Canada’s Bill C-2 is a Trojan horse, being pushed to align with U.S. surveillance demands. EFF joins the CCLA, OpenMedia & Citizen Lab in saying: Withdraw it. https://www.eff.org/deeplinks/2025/07/canadas-bill-c-2-opens-floodgates-us-surveillanc
Cybersecurity blue team person. Love to discuss urbanism, housing crisis and most "bigger-than-you" modern challenges. YIMBY. Involved with Construisons Montréal and Locomotion.app.
My story from Monday is here:
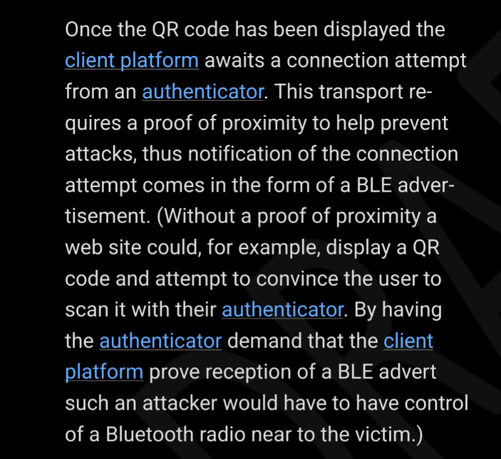
In short, the attack as originally described simply would not work against a FIDO2-compliant authentication system. Whatever system the researchers analyzed used a non-FIDO2 fallback in the event the user was unable to provide FIDO2-MFA. Calling this a bypass is like saying a door lock is insecure because an intruder could enter through a window. Lots of publications continue even now to say this was a bypass. It wasn't.
@dangoodin THANKS for covering this! I was frustrated when I read about it. The FIDO2 specification explicitely describes this exact scenario. Big oversight on them for not understanding the FIDO2 spec.
@blond11516 For someone who claims to be a meta employee like in my OP, it is
@spzb like meta does not need to do this at all, the benefit would not outweight the risk and cost! 🤷♂️
@blond11516 It's such a popular conspiracy it's kind of frustrating
@blond11516 if there is no LED, you still need to display a green dot. This is required by Android and enforced to manufacturers
https://support.google.com/android/answer/13532937?hl=en#:~:text=When%20your%20camera%20or%20microphone,to%20check%20our%20Android%20version.
https://source.android.com/docs/core/permissions/privacy-indicators
And if you don't have an always-on display, it's trivial to open settings and see that facebook did not, in fact, use the microphone
This misinformation sucks. When an app uses the microphone on Android, even a background app, the operating system turns a little LED above your screen on to let you know something is listening. I have never seen this open when my phone was closed and have not seen any credible report of it happening. Just anecdotes of people who don't understand that if you meet a friend and that friend has a new hobby and you talk about it and you see ads of it, it's not because of the mic, it's because facebook saw that you met that friend and the chances you talked about this is high.
We don't need to create false conspiracies to hate on Meta, there is enough real stuff already.
cc @scarpentier d'un coup que tu n'aies pas vu
Chronique absolument à lire par Patrick Lagacé - https://www.lapresse.ca/actualites/chroniques/2025-07-20/pistes-cyclables-contre-egouts.php #polmtl
The Canadian government cyber centre are this weekend recommending all orgs review historic logs for #CitrixBleed2 compromise, and reset all user sessions https://www.cyber.gc.ca/en/alerts-advisories/vulnerabilities-impacting-citrix-netscaler-adc-netscaler-gateway-cve-2025-5349-cve-2025-5777-cve-2025-6543
BleepingComputer article about the compromise https://www.bleepingcomputer.com/news/security/popular-npm-linter-packages-hijacked-via-phishing-to-drop-malware/
DLL SHA256: c68e42f416f482d43653f36cd14384270b54b68d6496a8e34ce887687de5b441
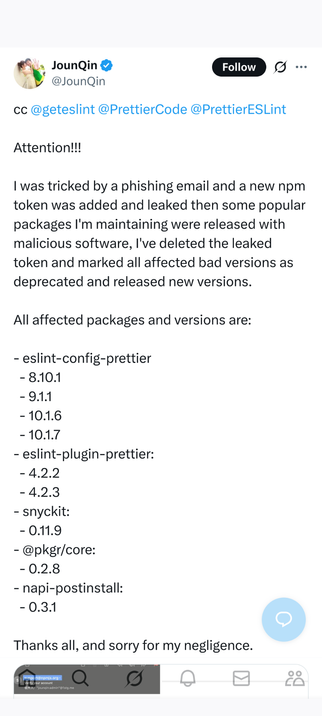
The owner of the package has addressed this on twitter: https://x.com/JounQin/status/1946297662069993690
Domain IOCs for the DLL:
firebase[.]su
dieorsuffer[.]com
smartscreen-api[.]com
3 other compromised packages:
pkgr/core v0.2.8
synckit v0.11.9
napi-postinstall v0.3.1
Same DLL.
Package eslint-plugin-prettier also has 2 malicious versions: v4.2.2 and v4.2.3. Same DLL.
Versions 8.10.1 and 9.1.1 are also malicious.
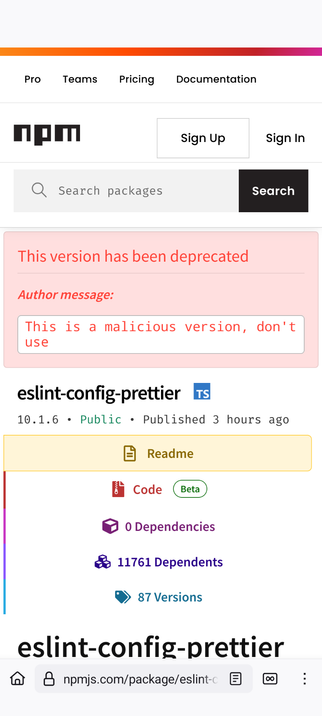
Version 10.1.8 is out and is not infected. If you have the capability, hunt for node-gyp.dll, it's the malicious DLL.
Widely used NPM package eslint-config-prettier has been compromised is dropping windows malware. Version 10.1.6 and 10.1.7 impacted. Beware!