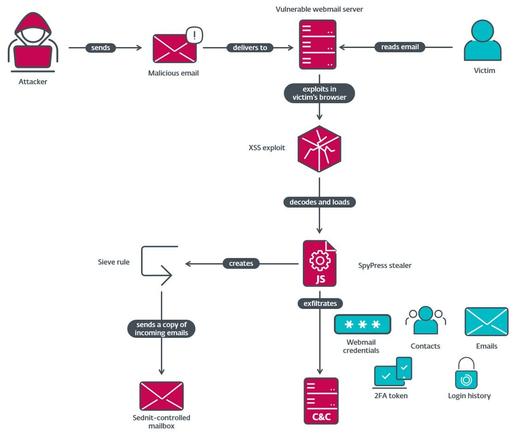
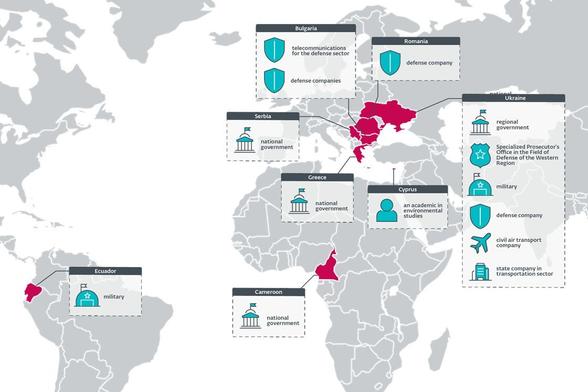
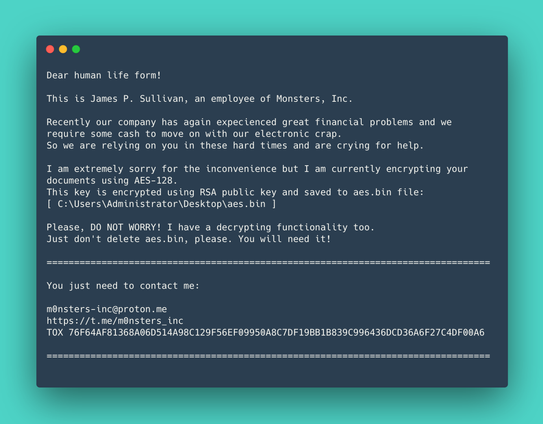
#ESETresearch publishes its investigation of Operation RoundPress, which uses XSS vulnerabilities to target high-value webmail servers. We attribute the operation to Sednit with medium confidence. https://www.welivesecurity.com/en/eset-research/operation-roundpress/
In 2023, Operation RoundPress only targeted Roundcube, but in 2024 it expanded to other webmail software including Horde, MDaemon, and Zimbra.. For MDaemon, Sednit exploited the zero-day XSS vulnerability CVE-2024-11182.
Most victims were governmental entities and defense companies in Eastern Europe, although we have observed governments in Africa, Europe, and South America being targeted as well.
Our blogpost provides an analysis of the JavaScript payloads, which we named SpyPress. They are able to steal webmail credentials, and exfiltrate contacts and email messages from the victim’s mailbox. IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/operation_roundpress 5/5
Malware researcher at @ESETresearch
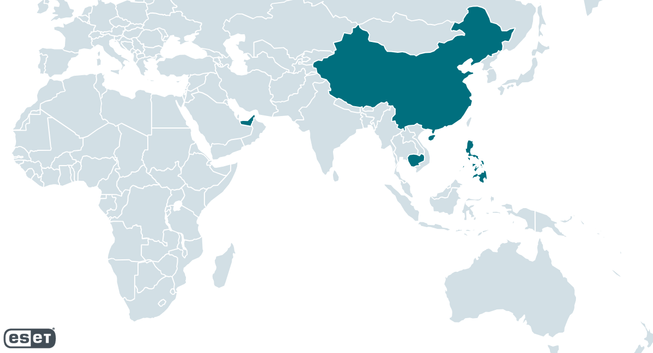
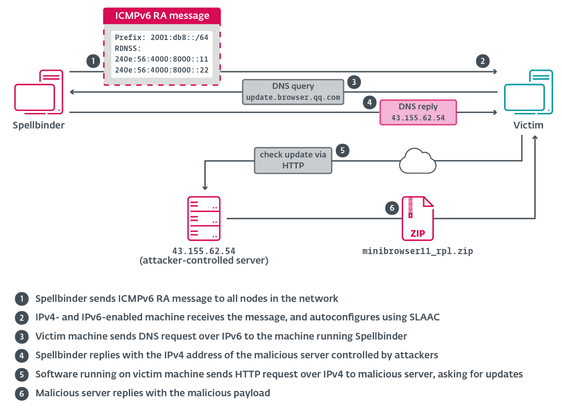
#ESETResearch analyzed the toolset of the China-aligned APT group that we have named #TheWizards. It can move laterally on compromised networks by performing adversary-in-the-middle (AitM) attacks to hijack software updates. https://www.welivesecurity.com/en/eset-research/thewizards-apt-group-slaac-spoofing-adversary-in-the-middle-attacks/
Since at least 2022, the group has targeted individuals, companies, and unknown entities in the Philippines, the United Arab Emirates, Cambodia, mainland China, and Hong Kong.
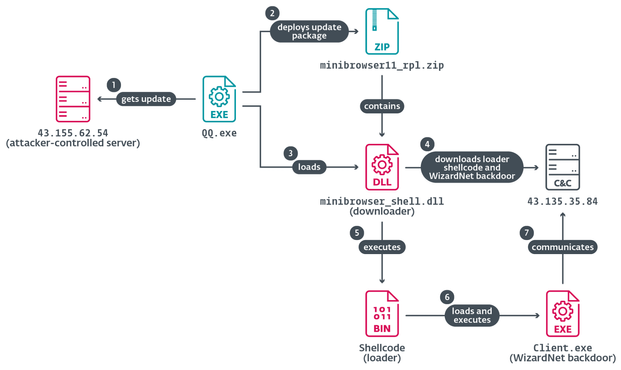
#TheWizards deploy a tool we have named #Spellbinder, which implements IPv6 SLAAC spoofing to redirect IPv6 traffic to the machine running Spellbinder, making it act as a malicious IPv6-capable router.
Spellbinder intercepts DNS queries associated with update domains for Chinese software. We focus on a recent case in which an update of Tencent QQ was hijacked to deploy TheWizards’ signature backdoor, WizardNet.
In our blogpost, we also discuss links we uncovered between #TheWizards and the Chinese company Dianke Network Security Technology, also known as UPSEC.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/thewizards
#ESETresearch published its investigation of Operation FishMedley, a global espionage operation by the China-aligned APT group FishMonger. We identified seven victims – including governments, NGOs, and think tanks – across Asia, Europe, and the US.
https://www.welivesecurity.com/en/eset-research/operation-fishmedley/
The same operation was the subject of a recent US DOJ indictment against I SOON employees and officers of China’s Ministry of Public Security. #ESETresearch independently determined that FishMonger is operated by the Chinese contractor I SOON.
https://www.justice.gov/opa/pr/justice-department-charges-12-chinese-contract-hackers-and-law-enforcement-officers-global
IoCs available in our GitHub: https://github.com/eset/malware-ioc/tree/master/fishmonger
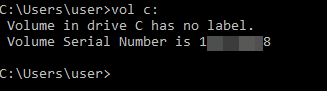
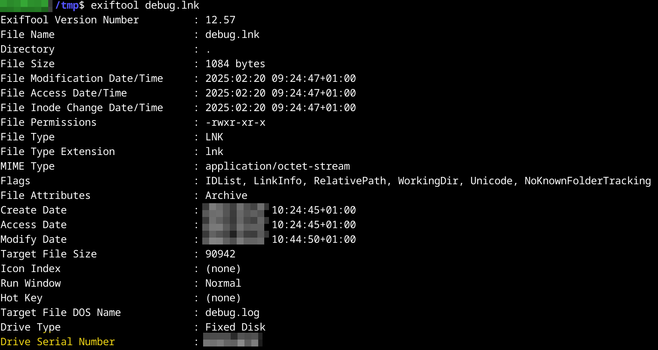
For incident responders investigating Shadowpad cases, remember to retrieve the volume serial number where #Shadowpad was deployed. The first time the malware is run, it will delete the encoded payload file (<random name>.tmp), and encrypt it in the Windows registry using the volume serial number. Those can also be found in LNK and Prefetch files in case you don't have live access to the host anymore.
You can then use the VolumeID tool from Sysinternals to change the volume serial number of your virtual machine
https://learn.microsoft.com/en-us/sysinternals/downloads/volumeid
#ESETResearch released its latest APT Activity Report, covering the period from September until the end of December 2022 (T3 2022). Take a look ➡ https://www.welivesecurity.com/wp-content/uploads/2023/01/eset_apt_activity_report_t32022.pdf 1/4
#ESETResearch releases IPyIDA 2.0, a plugin for IDA Pro that integrates IPython for a better console. Learn about all the new features on Hex-Rays’ blog at https://hex-rays.com/blog/plugin-focus-ipyida/ or read the tl;dr down here 👇 @marcetienne 1/5
Today, @ESETresearch identified a new wiper from #Agrius, a suspected Iranian threat actor that previously deployed the Apostle #ransomware and #wiper in a supply chain attack. Check out all the details at WeLiveSecurity: https://www.welivesecurity.com/2022/12/07/fantasy-new-agrius-wiper-supply-chain-attack/
PwC's #threatintel team published our reporting on Russia-based TA #BlueCallisto (aka #TAG53 #SEABORGIUM #Callisto). Though they have included Ukrainian targeting in their operations, they've maintained a focus on US government organizations including the US National Labs.
Reporting here:
https://www.pwc.com/gx/en/issues/cybersecurity/cyber-threat-intelligence/blue-callisto-orbits-around-us.html
(Recorded Future also published research on the same actor who they call #TAG53
https://www.recordedfuture.com/exposing-tag-53-credential-harvesting-infrastructure-for-russia-aligned-espionage-operations)
(also posted on the bird site)
"Amnesty International Canada hit by cyberattack out of China, investigators say"
https://www.cbc.ca/news/politics/amnesty-international-canada-cyber-attack-china-1.6674788
If you pivot on ESET's detection (https://www.virustotal.com/gui/search/eset_nod32%253A%2522a%2520variant%2520of%2520Win32%252FKryptik.GZGF%2522/files), you'll see more trojanized software and bitbucket repos. No idea what it is though.
There are similarities with previous attacks conducted by #Sandworm: a PowerShell script used to distribute the .NET ransomware from the domain controller is almost identical to the one seen last April during the #Industroyer2 attacks against the energy sector. 4/9
On Nov 21st #ESETResearch detected and alerted @_CERT_UA of a wave of ransomware we named #RansomBoggs, deployed in multiple organizations in Ukraine🇺🇦. While the malware written in .NET is new, its deployment is similar to previous attacks attributed to #Sandworm. 1/9
I choose a slightly different method: right click -> Mark All as Read 😂
Hey Mastodon! We recently published our APT threat report, looking back at the past few months of threat actor activities monitored by #ESETresearch. Check it out https://www.welivesecurity.com/wp-content/uploads/2022/11/eset_apt_activity_report_t22022.pdf