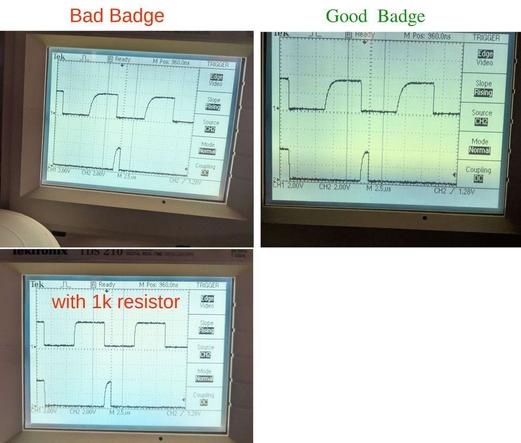
@cryptax @botconf @NorthSec j'ai pris l'avion lundi. L'équipe de logistique de NorthSec a fini le travail. Mais en effet dimanche à minuit je retournais des fûts de bière vide encore...
Botconf est incroyable ça vaut le détour! Et j'ai une copine merveilleuse de me permettre de faire ça.