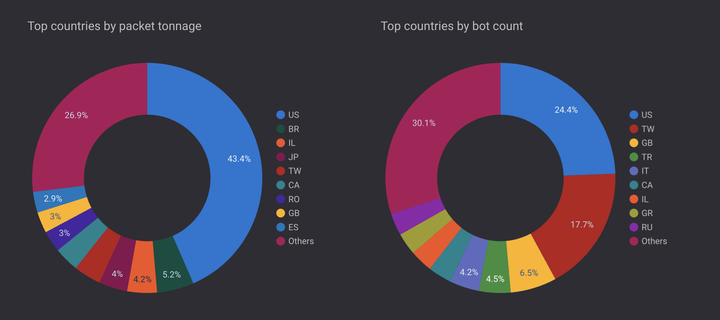
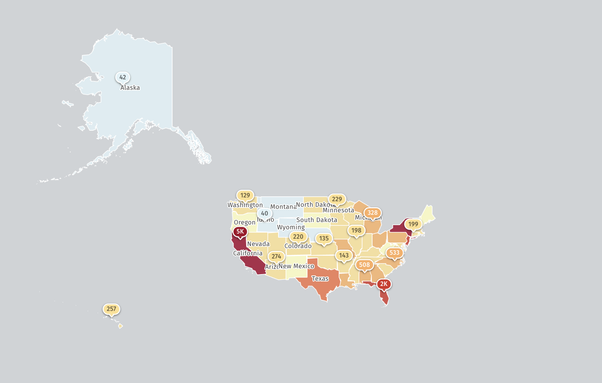
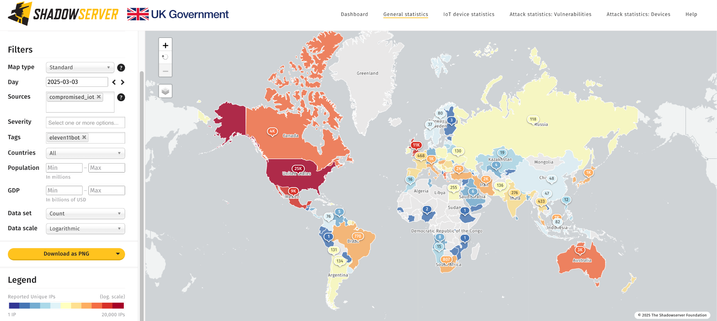
On 26 February 2025, the Nokia Deepfield Emergency Response Team (ERT) identified a significant new DDoS botnet, now tracked under #Eleven11bot
Primarily composed of compromised webcams and Network Video Recorders (NVRs), this botnet has rapidly grown to exceed 30,000 devices. Its size is exceptional among non-state actor botnets, making it one of the largest known DDoS botnet campaigns observed since the invasion of Ukraine in February 2022.
Eleven11bot has targeted diverse sectors, including communications service providers and gaming hosting infrastructure, leveraging a variety of attack vectors. Attack intensity has varied widely, ranging from a few hundred thousand to several hundred million packets per second (pps). Public forums report sustained attack campaigns causing service degradation lasting multiple days, some of which remain ongoing.