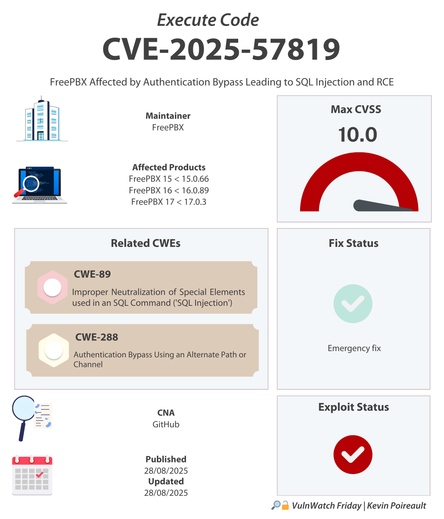
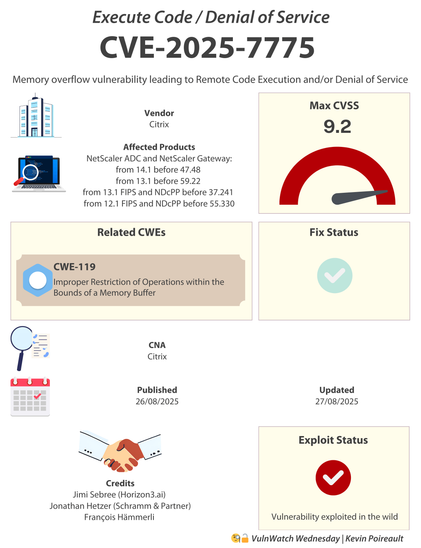
𝐋𝐞𝐠𝐢𝐭𝐢𝐦𝐚𝐭𝐞 𝐂𝐡𝐫𝐨𝐦𝐞 𝐕𝐏𝐍 𝐄𝐱𝐭𝐞𝐧𝐬𝐢𝐨𝐧 𝐓𝐮𝐫𝐧𝐬 𝐭𝐨 𝐁𝐫𝐨𝐰𝐬𝐞𝐫 𝐒𝐩𝐲𝐰𝐚𝐫𝐞
A popular Google-featured browser extension offering a VPN service recently turned malicious and is now spying on users’ every move online.
🕵️ Researchers from Koi Security detected that FreeVPN.One, a VPN extension with over 100,000 installs on the Google Chrome Web Store, a ‘Verified’ status and a 3.8/5 rating from 1110 reviews, has been acting as spyware for the past five months.
The researchers contacted the developer of FreeVPN.One, but their explanations for the extension’s behavior failed to align with the researchers’ observations.
⚠️ This new research, published on 𝑰𝒏𝒕𝒆𝒓𝒏𝒂𝒕𝒊𝒐𝒏𝒂𝒍 𝑽𝑷𝑵 𝑫𝒂𝒚, is a reminder that not all VPNs are equal and that many so-called privacy tools can be malicious, while even reputable commercial providers often lack transparency about the data they collect from users.
📰 Read my story here: https://www.infosecurity-magazine.com/news/chrome-vpn-extension-spyware/
📜 Read the full Koi Security report here: https://koi-security.webflow.io/blog/spyvpn-the-vpn-that-secretly-captures-your-screen#heading-3