Our latest @rapid7 analysis details Critical CVEs in Outdated Versions of Atlassian Confluence and VMware vCenter Server https://www.rapid7.com/blog/post/2024/01/19/etr-critical-cves-in-outdated-versions-of-atlassian-confluence-and-vmware-vcenter-server/
Chief Scientist at Rapid7 (ex McAfee) | Cloud Security Alliance - Chief Innovation Officer | Co-author of Smart Grid Cyber Book & CSA Guide to Cloud | Advisor Europol European Cybercrime Centre (EC3)
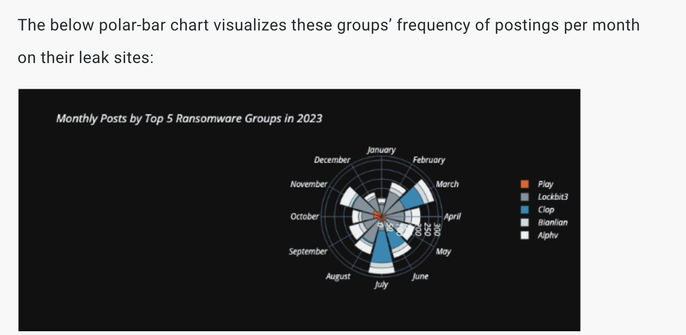
Our latest Rapid7 Labs publication details an assessment of the hashtag#ransomware landscape detailing the most common threat groups and the common patterns and methodologies observed in the majority of ransomware attacks.: https://www.rapid7.com/blog/post/2024/01/12/2023-ransomware-stats-a-look-back-to-plan-ahead/ #infosec #cybersecurity H/T @ChristiaanB
We are hiring! Great opportunity to join the vulnerability and exploit research team. More details here: https://careers.rapid7.com/jobs/lead-security-researcher-united-states #infosec #infosecjobs
@theomegabit nice to meet you. We have a lot of the team here who are posting and also @metasploit posts much of our content.
Our latest @rapid7analysis details CVE-2023-47426, a zero-day path traversal vulnerability affecting on-premise SysAid servers. Including IoCs and @velocidex
artifact: https://www.rapid7.com/blog/post/2023/11/09/etr-cve-2023-47246-sysaid-zero-day-vulnerability-exploited-by-lace-tempest/ #infosec
Our latest @rapid7 advisory details CVE-2023-20198: Active Exploitation of Cisco IOS XE Zero-Day Vulnerability - IoCs and observed attacker behaviour included; https://www.rapid7.com/blog/post/2023/10/17/etr-cve-2023-20198-active-exploitation-of-cisco-ios-xe-zero-day-vulnerability/
We have now posted our @rapid7 analysis into CVE-2023-40044, a .NET deserialization vulnerability affecting the Ad Hoc Transfer module of WS_FTP Server. Now available on @AttackerKb https://attackerkb.com/topics/bn32f9sNax/cve-2023-40044/rapid7-analysis
We are seeing multiple instances of WS_FTP exploitation in the wild. Further details of this and the vulnerabilities in the advisory, two of which are critical (CVE-2023-40044 and CVE-2023-42657) available in our
Rapid7 advisory: https://www.rapid7.com/blog/post/2023/09/29/etr-critical-vulnerabilities-in-ws_ftp-server/
Our latest @rapid7 advisory details CVE-2023-42793: Critical Authentication Bypass in JetBrains TeamCity CI/CD Servers. More details here https://www.rapid7.com/blog/post/2023/09/25/etr-cve-2023-42793-critical-authentication-bypass-in-jetbrains-teamcity-ci-cd-servers/
Our latest @rapid7 analysis details a new loader to execute infostealers on compromised systems including StealC and Lumma. More details including IoCs available here https://www.rapid7.com/blog/post/2023/08/31/fake-update-utilizes-new-idat-loader-to-execute-stealc-and-lumma-infostealers/?utm_campaign=sm-EA&utm_source=linkedin&utm_medium=organic-social #infosec #malware
Our latest Rapid7 analysis details observed Exploitation of Cisco ASA SSL VPNs, further details including IoCs located here: https://www.rapid7.com/blog/post/2023/08/29/under-siege-rapid7-observed-exploitation-of-cisco-asa-ssl-vpns/
Our @metasploit weekly wrap up details two new exploit modules leveraging CVE-2023-34960 Chamilo versions 1.11.18 and below and CVE-2023-26469 in Jorani 1.0.0 - more details here: https://www.rapid7.com/blog/post/2023/08/25/metasploit-weekly-wrap-up-24/ #infosec
Our latest research analyses a dozen medical infusion pumps available for purchase on the secondary market, and how these were not properly decommissioned before being sold: https://www.rapid7.com/blog/post/2023/08/02/security-implications-improper-deacquisition-medical-infusion-pumps/ #infosec
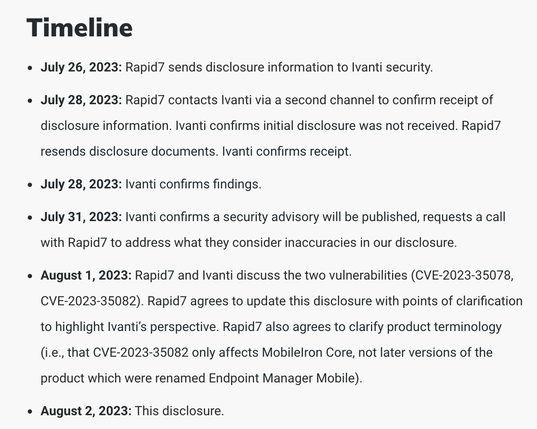
Our latest analysis details CVE-2023-35082, a new vulnerability that allows unauthenticated attackers to access the API in older unsupported versions of MobileIron Core (11.2 and below). https://www.rapid7.com/blog/post/2023/08/02/cve-2023-35082-mobileiron-core-unauthenticated-api-access-vulnerability/ #infosec #cybersecurity
ICYMI We recently released @velocidex Artifact that "enables scoping EventLogs from Progress Software’s MoveIT File Transfer. It is designed to assist in identifying exfiltration resulting from the exploitation of CVE-2023-34362" https://docs.velociraptor.app/exchange/artifacts/pages/moveitevtx/
Further details on CVE-2023-2868: Total Compromise of Physical Barracuda ESG Appliances - note we have identified malicious activity that took place as far back as November 2022: https://www.rapid7.com/blog/post/2023/06/08/etr-cve-2023-2868-total-compromise-of-physical-barracuda-esg-appliances/ #cybersecurity #înfosec
New Velociraptor artifact now available that "enables scoping EventLogs from Progress Software’s MoveIT File Transfer. It is designed to assist in identifying exfiltration resulting from the exploitation of CVE-2023-34362" https://docs.velociraptor.app/exchange/artifacts/pages/moveitevtx/ #DFIR #Infosec #cybersecurity
We are hiring! We are looking for a Senior Manager driving communications within our @rapid7 Labs team.
More details here: https://careers.rapid7.com/jobs/senior-manager-rapid7-labs-threat-communications-boston-ma-united-states #infosecjobs #infosec
Technical analysis detailing CVE-2023-25690 in Apache HTTP Server 2.4.56 now available in AttackerKb - Its CVSS base score is 9.8, as this can theoretically bypass access controls https://attackerkb.com/topics/0Uka1VHsPO/cve-2023-25690/rapid7-analysis
We are hiring! Great opportunity to join the @rapid7 Labs team as a software engineer - more details here: https://careers.rapid7.com/jobs/software-engineer-i-security-sciences-belfast-united-kingdom #infosecjobs