Linux folder Structure
Security Researcher
I believe the time has come to collect all my bug bounty tips and tricks into a PDF book. #bugbounty
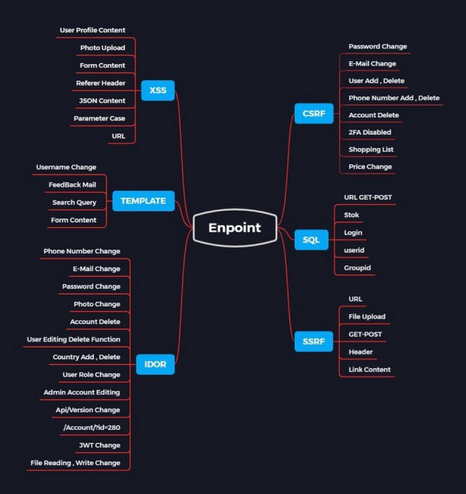
Cheat sheet for Endpoint Security #cybersecurity
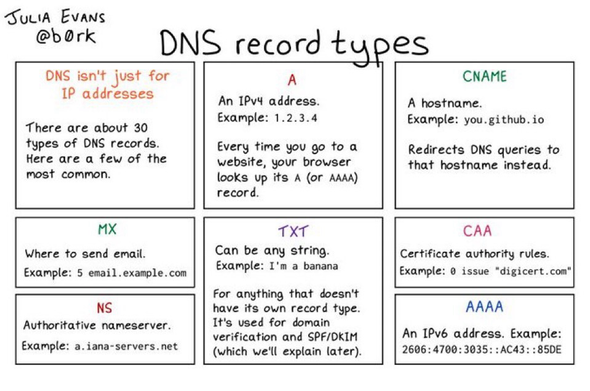
DNS Record Types
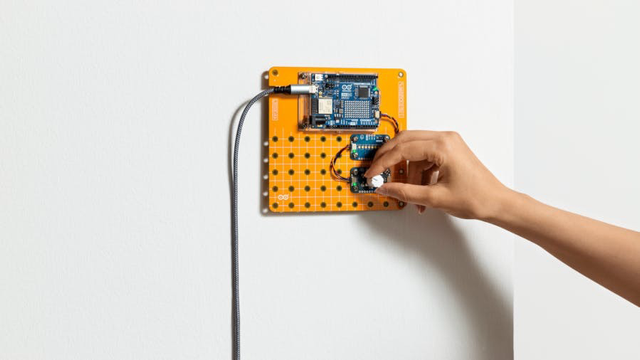
🚀 Dive into the world of physical computing with the new Arduino Plug and Make Kit! 🌟 Featuring the Arduino UNO R4 WiFi and quick-connect Modulino modules, it's never been easier to get started on your IoT journey. Perfect for makers of all ages! #Arduino #IoT #MakersMovement
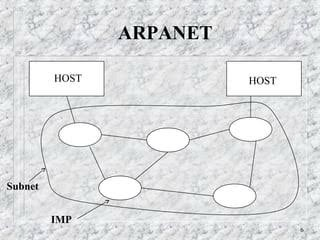
#ARPANET Computer Network!
What do you know about this computer ?
Share your thoughts!
Imperva File Security can detect ransomware activity, like a Wannacry attack, before it does widespread damage, using policy-based monitoring and deception technology. Imperva identifies suspicious file access behavior in real time, and quarantines infected users or devices which may be affected by ransomware. It also provides data that can help security teams investigate and report on ransomware activity.