Privacy Security Anonymity Obfuscation, UK Surveillance Database State PGP/GPG 0x2297B6D37E9B350F I had levyr a letter be brent then lost ne forte videant Romani
Hoping that @SpyBlog can continue on Twitter without being location tracked.
Already [self] #censored because of the new anti-#Mastodon links policy.
N.B. Unlikely to follow you back until you have posted or boosted something.
I've read a lot online about how "Y2K was overblown". As an engineer who worked like crazy in 1999 to correct our systems this drives me crazy.
Today I read about games going offline, watches getting frozen and airline tickets showing the wrong date.
Because of a leap year. Which happens every FOUR years (give or take).
Yeah Y2K was a one time thing. (Well at least until year 10000)
Isn't 2038 going to be fun.
CryptoParties are back in London! #CryptoPartyLDN
After a three-year hiatus, we’ll have a small #CryptoParty at our usual spot at Juju’s Bar and Stage in Spitalfields, East End of London. Join us on Tuesday, 19th of December from 6pm to chat about digital privacy.
Tuesday 19th December 2023: Informal #CryptoParty #CryptoPartyLondon re-launch at Juju's
https://www.cryptoparty.in/london
N.B. COVID-19 and new strains of influenza are still around this winter, so please get vaccinated if you are vulnerable, wash your hands and wear a mask on public transport or in crowds.
Tuesday 19th December 2023 6:00pm till late
JuJu's Bar and Stage
15 Hanbury St, London, E1 6QR
https://www.jujusbarandstage.com/about/
Free entrance, all welcome, no registration needed. N.B. licensed premises
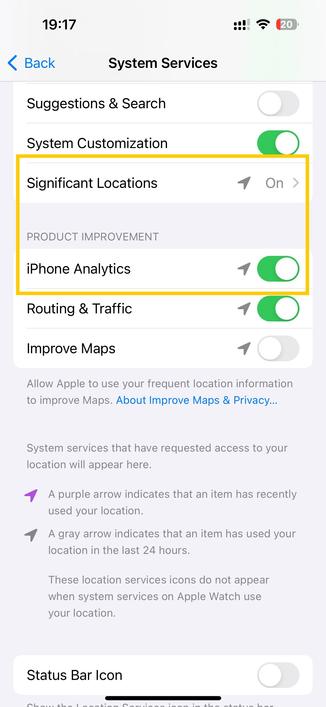
🚨PSA: iOS 17 turns these sensitive location options back on. If you have disabled significant locations as well as adding your location information to your iPhone analytics before upgrading to iOS 17, #iOS17 will turn the options on as shown in the screenshot.
While significant locations remain local on your #iPhone, they can be abused as they record detailed information about the locations you visit frequently. iPhone analytics, on the other hand, are shared with #Apple. Having your location information included in these analytics reports might have privacy implications, even if the reports don't identify you.
Security experts have always advised to turn these two options off.
Go the Settings app: Privacy & Security ➡️ Location Services ➡️ Scroll down to System Services ➡️ Find these two options and turn them off:
👉 Significant Locations
👉 iPhone Analytics
A re-post or boost would be appreciated to spread the word🙏
You're welcome!
"What's the biggest pitfall a pentester can make?"
Ever wonder how a pentest turns into felony charges? Coalfire duo explain Iowa courthouse arrest debacle
Get. The. Terms. Of. The. Audit. In. Writing
https://www.theregister.com/2020/08/05/coalfire_pentest_iowa_black_hat/
New #TunnelCrack flaw can break a large majority of VPNs: we can trick a VPN into leaking traffic outside the protected VPN tunnel. Our tests indicate that this is a widespread design issue. For a demo, more details, and the USENIX Security paper, see https://tunnelcrack.mathyvanhoef.com
Hi, we are BBC News Labs #introduction
We’re charged with driving innovation for BBC News. Our team of technologists and journalists explore how new tools and formats affect how news is found and reported.
You can find out more at https://bbcnewslabs.co.uk/ and we’ll be posting here about our work
This account is part of an experiment from BBC R&D in establishing a BBC presence in the Fediverse.
This account is part of an experiment from BBC R&D in establishing a BBC presence in the Fediverse. You can read more about this experiment at https://www.bbc.co.uk/rd/blog/2023-07-mastodon-distributed-decentralised-fediverse-activitypub
Friends, I've just activated accounts for two big BBC radio brands on here - @BBCRadio4 and @BBC5Live. It's part of an experiment that @tristanf and @BBCRD colleagues are running. We want to learn more about publishing, management, governance etc. in a fediverse/ActivityPub world. Follow and let us know what you'd like to see from the Beeb in the fediverse
#OpSec Wot no taxi nor "anonymous" Uber etc. to a destination not exactly to, but plausibly deniably within walking distance of your destination ?
N.B. sometimes even an anonymous drop off to a remote area gives the game away.
Mistake 1: Recursive 2FA Loop
I use a cool app called @ente@mstdn.social Auth as my authenticator, which requires email verification to log in. The problem was that I used my regular email for my Auth account, which has 2FA enabled. So, if I couldn't log in to Ente Auth, I couldn't access my email, and without email access, I couldn't log in to Ente Auth. It was a frustrating loop!
Mistake 2: Forgotten Phone Password
I recently visited a relative and took a break from carrying multiple devices. On Saturday (June 3), I decided to make my phone password stronger by adding a 4-digit code after my previous password. However, I never imagined I would forget the code within 72 hours. Unfortunately, my Samsung phone requires the password every 72 hours, even with biometrics enabled.
The real trouble began when I couldn't remember the password correctly. Since I had no other devices with me, I lost access to everything instantly. I couldn't access Ente Auth or my password managers. I tried more than 85 different passwords, but none worked on my phone.
In desperation, I reached out to the Ente.io Team through their Matrix channel. At first, I thought they had to disable email verification for me. But Vishnu came to the rescue and shared the verification code sent to my email via Matrix. That allowed me to successfully log in. The first thing I did was change the email to break the 2FA loop.
Today, I finally wiped all the data from my phone and regained access to my other devices. Luckily, I had regularly backed up my secret keys, like SSH.
I'm really sorry for everything that happened in the last 5-6 days. To prevent such situations in the future, I will appoint a new administrator to help maintain NixOrigin. If any of you are interested, please let me know.
Thanks a bunch! 😊
#OpSec #FediAdmin #nixorigin #neo #mitexleo #PixelfedAdmin #Pixelfed
"I put the shotgun in an Adidas bag and padded it out with four pairs of tennis socks, not my style at all, but that was what I was aiming for. If they think you're crude, go technical; if they think you’re technical, go crude. I’m a very technical boy. So I decided to get as crude as possible. These days, though, you have to be pretty technical before you can even aspire to crudeness."
William Gibson
Johnny Mnemonic’ (1981)
Here’s how I used AI to clone a 60 Minutes correspondent’s voice to trick a colleague into handing over Sharyn's passport number. I cloned Sharyn’s voice then manipulated the caller ID to show Sharyn’s name on the caller ID with a spoofing tool.
The hack took 5 minutes total for me to steal the sensitive information.
So, how do we protect ourselves, our loved ones, and our organizations?
1. Make sure the people around you know that caller ID is easily faked (spoofed) and that voices can also be easily impersonated.
2. If they receive a dire call from “you”, verify it’s really you with another method of communication (text, DM, FT, call, etc) before taking an action (like sending money). Kind of like human MFA.
Some suggest setting up a secret “verification word” with their folks ones so that if someone impersonates & demands money/access etc you can ask for the verification word to see if it’s a real crisis. This won’t work for all people but could work for some. If it’s a match, use it.
In general, I recommend keeping advice simple: if premise of call is dire use a 2nd method of communication to confirm a person is in trouble before taking action (like wiring money or sensitive data). Rapid text, email, DM, have others message repeatedly — before wiring money.
Bottom line is:
Scammers use urgency & fear to convince victims to take actions (like sending money, data, etc).
If premise of a call, text, email, or DM is too dire (or too good to be true), that’s a likely scam.
Use a 2nd method of communication to check it’s real before taking action!
The transition to post-quantum key exchanges has begun for Signal.
Some code based on Crystals-Kyber post-quantum key exchange from the ongoing NIST standardization is now part of Signal.
Apparently, Signal's Diffie-Hellman ratchet already provides some protection against quantum computers, but the developers wanted to harden the code for a post-quantum world.
https://github.com/signalapp/libsignal/commit/ff09619432e19e96231ebed913fe4433f26ee0d2
@SpyBlog Airtags periodically send out unsolicited bluetooth beacons, which are picked up by any i-device in range. I don't think they use UWB.
The effect is that while the power is low, a receiver is also likely to very nearby (possibly only a foot or so away). So the level of shielding needed to reliably isolate them is comparable to that of a cellphone.
Does an Apple #Airtag rely primarily on #Bluetooth to periodically beacon its unique identifiers or does it also passively transmit on the shorter range but harder to jam, multi frequency, #UltraWideBand ?
Or does it only do so in response to an iPhone initiated Find Me active scanning request ?
What if the "tracking device attached to the bumper" is *not* a powerful cell phone transmitter (with an obviously limited battery life, unless somehow wired in to the vehicle's electrical system ) but a low powered Apple #AirTag ?
This might track the vehicle for months, relying on the network of millions IPhones to track it cooperatively ?
How much foil etc. is needed to isolate an AirTag which uses #Bluteooth and the harder to block #UltraWideBand ?
https://screenrant.com/apple-airtag-precision-finding-how-block/
Short answer: It's hard, and things that looked great often worked poorly. The best was a single layer of foil, carefully folded sealed around the edges. But several other students built impressive looking foil containers that didn't work at all).
None of the cookie tins worked.
A very substantial-looking pressure cooker appeared to actually amplify the signal.