- Google's moat on search is thinner than we think: they pay for the privilege of being the default search engine in various search bars like the URL in browsers or on iOS. OpenAI could easily bump them out of this spot which would be a massive hit. Especially with the Jony Ive connection to Apple.
@mattjay from bird app
I'm not big on predictions but I thought of a few things I think are highly probably while out for a drive this morning:
- OpenAI obviously has Google and Apple in it's crosshairs, Jony Ive just adds fuel to that. Search + consumer devices.
- Ads are coming to AI responses. It is inevitable. I barely use Google search anymore, I ask ChatGPT nearly everything. Only a matter of time before sponsored answers show up.
I know my addictive personality, and for that reason I'll never download Balatro.
Just a boy in a daily battle with his Apple Watch battery.
Read Coinbases whole announcement here: https://www.coinbase.com/blog/protecting-our-customers-standing-up-to-extortionists
For more updates like this - Join over 28,000 pros who subscribe to my free weekly newsletter:
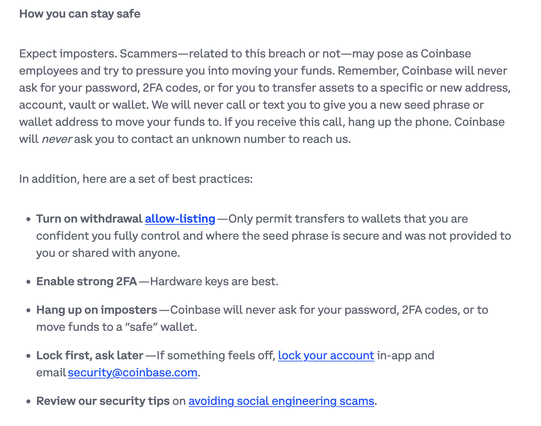
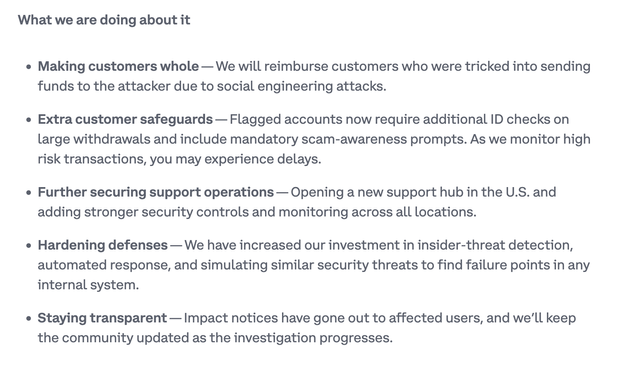
For affected users: Company promises reimbursement for any losses from social engineering attacks stemming from this breach.
Threat actor TTPs suggest sophisticated social engineering operation.
They're likely impersonating Coinbase support to trick victims into transferring funds.
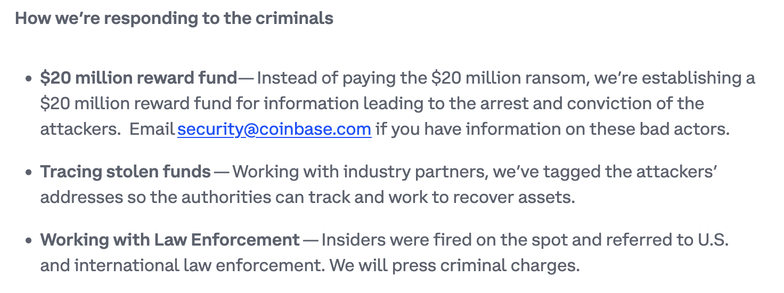
Rather than pay ransom, Coinbase is creating a $20M reward fund for intel leading to arrests.
What a baller move to flip the script here.
Coinbase is implementing enhanced withdrawal controls, mandatory scam awareness checks, and ID verification for flagged accounts.
Technical controls: Increased investment in insider threat detection systems, automated response capabilities, and red team simulations targeting internal systems.
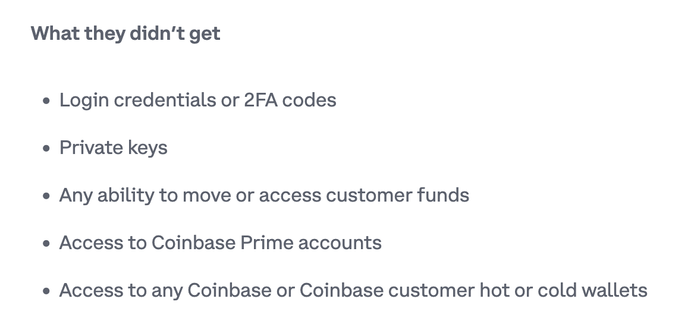
No Coinbase Prime accounts were touched.
Attackers specifically targeted retail customers, likely for subsequent social engineering campaigns.
Threat actors specifically targeted overseas support staff, successfully recruiting multiple insiders who abused legitimate access to customer support tools.
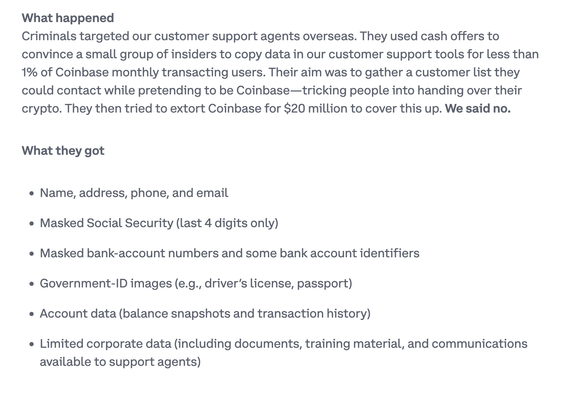
Less than 1% of monthly transacting users affected. Compromised data includes names, addresses, masked SSNs, bank details, gov ID images, and account history.
No private keys, credentials, or funds were accessed.
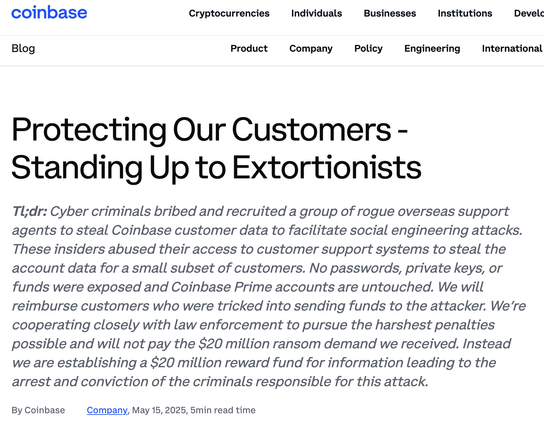
🚨 Breaking: Coinbase reveals insider threat incident where overseas support agents were bribed to exfiltrate customer data.
Company refusing $20M extortion demand, instead offering same amount as bounty for threat actor identification.
I cover stories like this every week in my free cybersecurity newsletter.
Join over 28,000 subscribers here:
There is no such thing as a backdoor only for the "good guys"
You can't have it both ways - either messages are truly E2EE or they're not.
Thanks 404media for this awesome reporting as usual:
https://www.404media.co/the-signal-clone-the-trump-admin-uses-was-hacked/
TeleMessage has wiped their website. (All links on the page are dead ends)
Multiple gov agencies including State Dept and CDC have active contracts with the company.
Worth noting: While cabinet members' messages weren't accessed, the trivial nature of the breach suggests more data could have been exposed if attacker chose to dig deeper.
Incident validates Signal's previous statement that they "cannot guarantee security properties of unofficial versions."
TeleMessage's claims about maintaining Signal's security were demonstrably false.
One screenshot showed 747 CBP officials in the system.
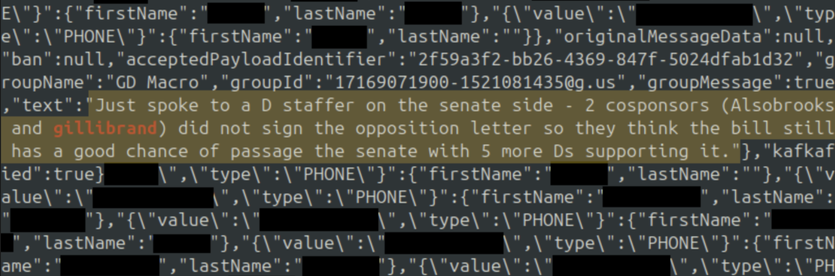
Data includes fragments of live communications, including sensitive discussions about pending crypto legislation.