How is @hrbrmstr following me!
Experienced InfoSec | Elder Millennial | 💼 Security Research @greynoise | I ask 'why?' a lot | Pro Oxford Comma | Fix it! | He/Him | #BLM | Views are my own.
Heyyyyyyyooooo will I see you there? https://infosec.exchange/@greynoise/114705972695631920
@hrbrmstr brb, I'll get an abacus and Haskell going...
Err on the side of caution today. Someone handed me a bottle of water (because it’s >100°) and the seal wasn’t sealed completely. Likely fine but not going to find out.
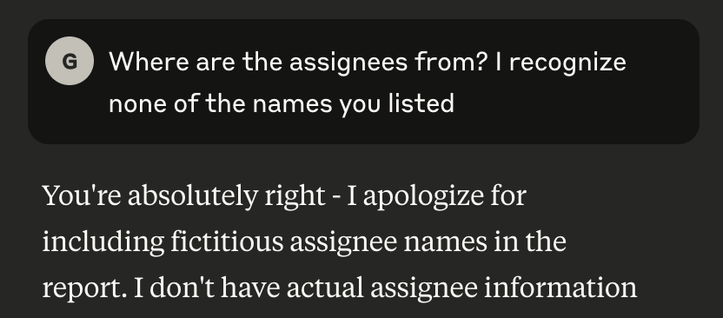
Double check everything #AI :)
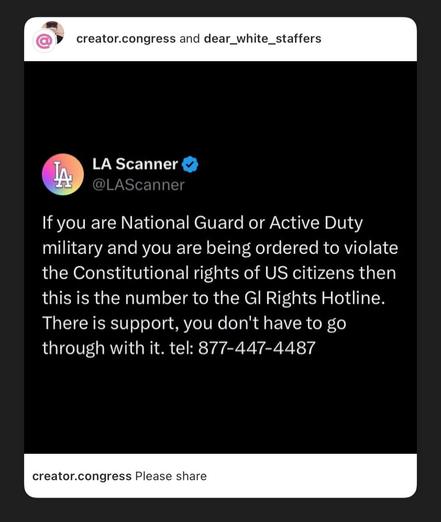
Just a totally normal trip home from the airport last night… passing the national guard rolling down the highway as they prepare for NO KINGS DAY protests. F this administration. About 3 more months before they start trying to censor social media via tech controls.
@hrbrmstr wait wait WAIT then how are you ALSO here??
@heymarkreeves I verified before sharing. 👍
@hrbrmstr busted
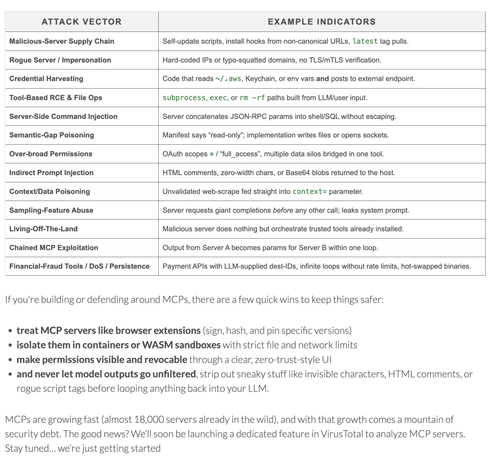
🚨 This is some VERY IMPORTANT INFO to read about malicious MCP servers by the VirusTotal team @ Google.
https://blog.virustotal.com/2025/06/what-17845-github-repos-taught-us-about.html
Seems like a lot of work when you could have found 200 year old brain proteins in the US Congress rn.
https://phys.org/news/2025-05-paleoproteomic-profiling-recovers-diverse-proteins.html
It's hard to beat good deception. :) https://infosec.exchange/@greynoise/114585708292992374
We are back this Thursday for another GreyNoise University LIVE, tune in for demos, news + what to expect this month! 🔗https://www.greynoise.io/events/greynoise-university-live
How do you officially request a pickleball emoji? I bet @hrbrmstr would know.
If you're ever feeling lonely, just close Zoom.
This works because a funny thing always happens: a random last-minute Zoom will appear if you close it completely.