Current vibes... 😅
Advanced Practices 🦅 at Google Threat Intelligence Group
Threat Attribution, Frontline Intelligence, Malware Analysis, Threat Hunting, Incident Response
@avolha zapisane w kolejce do odsłuchania :)
Mądrego to i fajnie posłuchać 😉 czyli Cybergadki z Irkiem Tarnowskim, któremu w przeszłości nieraz się zdarzyło napisać coś do z3s
Vibe coding is real…
I was just blown away by Gemini 2.5 Pro capabilities to refactor and improve python code. I cannot share details as it is an internal use-case, but it took Gemini only around 5 minutes to completely refactor 1500 LOC python script the way I wanted. What's even better is that it also fixed a few other minor bugs (something I didn't ask for), added comments, debug messages, and improved the overall readability of the code.
It only made one very simple mistake, that took me 20 minutes to fix manually, and after that I had a perfectly runnable code to use, with performance improved 300%.
I was pretty skeptical about all this "AI will replace programmers hype" but now I don't know what to think. It is already a way better (and 100x faster) programmer than I am. This is admittedly not that big of an accomplishment, but who knows in a year or two it might be better than actual programmers ;)
Excellent story, featuring the equally excellent @jik.
Love this commentary on our recent blog, pineapples vs ananas 😂 If you don't yet listen to "Three Buddy Problem" podcast you are missing out!
https://www.youtube.com/watch?v=KHhrA4sazoY&ab_channel=ThreeBuddyProblem
@avolha dlatego ja czytam / słucham tylko w oryginale - a ksiazka fajna
This is something that was occupying my time for some time already and I'm super happy that this research is finally released.
I believe this to be only a second reporting on malware targeting Juniper devices. Following Lumen Technologies blog from last month (but this one related to a different actor and different malware).
This blogs dives into specifics of Veriexec bypass vulnerability used by UNC3886, and details of 6 different backdoors found on Juniper MX devices.
UNC3886 is a very interesting actor that does not shy away from targeting less commonly known technologies like routers, edge devices or hypervisors.
More details here: https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-espionage-targets-juniper-routers
This is a "clip" (I don't even know how to call this) that the President of the United States publishes on his social media account, regarding a region that has been impacted by one of the greatest humanitarian crisis of our times.
I try not to comment publicly on the US politics, but... SERIOUSLY???
https://truthsocial.com/@realDonaldTrump/posts/114068387897265338
Do artykułu o platformie moje.cert.pl dodaliśmy otrzymane od @cert_polska_en odpowiedzi na nasze pytania. Zachęcamy do rzucenia okiem! Jest mowa o kilku nowych funkcjonalnościach. https://adwersarz.pl/moje-cert-pl-darmowa-platforma-do-ochrony-twojej-firmy-bloga-i-portalu-jak-jej-uzyc/
One promise of crypto has long been its potential to flout state control. Gambaryan's story is what happens when that promise actually comes into conflict with an unaccountable government.
Read the full, untold story of his hellish ordeal—and how he finally got free. https://www.wired.com/story/untold-story-crypto-crimefighters-descent-nigerian-prison-binance/
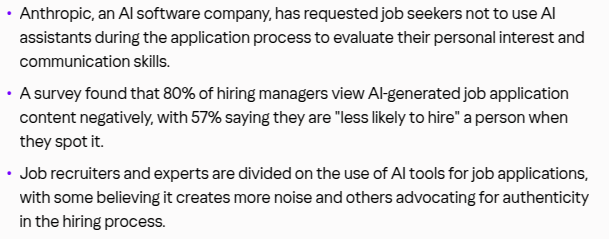
Anthropic (Claude LLM) AI Company doesn’t want people using AI for their resumes or any part of Interview for software developer or IT jobs at their office. How ironic? LOL. The company says AI tools are flooding their system with bogus résumés and too many applicants. They can't find real talent even using their own AI system where candidates lie about their skills when resumes are created by AI.
Analiza kodu źródłowego aplikacji wykorzystującej technikę #NFCRelay przeciwko klientom PKO BP, o której niedawno pisaliśmy na z3s. Irek - jak zwykle - odwalił kawał dobrej roboty 💪
🇵🇱 Atak NFC Relay - przestępcza ”komercjalizacja” projektu badawczego NFCGate
🇬🇧 NFC Relay = Criminal “Commercialization” of the NFCGate Research Project
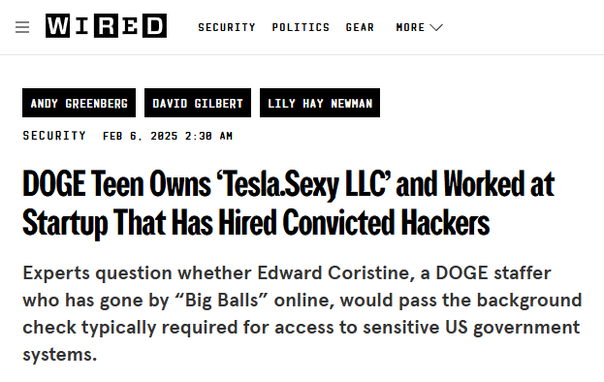
Oh man, I have so many stories about the "startup" (Path Network), which the 19-year-old DOGE employee, Edward Coristine previously worked for.
https://www.wired.com/story/edward-coristine-tesla-sexy-path-networks-doge/
My first interaction with the founder, Marshal Webb, was in 2016 when the company was called "BackConnect'. I'd recently posted a research paper on the Mirai botnet, which lead to him harassing me online, simply because he considered himself to be the sole authority on Mirai.
It later turned out, that a lot of his knowledge came from the fact that he was personally hosting the threat actors' infrastructure, therefore had direct insight into the botnet. He tried to play it off as an "intelligence gathering operation". Everyone knew he was really just in bed with the threat actors, but nobody could prove it enough to make a case against him.
At some point shortly after, a DDoS-for-hire service got hacked and its entire customer database along with all DDoS attack logs was leaked online. One of the records traced back to an employee of his DDoS mitigation firm, and from a combination of attack logs and corroboration with customers, it was determined that they had been launching DDoS attacks against businesses, then cold calling them to sell DDoS protection services.
It was fairly apparent from the fact the emails coincided with the DDoS attacks, but did not originate from the the employee performing the attacks that the company was in on it, and this wasn't the work of some rogue employee. Nevertheless, said employee got thrown under the bus, convicted, and was unsuccessful in proving that his employer was in on the conspiracy, although they most certainly were.
Eventually, the founder ended up being named in some kind of criminal complaint or other FBI related court document. The specific wording seemed to imply that he'd gotten caught doing something illegal enough that he'd become an informant to save himself. Amusingly, when the document surfaced, the company just issued a press release about how they were "helping the FBI stop crime" and nothing become of it.
The company has always been shady as hell, and while it's not abnormal for cybersecurity firms to hire reformed hackers, I've not seen a single employee who was not directly involved in cybercrime immediately prior to getting hired. Furthermore, multiple of the employees have been caught committing cybercrime while working for the company.
Originally, when I posted this thread on February 6th, I stopped short of any allegation that Edward himself was involved in cybercrime. Since then @briankrebs was able to trace his aliases back to a known cybercrime organization and confirm he indeed was directly involved in cybercrime as recently as May 2024.
You can find Brian's Mastodon thread on the matter here:
https://infosec.exchange/@briankrebs/113965646509637016
https://infosec.exchange/@briankrebs/113957683483583881
Kto by się spodziewał na białostockim uniwerku wydarzenia na temat ransomware'u z udziałem czołowych polskich specjalistów od cyber? No, może ja, bo wiem, kto je organizuje 😃
Fragment agendy:
👉 Zabezpieczenie i „utwardzenie” środowisk opartych o technologie Microsoft – Grzegorz Tworek – Microsoft Polska
👉 Reagowanie na incydenty ransomware – dobre praktyki pozwalające zminimalizować skutki ataku – Maciej Broniarz – CERT.ngo
👉 Współpraca z podmiotami Krajowego systemu cyberbezpieczeństwa oraz cybersamodzielność – Mateusz Szymaniec – CERT Polska
👉 Prezesie - jakiś ransomware pisze że ma nasze dane... – płk Jarosław Wacko, DKWOC | CSIRT MON
Kiedy i gdzie? 17 lutego w godz. 10:00–13:30 na kampusie UwB
Jeśli ktoś ma możliwość, na pewno warto się wybrać
So I finally turned a recent popular post here into a proper story.
Teen on Musk’s DOGE Team Graduated from ‘The Com’
Wired reported this week that a 19-year-old working for Elon Musk‘s so-called Department of Government Efficiency (DOGE) was given access to sensitive US government systems even though his past association with cybercrime communities should have precluded him from gaining the necessary security clearances to do so. As today’s story explores, the DOGE teen is a former denizen of ‘The Com,’ an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network for facilitating instant collaboration.
https://krebsonsecurity.com/2025/02/teen-on-musks-doge-team-graduated-from-the-com/
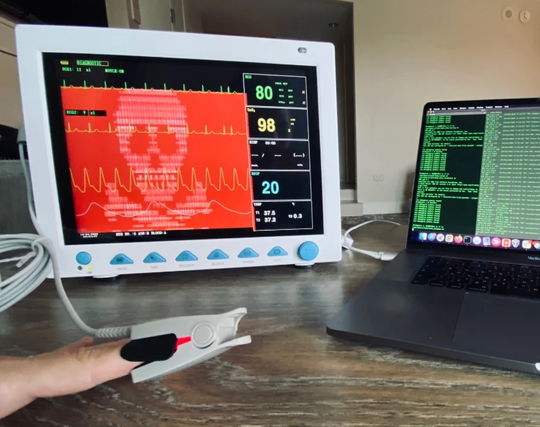
Tylna furtka zagrażająca pacjentom czy prymitywny mechanizm aktualizacji?
Nie wszystko jest tym, czym się wydaje ;)
New: Elon Musk's DOGE team was granted "full access" to sensitive Treasury payment systems that control trillions of dollars in payments to Americans, including Social Security checks and tax refunds.
Sen. Ron Wyden said Musk’s access poses a “national security risk.”
The access could also be considered a massive data breach of Americans' personal information in the hands of unelected private individuals.