The Bumblebee SEO poisoning campaign uncovered earlier this week abusing the RVTools brand is using more typosquatting domains mimicking other popular open-source projects.
Recovering Threat Intel addict. Came for the Intel, stayed for the memes.
Looking for a daily dose of Cyber News? 👉🏻 opalsec.io
EscapeTwo from HackTheBox is a Windows box with MSSQL, some AD, and ESC4.
NEW by @lorenzofb: A mysterious government hacking group called "Careto" (aka "The Mask") was once one of the "most advanced threats" of its time, but was never publicly linked to a specific government.
Researchers privately concluded that Careto was working for the Spanish government.
I made this point a few weeks ago, but... outsourcing all your IT, Networks, Service Desk (helpdesk) and operational cybersecurity is a temporary cost saving and basically paints a ticking timebomb on the org, IMHO.
A proof-of-concept exploit has been publicly released for a maximum severity Apache Parquet vulnerability, tracked as CVE-2025-30065, making it easy to find vulnerable servers.
Despite misleading marketing, Israeli company TeleMessage, used by Trump officials, can access plaintext chat logs. My findings are based on TM SGNL's source code, and they are corroborated by hacked data https://micahflee.com/despite-misleading-marketing-israeli-company-telemessage-used-by-trump-officials-can-access-plaintext-chat-logs/
A supply chain attack involving 21 backdoored Magento extensions has compromised between 500 and 1,000 e-commerce stores, including one belonging to a $40 billion multinational.
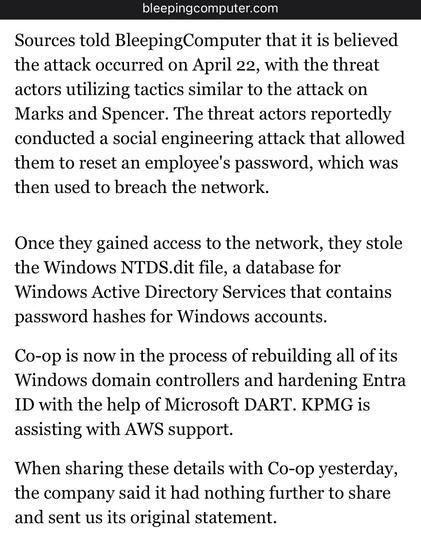
Bleeping Computer have more on the Co-op breach https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
I’m going to say this slowly.
If Andrew Tate & his ilk were right about ANYTHING they’d have no audience.
Guys would listen briefly, apply advice, & be WAY too busy with their new gfs, side-pieces, & high income hustles to bother tuning in.
It’s the Tinder principle: if you’re happy, they lose a customer.
Their business model is your unending misery.
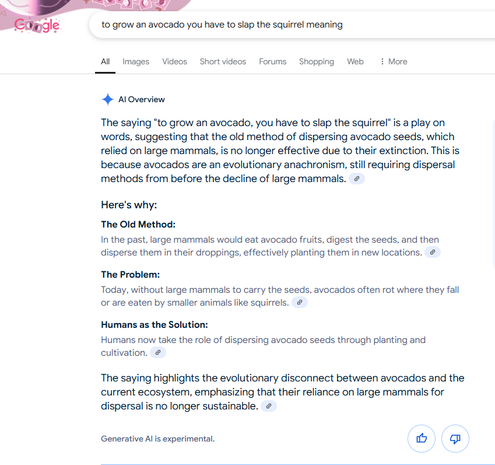
Oh gosh, it's true, you really can enter a completely nonsense phrase into Google, ask for its meaning, and lo and behold, Google's AI will make shit up.
So if you've ever wondered what "to grow an avocado, you have to slap the squirrel" means, now you know.
@wdormann these types of error messages that require you to navigate multiple rabbit holes to translate make me want to turn off all my computers and walk slowly into the ocean
In a recent espionage campaign, the infamous North Korean threat group Lazarus targeted multiple organizations in the software, IT, finance, and telecommunications sectors in South Korea.
EFF’s Sophia Cope joined Australia’s ABC News radio to discuss how people around the globe are rethinking their travel plans to the United States, and how you can protect your digital privacy if you’re coming. https://www.abc.net.au/listen/programs/the-radio-national-hour/reports-of-surge-in-phone-checks-at-the-us-border/105214062
Russian threat actors have been abusing legitimate OAuth 2.0 authentication workflows to hijack Microsoft 365 accounts of employees of organizations related to Ukraine and human rights.
as is tradition, I just published my commentary on this year's Verizon Data Breach Investigations Report (aka #DBIR): https://kellyshortridge.com/blog/posts/shortridge-makes-sense-of-verizon-dbir-2025/
In the post, I include the following sections covering what I felt were the most notable insights and facets in the report:
🌍 So, what?
💃 Espionage: fast fashion or couture?
👻 APTs go BWAA-haha >:3
💸 How do the money crimes generate money?
🤖 Attackers are still not really using GenAI
👩🍳 If you can’t make your own 0day, store-bought creds are fine
🔓 #Security was the real supply chain threat all along
🍄 Things Rot Apart
🕵 Scooby Doo's Spooky Kooky Corporate IT Caper
🌈 At least some things are improving somewhere
Go forth and enjoy my commentary, and then make sure to find me at #RSAC to tell me what you loved or hated Tuesday 14:30 at the @fastlydevs booth (where you'll also get a free copy of my book ✨)
thanks @alexcpsec for the early copy <3
With Chinese diplomats reportedly admitting to targeting US Critical Infrastructure as a "warning to the U.S. about Taiwan" and some in the industry war-gaming the possibility of Cyber Effects being used to sway the Trade dispute between the US and China, now seemed a good time to do a reality check on how - if at all - China would do so.
The bottom line - expect a surge in cyber espionage and signaling campaigns targeting US telcos and leadership to provide the CCP a competitive advantage in negotiations and their backdoor dealings.🕵️
Cyber Security doesn't operate in a vacuum - here's a good example of where geopolitics starts to seep in at the edges: https://opalsec.io/is-cyber-a-legitimate-weapon-in-a-tariff-war/
#CyberSecurity #InfoSec #ThreatIntel #China #USChinaTradeWar #Geopolitics #CyberWarfare #CriticalInfrastructure #VoltTyphoon #SaltTyphoon #NationalSecurity #CyberThreats #RiskManagement #GeopoliticalRisk #CyberPolicy #CISA
Cyber Security Policy is markedly different under the Trump administration, to say the least.
Expert warnings mount as key US cyber agencies face staff cuts, leadership shakeups, and even retaliatory actions against private partners - namely those made in the last 24 hours, targeting former CISA Director, Chris Krebs.
Recent White House actions suggest a troubling shift away from expert-driven cyber defense towards political expediency. From sidelined Russia operations to gutted agencies, we examine the evidence and the potential global fallout.
Read our full analysis here: https://opalsec.io/eroding-foundations-the-precarious-state-of-us-cyber-leadership/
#CyberSecurity #NationalSecurity #USPolitics #Geopolitics #ThreatIntel #PolicyAnalysis #CyberRisk #Leadership #CISA #NSA
Biggest commitment to a 3 second joke I've ever seen
Our latest post is out, check it out for the full details here 👉 https://opalsec.io/daily-news-update-saturday-april-5-2025-australia-melbourne/
If you're short on time, here's a quick rundown of the key stories:
🇦🇺 Australian Pension Funds Under Attack: A significant credential stuffing campaign hit multiple Aussie superannuation funds (Australian Super, REST, Hostplus, Insignia, ART) over the March 29-30 weekend. Attackers used stolen creds, likely targeting web portals and mobile apps, accessing accounts and unfortunately stealing funds in some cases (reports mention ~AU$500k from four Australian Super members alone). ASFA is coordinating the response. A stark reminder about password reuse and MFA effectiveness, especially during off-hours!
🏛️ Shake-up at NSA/Cyber Command: Big news out of the US – Gen. Timothy Haugh has been fired from his dual-hat role leading the NSA and USCYBERCOM after just over a year. Deputy Director Wendy Noble is also reportedly out. Reasons are murky, but speculation points towards political motivations (linked to Laura Loomer's visit with President Trump). This raises questions about stability, the ongoing 'Cybercom 2.0' review, and the future of the dual-hat structure, especially with ongoing nation-state threats.
⏱️ Incident Response Speed vs. Backups: An interesting debate highlighted recently – while backups are vital for recovery, is rapid IR potentially even more critical? It’s a tough balancing act: contain fast (risking tipping off attackers/losing evidence) or investigate thoroughly while the breach continues? Emphasises the need for skilled responders and adequate tooling, not just relying on backups as a silver bullet.
⚠️ Critical RCE in Apache Parquet (CVE-2025-30065): Heads up, data folks! A CVSS 10.0 RCE vulnerability has been found in the widely used Apache Parquet columnar storage format (up to v1.15.0). Given its use in Hadoop, AWS, Azure, GCP, and by major tech companies, the potential impact is huge. Patch to version 1.15.1 ASAP!
📱 Pentagon Probes Defense Secretary's Signal Use: The DoD's Inspector General is investigating Defense Secretary Pete Hegseth's use of Signal for official business. This follows a report where a journalist was accidentally added to a Signal chat discussing sensitive airstrike details (targets, timing). Raises concerns about classified info on unclassified apps, need-to-know, and record-keeping compliance.
The full blog post dives deeper into each of these stories and much more. Don't forget to sign up to our newsletter so you can get this daily wrap-up straight to your inbox!
📨 https://opalsec.io/daily-news-update-saturday-april-5-2025-australia-melbourne/#/portal/signup
What are your biggest takeaways from this week's news? Let's discuss below!
#CyberSecurity #InfoSec #ThreatIntel #DataBreach #CredentialStuffing #Ransomware #Phishing #Vulnerability #ApacheParquet #NSA #CyberCommand #IncidentResponse #CloudSecurity #NationalSecurity #Espionage #Privacy
@grey Disappointing to hear it looked like AI garbage to you - I spent over an hour curating and publishing the article and social media posts.
Sorry to disappoint, but hey, if you still wanted those lyrics: https://letmegooglethat.com/?q=lyrics+to+rick+astley%27s+never+gonna+give+you+up