On Tuesday morning near RSAC, I'll be presenting with at a fireside chat with @Secitup with IANS. We'll be talking about where you should (and probably shouldn't) use AI in your security operations, with specific examples and lessons learned. Join us!
https://www.iansresearch.com/ians-at-rsa-in-2025
Breaker of software, investigator of incidents | GSE #150 | Faculty at IANS Research | Stuff: jake at malwarejake dot com | He/him
Clients: I understand why you might want to record an IR tabletop exercise. The ability to review it later could be helpful. But it's almost certainly discoverable in litigation (yes, even if your internal counsel are present). The value simply isn't there given the outsized risk.
I'm officially done pretending what happened to Oracle somehow didn't involve Oracle Cloud. Transparency from Oracle has been garbage. I literally cannot recommend OCI to any of my clients at this point.
@Jacob Concur. I've already talked to several overseas DEFCON regulars who aren't coming this year.
I predict RSAC is going to be a lot less heavily attended than past years. Between economic uncertainty and the VERY REAL risks of attendees traveling to the US, I suspect a lot of people will save the travel budget and just stay home. Hope I'm wrong, but kind of doubt it.
You cannot simultaneously hold that "cybersecurity is a priority for the federal government" and "we're cutting CISA services with no replacements for federal agencies."
This is your regular reminder (apropos of nothing in particular) that ransomware, an actual national security threat, only exists in its current threat because we fail to fully regulate off-ramps for crypto into fiat.
https://www.reuters.com/world/us/us-justice-dept-disbands-cryptocurrency-enforcement-unit-2025-04-08/
It is NOT GREAT(TM) to hear that threat actors were in OCC's network and reading emails for almost two years (timeline from paywalled Bloomberg article citing a memo from OCC to Congress).
It's even worse that OCC needed MSFT to notify them of the incident.
https://occ.gov/news-issuances/news-releases/2025/nr-occ-2025-30.html
If you're using Ivanti at the perimeter, I have to presume at this point that you enjoy incident repsonse. There's no other rational explanation...
Working on some code and I have to say that while this is just a word wrap error, I can't think one that's more on point...
If you work in DevOps read this post-mortem. If you don't work in DevOps, send this to your coworkers that do. Trust me, it's important they read this.
https://www.landh.tech/blog/20250211-hack-supply-chain-for-50k/
Auto manufacturer Stellantis is laying off 900 people (at least) temporarily due to the new tariffs.
This is the first of many stories you'll read over the next month of tariffs "helping US manufacturing" if they're not repealed.
https://www.reuters.com/business/autos-transportation/stellantis-says-will-temporarily-lay-off-900-us-workers-following-tariff-2025-04-03/
@Cyberoutsider These come through Windows Store, so I think the security boundary there is "can malware get into Windows Store?"
Again, Microsoft - unsolicited advertisements for games have NO PLACE in Windows 11 Professional. Please slap whoever decided this was appropriate.
Remember the part of required federal records management training that says "it's okay to use Gmail for work as long as you cc government accounts?"
Yeah, me neither...
It's 2025 - please stop using the terms whitelisting and blacklisting. Yes, I know many of these terms were acceptable when you were growing up.
Continuing to use them today shows you're unable to adapt to change, which particularly in high-change environments like cybersecurity, is NOT a good look.
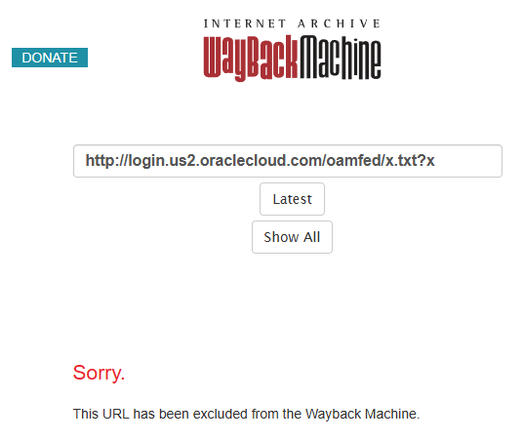
This is Oracle actively covering up evidence of an intrusion. This is someone executing 1990's breach playbooks in 2025.
@dsalo Wow - that's awesome.
@j_angliss Well played.
At this point, every statement I read from Oracle feels like one of those convos: "That looks like a nasty bruise, how'd you get it?" and they're like "I definitely wasn't having sex with a horse" and the answer leaves you with more questions than you had originally...