @zhero___ and @inzo____ for their research and writeup! Of course all credit where credit is due, their blog post on it: https://zhero-web-sec.github.io/research-and-things/nextjs-and-the-corrupt-middleware
And all credit where credit is due, kudos to @cxnturi0n for building and publishing the convoC2 tool!
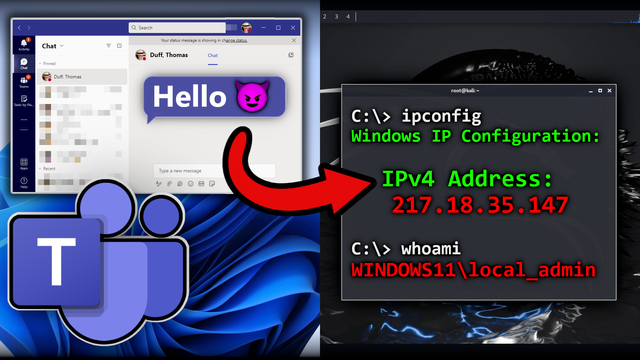
MS Teams as a C2! Command and control with "convoC2," a sweet utility that smuggles in commands to run within hidden HTML span tags in Teams messages and a client agent that parses and executes them from the Teams message logs 😱 Video showcase: https://youtu.be/FqZIm6vP7XM
Big thanks to @PlexTrac for sponsoring this video and their continued support of the channel! Save time and effort on pentest reports with PlexTrac's premiere reporting & collaborative platform: https://jh.live/plextrac-318 😎
I took the TryHackMe Security Analyst Level 1 certification exam! Video is literally me going through it and discussing it fresh at each break 😅 Honestly very cool training, the SOC Simulator makes it really real-world & practical -- review and showcase: https://youtu.be/AIPbFFJgD4o