@Sinjo hell yeah, neat!
I like to be called Jeff. https://somethingsimilar.com
Was @jmhodges on Twitter
@Sinjo Yeah! It was my Killing the Cowboy: Lessons from a Pager talk I did a million, jillion years ago. https://vimeo.com/42898664
There's better ways to do what we were doing like with using deadlined Context objects in Go, or whatever) We even did some version of that deadlining in Rails eventually, iirc.
I know a lot of folks on here have feelings about the bird site. I have them too. But:
There is a time capsule from 2012 embedded in a glass case inside Twitter HQ. I helped put it there. The Computer History Museum said they'd accept it as a donation, and then all of the Twitter things happened. I'd love to retrieve it before they close the building.
I don't know anyone on the inside anymore. Anyone have any suggestions?
Sorry, folks, if you follow me and have no idea what the hell I’m on about today, here’s a quick explainer:
https://toot.cat/@skye/112184566541867183
Some notes from analyzing the bash part obfuscation of the xz/liblzma part – link leads to the part I found most interesting – it was added in 5.6.1:
https://gynvael.coldwind.pl/?lang=en&id=782#stage2-ext
TL;DR: in 5.6.1 there's some code added that looks for specific signatures in files in tests/files, and if found, it grabs some data from these files, deciphers them, and executes them. NO FILES WITH THESE SIGNATURES EXIST YET, so it's like a way to extend the backdooring scripts in the future by just adding new binary test files. Guess things weren't supposed to end here.
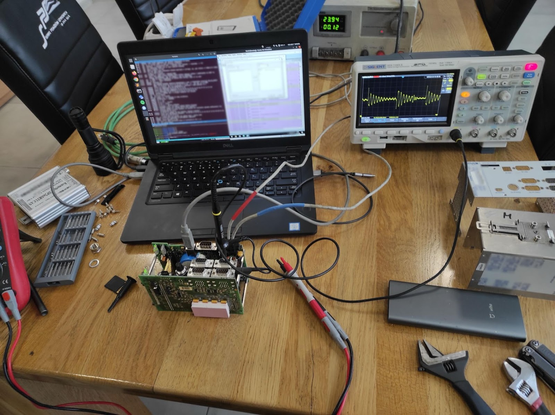
I was doing some micro-benchmarking at the time, needed to quiesce the system to reduce noise. Saw sshd processes were using a surprising amount of CPU, despite immediately failing because of wrong usernames etc. Profiled sshd, showing lots of cpu time in liblzma, with perf unable to attribute it to a symbol. Got suspicious. Recalled that I had seen an odd valgrind complaint in automated testing of postgres, a few weeks earlier, after package updates.
Really required a lot of coincidences.
It is 2024, and we're back once again on the "to counteract malign Russian influence, we must adopt speech-suppressing laws identical to those they have in Russia" bullshit. This time, the offending party is the California state legislature. Californians, call your state senators to oppose SB 1228:
https://leginfo.legislature.ca.gov/faces/billNavClient.xhtml?bill_id=202320240SB1228
"This is like Russia!" isn't hyperbole, it's a literal fucking actual law they passed a whole-ass decade ago:
https://www.theverge.com/2014/5/7/5690410/putin-signs-law-forcing-bloggers-to-register-with-russian-media-office
Here's the design, sketches of IND-CCA/sUF-CMA proofs in the multi-user insider model, and a neat lil Rust impl: https://github.com/codahale/pqc-signcrypt
The common link behind the companies challenging NLRB's legal authority is Morgan Lewis. They represented Elon Musk's various companies, Trader Joe's, and Amazon in many NLRB cases. The lawyer leading the charge for Morgan Lewis, Catherine Eschbach, was also present at my NLRB hearing during the first day, during which X/Twitter was represented by another Morgan Lewis attorney.
Morgan Lewis is, and has been for a very long time, one of the most anti-union law firms in the country.
You're on macOS. Which are you picking?
It is now illegal in California to park a car within 20 feet approaching a marked or unmarked crosswalk (i.e. most intersections), even if the curb is not painted red.
Cities can’t write tickets for this until Jan 1, 2025 but can write warnings now.
The great dirty secret of the software industry is that an awful lot of the work that is critical to sustainably build and maintain a software system/product/whatever only happens in the wild because one person with a little extra care and a little extra time decided "I'm not going to wait for this to get priority. I'm not going to wait for permission. I'm just going to do this because it should be done, and damn the consequences."
This link captures the confusion about how to pronounce "fsck":
https://lwn.net/Articles/190223/
Here's the truth. Ted Kowalski, username frodo, may he rest in peace, was the original author, just down the hall from my office in Murray Hill, and his name for the program had a 'u' where there is now an 's'. Management made him change it for distribution, but they couldn't make him change his pronunciation.
RT @aarmlovich Remember when everyone said "High-wage superstar zoning can't be fixed, why don't you just move to [small cheap city]?"
Well it turns out [small cheap city] also has apartment bans & few vacant units, so even just a few thousand Californians totally overwhelm them
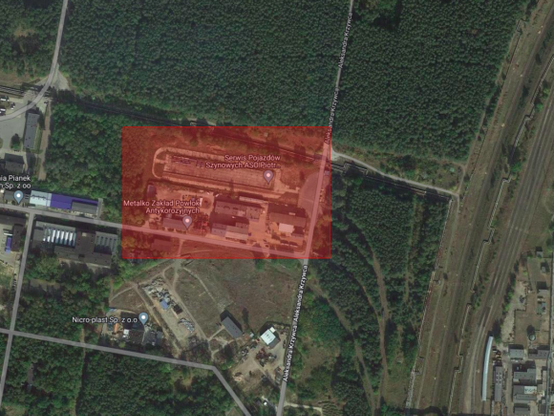
We found that the PLC code actually contained logic that would lock up the train with bogus error codes after some date, or if the train wasn't running for a given time. One version of the controller actually contained GPS coordinates to contain the behaviour to third party workshops.
It was also possible to unlock the trains by pressing a key combination in the cabin controls. None of this was documented.
2/4
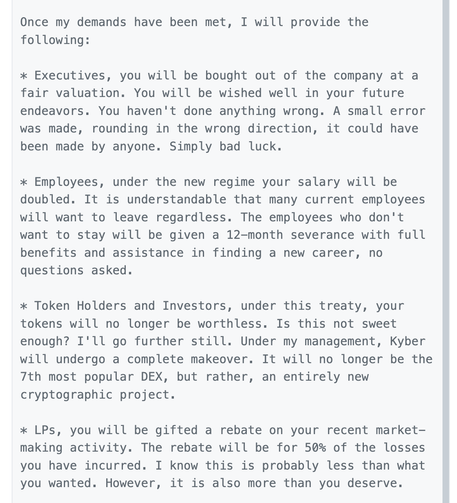
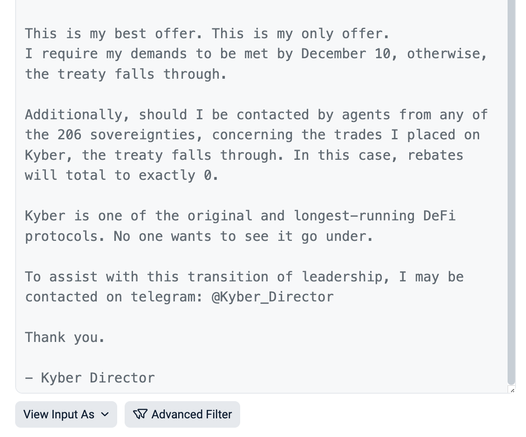
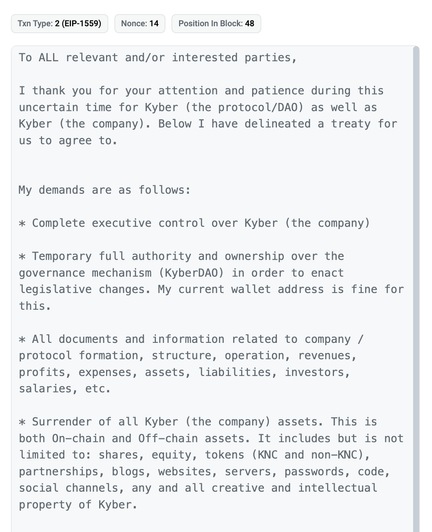
The KyberSwap attacker responded with their "negotiation" and it is wild.
"My demands are as follows: Complete executive control over Kyber". They signed the message "Kyber Director".
Reminder: using other people's work without consent or permission is something we as humans do all the time, and can be ethical in many contexts. Please don't buy into the copyright maximalist position that every use must require permission.
And yes, this is about AI, and no, I am unsure whether AI scraping is ethical. But we cannot let distaste for AI chip away at the small space we've painstakingly carved out for fair, ethical, permissionless use.
@agwa the certificate transparency ban really betrays what the idea behind the law is. That ban also clearly shows that even the hypothetical law-abiding-nothing-to-fear EU citizen is harmed by the law, as it makes MitM attacks much easier for any attacker, not just the EU government.