Roger A. Grimes, CPA, CISSP, CEH, MCSE, CISA, CISM, CNE, yada, yada, Data-Driven Defense Evangelist for KnowBe4, Inc., is the author of 14 books and over 1400 articles on computer security, specializing in host security and preventing hacker and malware attacks. Roger is a frequent speaker at national computer security conferences and was the weekly security columnist at InfoWorld and CSO magazines between 2005 - 2019. He has worked at some of the world’s largest computer security companies, including, Foundstone, McAfee, and Microsoft. Roger is frequently interviewed and quoted in the media including Newsweek, CNN, NPR, and WSJ. His presentations are fast-paced and filled with useful facts and recommendations.
Linux Users Urged to Patch Critical Sudo Vulnerabilities. Allows unauthenticated users to get to root. One vuln has been present for over a decade. Can we, for forever, put to bed the whole "many eyes" theory that open source software is inherently stronger because it can be inspected more for bugs? Can and is is a vast ocean.
https://www.infosecurity-magazine.com/news/linux-users-urged-to-patch/
Vercel's v0 AI Tool Weaponized by Cybercriminals to Rapidly Create Fake Login Pages at Scale. It's not the first, but it's another in a long-line of tools that allow scammers to quickly create personalized fake logon pages on the fly
https://thehackernews.com/2025/07/vercels-v0-ai-tool-weaponized-by.html
Scammed Brit thought Jennifer Aniston was in love with him —and needed help paying her Apple bill. Sure, why not??
https://nypost.com/2025/07/02/us-news/scammed-brit-thought-jennifer-aniston-was-in-love-with-him/
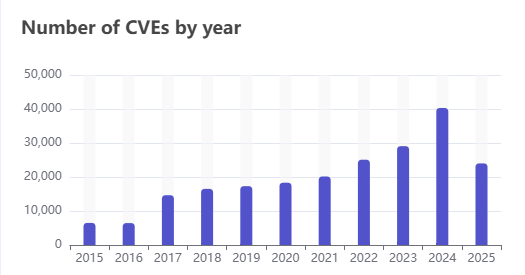
We are on schedule to have another recorded year of CVE's, just like most years. We had 40,200 vulns last year. We have nearly 24,000 so far this year, at just past half-of-the-year. https://www.cvedetails.com/browse-by-date.php
“The number of pieces of magic we still need is declining.” -engineer when describing the improvements in Ocean-2
Great quote I heard while watching a YouTube video on Ocean-2 (a new green energy device that uses sea power) https://www.youtube.com/watch?v=Q7Pmgq2JKbI (at the 9:58 mark)
I just loved it. It speaks to engineers solving tough problems on their way to a larger goal
@Cali I don't discount that conclusion
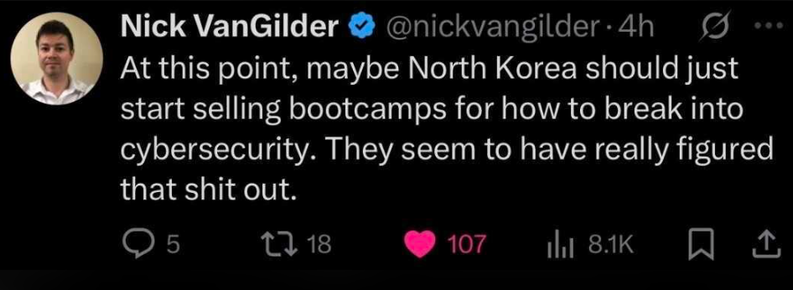
Several US-based North Korean fake employee laptop farms shut down, revealing over a hundred fake employees working at US companies.
Yeah, I won't be doing business with Hertz
@fedops You can, but it's not necessary. Use strong unique passwords or phishing-resistant MFA per site/serivce...that's enough
@blindcoder At least once a year...so that a stolen or guessed password doesn't stay good forever.
@mms Stephen Wolfram, Sean Carroll, Steve Gibson...I know lot more.
@welkin7 We wish. They should be, but aren't. It's terrible cybersecurity. It's people in the loop not taking their job seriously as they should be, led by management that doesn't take it seriously as they should (or severely unresourced so they can't do it right).
Sean Carroll, a popular and respected theoretical physicist, starting at 46:11, in a longer debate on string theory, says AI will not be able to meet general intelligence in the way we are making and using them now. He's not alone.
Pretty wild! Malware includes text strings to attempt to fool AI-enabled forensic tools. Yep, that's now a thing.
https://research.checkpoint.com/2025/ai-evasion-prompt-injection/
Hackers breach Norwegian dam, open valve at full capacity
https://risky.biz/risky-bulletin-hackers-breach-norwegian-dam-open-valve-at-full-capacity/