@johansolo ah! Y mientras estás en proceso puedes usar solamente un navegador para temas de google y utilizar la web en lugar de apps.
#SOC analyst and #PhD student in #computerscience. Member of @hackliza. Interested in #Cryptography, #Privacy, #Anonimity, #Bitcoin and #Monero. #MegaDrive #Genesis collector.
@johansolo para degooglizarte empieza dejando el ecosistema de google. GrapheneOS + protonmail o riseup + f-droid + Aurora store. Contras: el gps va a fallar bastante y olvidate de android auto o google pay. Algunas apps como las bancarias pueden fallar y necesitarás instalar (fácil con graphene) google services sandboxizado.
2024 was crazy:
- Married.
- First public talks.
- New work adventure.
- Bought an apartment (and an arcade cabinet!!!)
- Changed my car.
- Co-founded a company.
Three wishes for 2025:
- I hope it is a quieter year.
- I hope things keep as good as they are.
- I meant it I hope a quieter year. Really. Please.
[gal] Onte estiveron pola #BlackHat de Londres o noso @DonCaralludo e o noso amigo Marcos dando unha charliña sobre "Análise sintático de malware con Linguado". Menudas lendas!
[en] Yesterday our own @DonCaralludo and our friend Marcos were at #BlackHat London talking about "Syntax analysis for malware detection with Linguado". What a legends!
@XC3LL parabéns!!
@jartigag está acado de cocinarse! En diciembre/enero espero tener el paper listo para enviar.
Os nosos @DonCaralludo e @zer1t0 dando a súa charla “inxección de código en Python” na @pycones #pythones #python #vigo #pycones2024 #PyConES
@XC3LL homé, como ten que ser!
Novo artigo do @zer1t0, que apresenta a súa ferramenta keydump para leer os keyrings (protexidos) de terceiros procesos en Linux e extraer segredos como as credenciais de usuarias do dominio almacenadas por sssd. Agardamos que vos guste! https://hackliza.gal/posts/keydump/
I was playing with code injection to read processes keyrings on Linux. I've wrote a new tool, keydump, and showing how we can use it to extract cleartext credentials from sssd. Not an easy exploitable scenario, but I hope you like the article!!
Novo artigo do @zer1t0 explicando pasiño a pasiño como unir un Debian a un Active Directory (porque nos entornos privados tamén se pode meter software libre), incluíndo para que serve cada protocolo e ferramenta. Dende logo, moito lle gustan os internals a este rapaz! https://hackliza.gal/posts/linux-en-ad/
Brand new post from our own @zer1t0 explaining with baby steps how to join Debian to Active Directory (yes, you can add free software to a privative environment!) including detailed explanations of protocols and tools. Is there anyone in the world who love sysinternals more than him? We really doubt it! https://hackliza.gal/en/posts/linux-en-ad/
Have you ever added a DNS server to /etc/resolv.conf that disappeared? Our own @zer1t0 did a research about it and he brought a detailed solution for several GNU/Linux daemons: https://hackliza.gal/en/posts/cambiar_dns_linux/
Nunca che pasou de engadir un servidor DNS a /etc/resolv.conf e que desaparecera ao pouco? O noso compañeiro @zer1t0 estivo indagando sobre este problema e ofrece unha solución detallada para varios demos de rede de GNU/Linux: https://hackliza.gal/posts/cambiar_dns_linux/
@signalapp is there any know issue with signal in samsung devices? I’ve been told that it takes ages to sent or receive messages. They tried reinstalling and the issue persists.
In my new blog for #CheckPointResearch I propose a new injection technique, using the Thread Name API - check it out! 💙 : https://research.checkpoint.com/2024/thread-name-calling-using-thread-name-for-offense // #ThreadNameCalling #processInjection
Mañá imos estar online un rato para falarmos de ideas, actos e barallar en xeral. Se gostades vémonos ás 21:00 por aquí: https://app.element.io/#/room/#hackliza:matrix.org. Até mañá!
Dear Fellowlship,
Our owl @XC3LL showed during the EuskalHack VII conclave a technique to achieve stability when overwriting the R/W/X memory in VBA. Read this addendum in our homily: https://adepts.of0x.cc/vba-rwx-addendum/
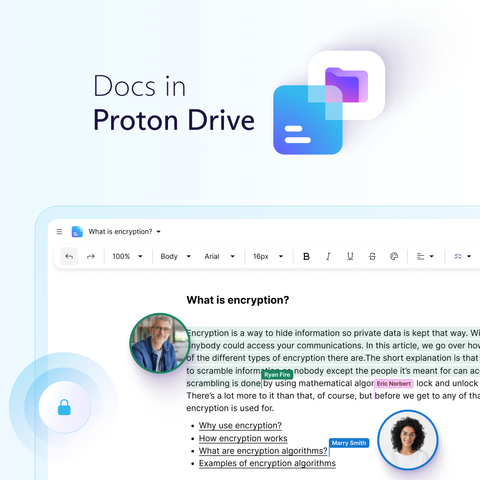
Say hi to Docs: end-to-end encrypted collaborative document editing in Proton Drive
✍️ Create, edit, and share documents securely
🤝 Collaborate in real-time with live cursors, presence indicators, and comments
↕️ Import/export with ease
Docs starts rolling out in #ProtonDrive today, and it will be available to everyone over the next few days.
Make sure you're running the latest versions of the Drive apps to try it out soon!
Find out more: https://proton.me/blog/docs-proton-drive
You can find my talk about Offensive VBA here => https://github.com/X-C3LL/congresos-slides/blob/master/Offensive%20VBA.pdf