CAN Injection : keyless car theft : https://kentindell.github.io/2023/04/03/can-injection/ credits @kentindell @mintynet
Linux Evangelist, Malwares, Kernel dev, Security Enthusiast , Sarcasm , Rebel , Reformist , Philanthropist , Jain , Meditation .
binitamshah at protonmail com
Grounded-Segment-Anything : Marrying Grounding DINO with Segment Anything & Stable Diffusion & BLIP & Whisper - Automatically Detect , Segment and Generate Anything with Image, Text, and Speech Inputs : https://github.com/IDEA-Research/Grounded-Segment-Anything
Pwning Pixel 6 with a leftover patch : https://github.blog/2023-04-06-pwning-pixel-6-with-a-leftover-patch/
A simple IPTV player in bash with M3U playlists support (with fuzzy finding, right in your terminal) : https://github.com/shahin8r/iptv
Reverse-engineering the division microcode in the Intel 8086 processor : http://www.righto.com/2023/04/reverse-engineering-8086-divide-microcode.html credits @kenshirriff
Hijacking Arch Linux Packages by Repo Jacking GitHub Repositories : https://blog.nietaanraken.nl/posts/aur-packages-github-repo-jacking/
Ref : Hijacking GitHub Repositories by Deleting and Restoring Them : https://blog.nietaanraken.nl/posts/gitub-popular-repository-namespace-retirement-bypass/
64 Methods For Executing Mimikatz : https://redteamrecipe.com/64-Methods-For-Execute-Mimikatz/ credits @Hadess_security (twitter)
Hacking Ham Radio: WinAPRS – Part 1 : https://www.coalfire.com/the-coalfire-blog/hacking-ham-radio-winaprs-part1
Part 2 : https://www.coalfire.com/the-coalfire-blog/hacking-ham-radio-winaprs-part-2
Part 3 : https://www.coalfire.com/the-coalfire-blog/hacking-ham-radio-winaprs-part-3
Part 4 : https://www.coalfire.com/the-coalfire-blog/hacking-ham-radio-winaprs-part-4
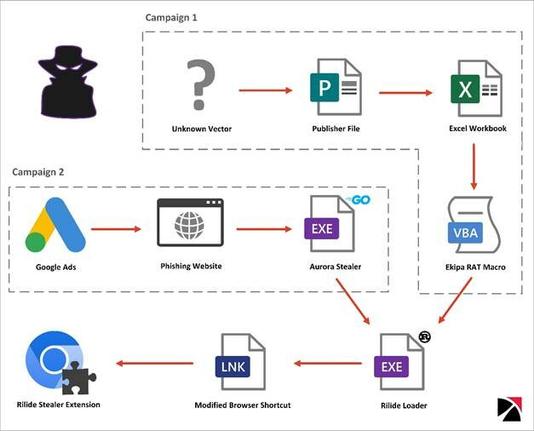
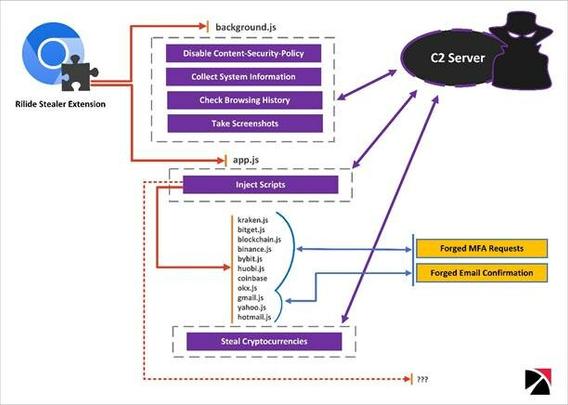
Rilide: A New Malicious Browser Extension for Stealing Cryptocurrencies : https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/rilide-a-new-malicious-browser-extension-for-stealing-cryptocurrencies/
Scilla : Information Gathering tool - DNS / Subdomains / Ports / Directories enumeration : https://github.com/edoardottt/scilla credits @edoardottt2 (twiiter)
cariddi : Take a list of domains, crawl urls and scan for endpoints, secrets, api keys, file extensions, tokens and more : https://github.com/edoardottt/cariddi credits @edoardottt2 (twiitter)
Awesome Hacker Search Engines : https://github.com/edoardottt/awesome-hacker-search-engines credits @edoardottt2 (twitter)
In-Memory Disassembly for EDR/AV Unhooking : https://www.signal-labs.com/blog/analysis-of-edr-hooks-bypasses-amp-our-rust-sample @credits @Kharosx0
XSS-Payloads : List of XSS Vectors/Payloads : https://github.com/RenwaX23/XSS-Payloads
Introducing — LOLDrivers.io : a curated list of Windows drivers used by adversaries to bypass security controls and carry out attacks : https://www.loldrivers.io/
More : https://haggis-m.medium.com/living-off-the-land-drivers-a5d74d45e77a credits @M_haggis
I built a Zero Day with undetectable exfiltration using only ChatGPT : https://www.forcepoint.com/blog/x-labs/zero-day-exfiltration-using-chatgpt-prompts
x86 Assembly demystified (3 Parts video series as of now) : https://www.youtube.com/playlist?list=PLs-lxQfNn-H3n9TghY02njSFYdBvf_Sea
Part 1 : https://www.youtube.com/watch?v=ZXoW5iqbFJE&list=PLs-lxQfNn-H3n9TghY02njSFYdBvf_Sea&index=1
Part 2 : https://www.youtube.com/watch?v=d-zxyLQlaYw&list=PLs-lxQfNn-H3n9TghY02njSFYdBvf_Sea&index=2
Part 3 : https://www.youtube.com/watch?v=g-8Vk7Jik9o&list=PLs-lxQfNn-H3n9TghY02njSFYdBvf_Sea&index=3 credits @jeFF0Falltrades (twitter)
Breaking Pedersen Hashes in Practice : https://research.nccgroup.com/2023/03/22/breaking-pedersen-hashes-in-practice/
InjectGPT: remote code execution by asking nicely (literally) : https://blog.luitjes.it/posts/injectgpt-most-polite-exploit-ever/
Google finds more Android, iOS zero-days used to install spyware : https://blog.google/threat-analysis-group/spyware-vendors-use-0-days-and-n-days-against-popular-platforms/
Ref :
1) https://googleprojectzero.blogspot.com/2022/11/mind-the-gap.html
2 ) Pwning the all Google phone with a non-Google bug : https://github.blog/2023-01-23-pwning-the-all-google-phone-with-a-non-google-bug/