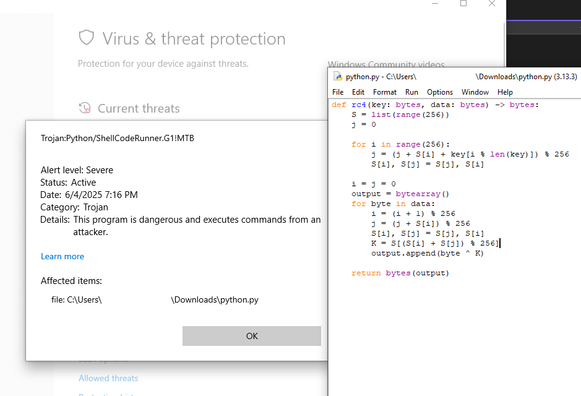
Microsoft really doesn't like RC4 encryption apparently 😆
I automate everything I can to replace human error with automated human error!
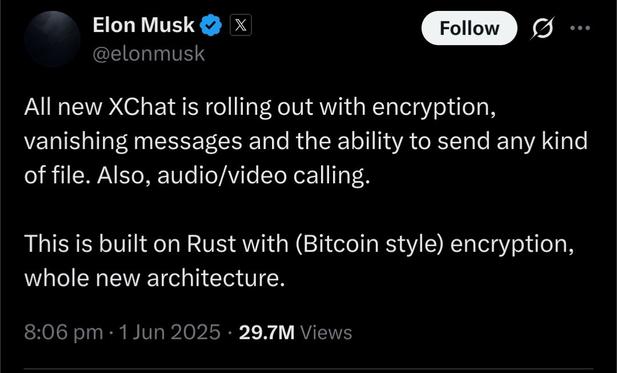
Dear Elon Musk:
Speaking as a maintainer of the most popular pure Rust implementations of the secp256k1 elliptic curve and SHA-256 hash function, there is no encryption in Bitcoin, only hashing and digital signatures.
You should probably be looking at Signal, oh wait you’re too busy spreading disinformation about nonexistent backdoors.
You want services which run in the EU and aren't using your data for profit?
Checkout the services we run!
https://meet.ffmuc.net - Videoconferencing
https://ffmuc.net/draw - Collaborative Whiteboards
https://cryptpad.ffmuc.net - Office Suite
https://hedgedoc.ffmuc.net - Collaborative Document Suite
DNS services:
IPv4:185.150.99.255/5.1.66.255
IPv6:2001:678:e68:f000::/2001:678:ed0:f000::
DoH: https://doh.ffmuc.net/dns-query
DoT: http://dot.ffmuc.net
Support our mission!
https://spende.ffmuc.net
Saying that 30% of all your code is generated “by software” (not “by AI”, but “by software”) is what you’d say if you knew perfectly well you can’t write and maintain a production OS with LLMs, but you have a financial motivation to inflate the number to ride a hype wave and eyeballed how much of your committed code is machine-generated by templates https://techcrunch.com/2025/04/29/microsoft-ceo-says-up-to-30-of-the-companys-code-was-written-by-ai/
EDIT: it seems this reporting omitted the rather load-bearing phrase "in some of our projects" from his exact words:
> I’d say maybe 20 to 30 percent of the code that is inside of our repos today in some of our projects are probably all written by software.
Now, can I believe that "some" projects at Microsoft are 30% AI-generated? Yes, because they have a lot of projects at a lot of different levels of needs-to-workness.
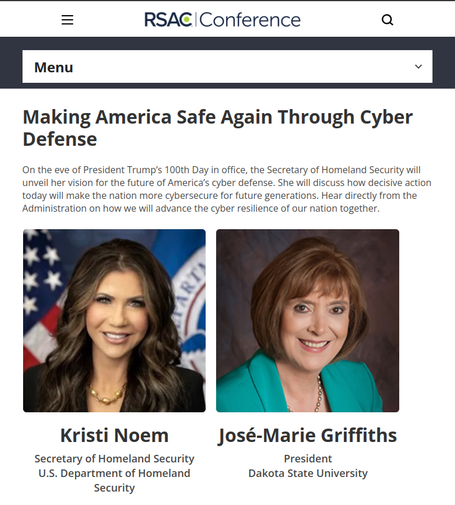
Looks like Corporate #infosec has made it's choice.
#RSAC is filled with talks embracing AI and making it "secure".
And they invited and encouraged the Trump regime to spread its disinformation - fully sanctioned and encouraged by the conference leadership(and by conference attendees who laughed at the regime's jokes and lies and issued no challenges or stands during the talk).
With the ostracization of #ChrisKrebs by industry and the full embrace of Kristi Noem as a speaker, this was the moment that infosec made its bed.
Y'all lie in it now.
Mastodon isn't perfect.
But the fact a social network exists that is completely free to use
has no venture capital investors
has no shareholders to answer to
has no growth targets
with a web interface with zero tracking cookies
and mobile apps with zero trackers at all
with ten thousand server administrators who donate their time for user safety
is - in my opinion - mindbogglingly cool, given the state of the world we live in. Not everything has to be shit. People make things better.
Hot off the presses: DOGE Worker's Code Supports NLRB Whistleblower
Yes, I turned another "oh btw" update here into a story. Please read/RT (thx!). Here's the top bit:
"A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk's Department of Government Efficiency (DOGE) siphoned gigabytes of data from the agency's sensitive case files in early March. The whistleblower said accounts created for DOGE at the NLRB downloaded three code repositories from GitHub. Further investigation into one of those code bundles shows it is remarkably similar to a program published in January 2025 by Marko Elez, a 25-year-old DOGE employee who has worked at a number of Musk's companies."
https://krebsonsecurity.com/2025/04/doge-workers-code-supports-nlrb-whistleblower/
Coworker: ...and the IP address are compared with a string match.
Me: grinning manically
Coworker: Why are you looking at me like that?
Me: Open up a terminal and type ping 4.2.514 and hit enter.
Coworker: ...what's the fourth number?
Me: grin widens Just hit enter.
Coworker: WTF!?
In September 2024, Highline Public Schools in Washington experienced a ransomware attack that led to a significant data breach, confirmed after a five-month forensic investigation. Threat actors infiltrated the district’s network, accessed sensitive systems, and exfiltrated personally identifiable information (PII) and protected health information (PHI) across multiple datasets. Exposed data included names, Social Security numbers, dates of birth, driver’s license and passport numbers, financial and employment records, digital signatures, medical and insurance information, and detailed student academic records. The breach impacted students, staff, and affiliates across 35 schools, compromising the integrity of the district’s information systems. In response, Highline initiated extensive cybersecurity hardening measures and is offering affected individuals one year of free identity theft protection via IDX. The incident underscores the critical vulnerabilities in K-12 infrastructure and the increasing targeting of education sectors by sophisticated ransomware actors. #CyberSecurity #Ransomware https://www.govtech.com/education/k-12/2024-ransomware-attack-compromised-data-from-highline-schools-wash
I bought $200 worth of stuff from Costco this week and they bought $0 worth of stuff from me. To resolve this deficit I will be charging myself $50 every time I go to the store. With this extra income I will build toasters, which I will attempt to sell to my local Costco for $200 each.
@Reshirams_Rad_Slam @GossiTheDog :catjam:
New, by me:
A Minnesota cybersecurity and computer forensics expert whose testimony has featured in thousands of courtroom trials over the past 30 years is facing questions about his credentials and an inquiry from the Federal Bureau of Investigation (FBI). Legal experts say the inquiry could be grounds to reopen a number of adjudicated cases in which the expert’s testimony may have been pivotal.
From the story:
In an interview this week, Harrington said court documents reveal that at least two of Lanterman’s previous clients complained CFS had held their data for ransom over billing disputes. In a declaration (PDF) dated August 2022, the co-founder of the law firm MoreLaw Minneapolis LLC said she hired Lanterman in 2014 to examine several electronic devices after learning that one of their paralegals had a criminal fraud history.
But the law firm said when it pushed back on a consulting bill that was far higher than expected, Lanterman told them CFS would “escalate” its collection efforts if they didn’t pay, including “a claim and lien against the data which will result in a public auction of your data.”
“All of us were flabbergasted by Mr. Lanterman’s email,” wrote MoreLaw co-founder Kimberly Hanlon. “I had never heard of any legitimate forensic company threatening to ‘auction’ off an attorney’s data, particularly knowing that the data is comprised of confidential client data, much of which is sensitive in nature.”
In 2009, a Wisconsin-based manufacturing company that had hired Lanterman for computer forensics balked at paying an $86,000 invoice from CFS, calling it “excessive and unsubstantiated.” The company told a Hennepin County court that on April 15, 2009, CFS conducted an auction of its trade secret information in violation of their confidentiality agreement.
“CFS noticed and conducted a Public Sale of electronic information that was entrusted to them pursuant to the terms of the engagement agreement,” the company wrote. “CFS submitted the highest bid at the Public Sale in the amount of $10,000.”
https://krebsonsecurity.com/2025/03/cyber-forensic-expert-in-2000-cases-faces-fbi-probe/
Tiny reminder that it's important
to boost posts on Mastodon!
Liking only will not help a post being seen more. Boosting will! :boost_ok: ✨
Boost the posts you want others to see. Add hashtags to your posts to help others find them.
This is the Fediverse way :mastodon:
One frustrating aspect of trying to write about all the incredibly reckless and risky actions taken by this administration with govt data is that by the time you're done writing, half the stuff in your story is outdated already, because they've reversed themselves, or they've been reversed. Or, and this is usually the most frequent cause: Because they've gone and done something even more colossally stupid, cruel and/or unwise.
I have not missed this aspect of reporting on the Trump administration at all. But it is absolutely true that their flood-the-zone-with-stupid approach really can become something like a mental ddos on journalists. And ofc that's intentional.
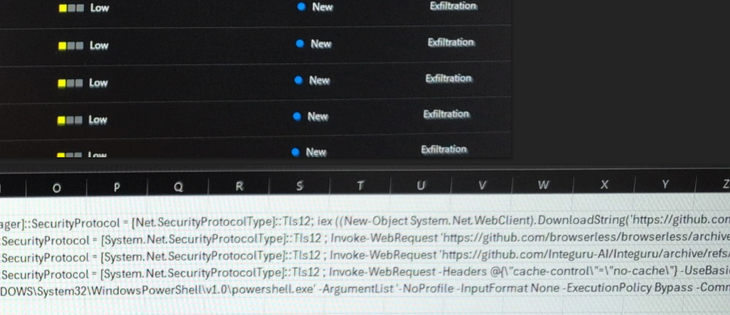
In today's Threat Model: Cybersecurity, @violetblue continues to track the irreparable harm DOGE is wreaking on US national security. Those headlines are super depressing, so here are today's Extras instead (also plenty scary).
Read/share/support: https://www.patreon.com/posts/122532103
#Cybersecurity #infosec #natsec
You had better take a shot, and then read this. Absolutely sobering. https://www.linkedin.com/posts/charles-spitzer-stadtlander-jd-mpa-9b018b25_urgent-national-security-threat-i-work-activity-7296973991716499456-31eV
“OpenAI tries to 'uncensor' ChatGPT | TechCrunch”
https://techcrunch.com/2025/02/16/openai-tries-to-uncensor-chatgpt/
And
“Trump's Silicon Valley advisers have AI 'censorship' in their crosshairs | TechCrunch”
Are exactly the sort of thing I was warning about the other day
“Poisoning for propaganda: rising authoritarianism makes LLMs more dangerous” https://www.baldurbjarnason.com/2025/poisoning-for-propaganda/
The new Trump administration have begun their book banning, and Julianne Moore's children's book "Freckleface Strawberry" has been banned, because it teaches children not to be sad that they are different, because everyone is different in some way — and that is just too inclusive to the hate administration.
Interesting statement filed in the case against the Treasury and DOGE which gives us some cybersecurity insights. Here's the key takeaways:
- Only a single DOGE employee (25 year old engineer Marko Elez) has direct access to the Treasury payment systems.
- The DOGE employee was only allowed to access the systems from an encrypted government issued laptop.
- The government issued laptop is equipped with monitoring software, data loss prevention, and tools to block internet access, and use of removable storage devices.
- Strict instructions were given that no data could leave this laptop for the duration of the engagement.
- The employee was meant to only have read access to treasury systems, but was accidentally granted write access.
- Following the accident, the employee's laptop was examined and it was concluded that no data had been written during the mistake.
- After the employee temporarily resigned over racist Twitter posts, all access was revoked, and all government issued equipment was recovered.
- The DOGE employee shared updates about his work with another DOGE employee, which "may have occasionally included screenshots of payment systems data or records"
My take:
If true, it seems that unlike other instances at different agencies, the Treasury abided by strict security protocols.
My only real cybersecurity question here are:
1) They document claims screenshots of payment records were shared with another DOGE employee. It doesn't specify how they were shared. Was it just the authorized employee showing his screen to someone, or were they transmitted outside of the laptop? If it's the latter, then it calls much of the claims made in the article into question.
2) This statement isn't clear "The Bureau enabled enhanced monitoring on his laptop, which included the ability to monitor and block website access, block the use of external peripherals (such as USB drives or mass storage devices), monitor any scripts or commands executed on the device, and block access to cloud-based storage services."
The use of the phrase "included the ability to" isn't really clear on if those security controls were actually being enforced. The phrasing could simply mean they enabled software that had those capabilities, but they weren't being used.
Now, cybersecurity aside, the bigger question is what was the purpose of any of this? To audit something as complex as a treasury payment systems, you'd need teams of forensic accountants.
A single 25 year old software engineer with no prior treasury experience poking around some files on a laptop is not an audit. The entire DOGE operation seems like a charade. The organization consists almost entirely of young engineers pulled from Musk's other companies, has produced no plan for how they intend to audit any of these systems, and lacks any oversight at all.