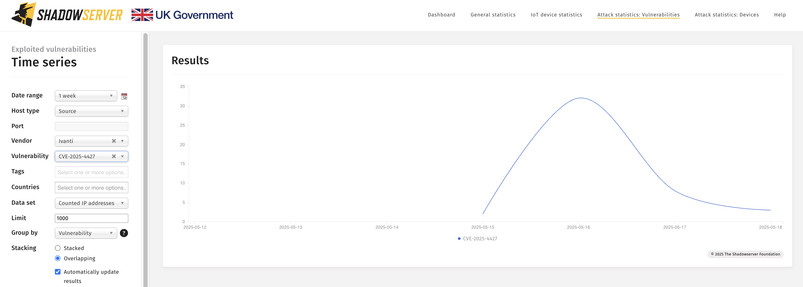
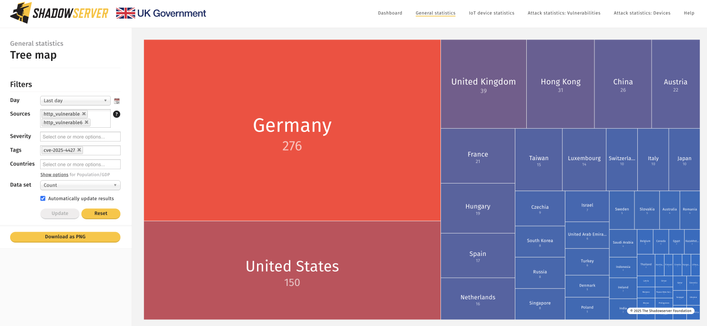
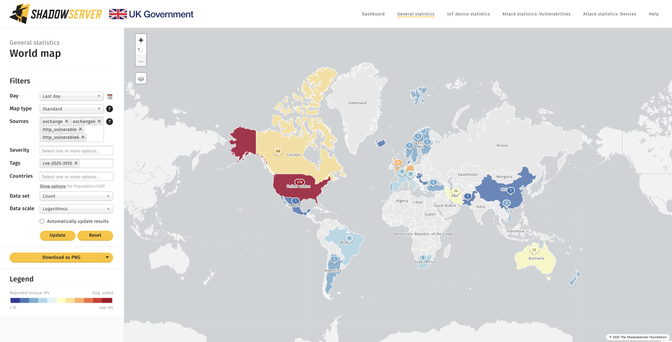
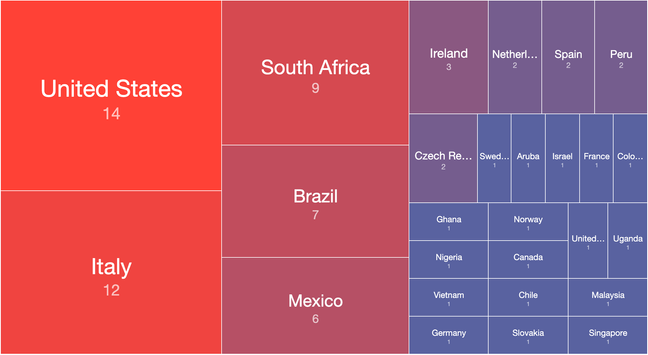
You can also track CVE-2025-4427 exploitation attempts as seen by our honeypot sensors on our Dashboard: https://dashboard.shadowserver.org/statistics/honeypot/vulnerability/time-series/?date_range=7&host_type=src&vendor=ivanti&vulnerability=cve-2025-4427&dataset=unique_ips&limit=1000&group_by=vulnerability&stacking=overlap&auto_update=on
Our mission is to make the Internet more secure by bringing to light vulnerabilities, malicious activity and emerging threats. Join our Alliance!
We are also scanning for Ivanti EPMM instances likely vulnerable (unpatched) to CVE-2025-4427 which can be chained with CVE-2025-4428 for RCE.
First scans found 940 instances (2025-05-15), down to 798 (2025-05-18).
IP data in https://shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/ tagged as 'cve-2025-4427'.
Detection is based on non-intrusive check provided by @watchtowrcyber
If you receive an alert, please make sure to review for any compromise - CVE-2025-4427/CVE-2025-4428 are exploited in the wild.
Patch info from Ivanti: https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Endpoint-Manager-Mobile-EPMM?language=en_US&_gl=1*1ylgtgu*_gcl_au*MTg5MTk4MDIzMC4xNzQ3MTU3OTQ1
Background on vulnerabilities:
https://labs.watchtowr.com/expression-payloads-meet-mayhem-cve-2025-4427-and-cve-2025-4428/
We’re excited to announce that CERT.LV (National CSIRT of Latvia) has joined the Shadowserver Alliance as a Bronze Tier Partner!
Together we will raise the bar on cybersecurity.
Read more about CERT.LV: https://cert.lv/en/
Become a Shadowserver Alliance partner today: https://www.shadowserver.org/partner/
We are sharing ScreenConnect instances likely vulnerable to CVE-2025-3935 (CVSS 8.1, versions 25.2.3 & earlier may be susceptible to a ViewState code injection).
Patch info: https://connectwise.com/company/trust/security-bulletins/screenconnect-security-patch-2025.4
685 instances still unpatched on 2025-05-07:
https://dashboard.shadowserver.org/statistics/combined/map/?date_range=other_value&day=2025-05-07&map_type=std&source=exchange&source=exchange6&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-3935%2B&data_set=count&scale=log
IP data tagged 'cve-2025-3935' in our Vulnerable HTTP report https://shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
We are sharing SysAid instances likely vulnerable to CVE-2025-2775, CVE-2025-2776, CVE-2025-2777 (XXEs) any of which combined with CVE-2025-2778 allows for RCE.
77 IPs found unpatched so far (version check).
Install updates from SysAid (from March!) https://documentation.sysaid.com/docs/24-40-60
IP data for your network shared in our Accessible HTTP https://shadowserver.org/what-we-do/network-reporting/accessible-http-report/ & Accessible SSL https://shadowserver.org/what-we-do/network-reporting/accessible-ssl-report/ reports with 'sysaid-vulnerable' tag.
Starting tomorrow data will be in our Vulnerable HTTP report with 'cve-2025-2775' tag https://shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
We would like to thank
@watchtowrcyber for the collaboration!
Background: https://labs.watchtowr.com/sysowned-your-friendly-rce-support-ticket/
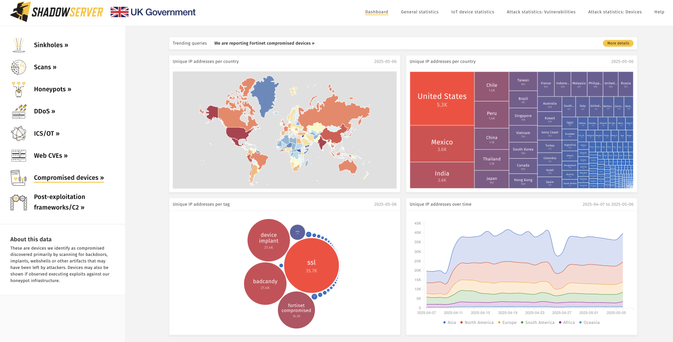
Check out our latest Dashboard updates that now highlight compromised devices & post-exploitation frameworks/C2s discovered in scans, as well as various functionality improvements:
https://dashboard.shadowserver.org/#compromised-devices
https://dashboard.shadowserver.org/#post-exploitation-frameworks
A big thank you to the UK Foreign, Commonwealth & Development Office for the funding that enabled the work.
As a reminder we have 76 languages supported!
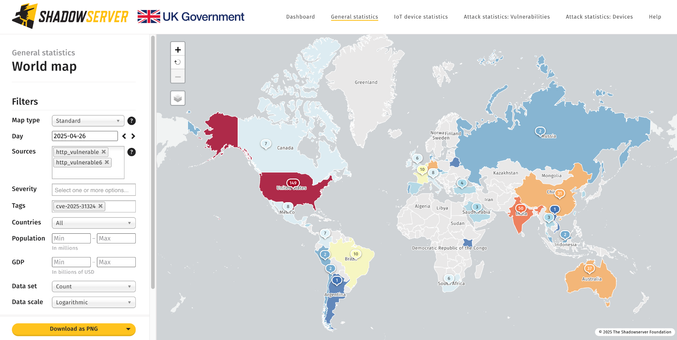
Attention! We are sharing SAP NetWeaver instances vulnerable to CVE-2025-31324 unauth upload (CVSS 10.0). 454 IPs found vulnerable on 2025-04-26. If you receive an alert from us, make sure to check for signs of compromise (incl. webshells).
Patch info from SAP: https://me.sap.com/notes/3594142
Data in https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
Top affected - US 149, India 50, Australia 37: https://dashboard.shadowserver.org/statistics/combined/tree/?day=2025-04-26&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-31324%2B&geo=all&data_set=count&scale=log
CVE-2025-31324 tracker: https://dashboard.shadowserver.org/statistics/combined/time-series/?date_range=7&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-31324%2B&dataset=unique_ips&limit=1000&group_by=geo&style=stacked
Background details on CVE-2025-31324: https://redrays.io/blog/critical-sap-netweaver-vulnerability-cve-2025-31324-fixed-actively-exploited-in-the-wild/
We’re excited to announce that Identity Digital has joined the Shadowserver Alliance as a Bronze Tier Partner!
Together we will work to make the Internet safer and more secure.
Read more about Identity Digital:
https://www.identity.digital/company
Become a Shadowserver Alliance partner today:
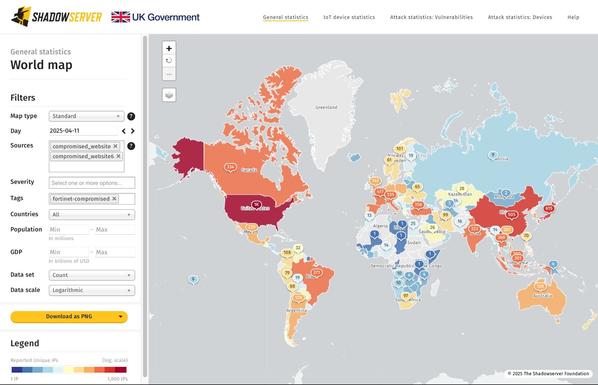
Attention!
Check your Compromised Website Report for critical events tagged “fortinet-compromised” and follow Fortinet's mitigation advice on compromised devices:
https://www.fortinet.com/blog/psirt-blogs/analysis-of-threat-actor-activity
Data available from 2025-04-11+
https://shadowserver.org/what-we-do/network-reporting/compromised-website-report/
Detected compromised Fortinet devices:
National CSIRT advisories:
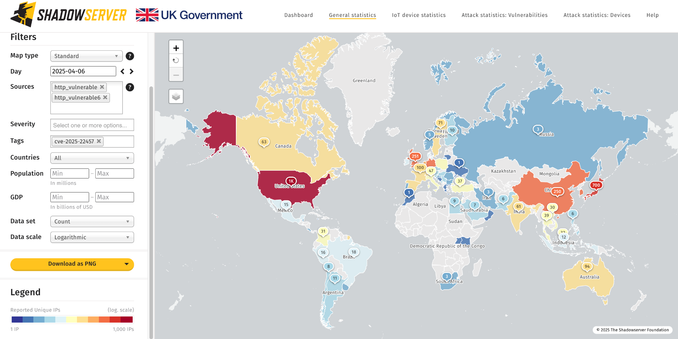
Ivanti Connect Secure CVE-2025-22457 (stack-based buffer overflow allowing for unauth RCE): we see over 5113 instances unpatched in our scan for 2025-04-06. This vulnerability has been observed exploited in the wild and is on US CISA KEV.
IP data shared in our Vulnerable HTTP report tagged 'cve-2025-22457'. As part of work on tagging this vuln, we improved our fingerprinting of Ivanti Connect Secure with a little help from some friends!
https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
CVE-2025-22457 tracker: https://dashboard.shadowserver.org/statistics/combined/time-series/?date_range=7&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-22457%2B&dataset=unique_ips&limit=1000&group_by=geo&style=stacked
Ivanti advisory and patch info: https://forums.ivanti.com/s/article/April-Security-Advisory-Ivanti-Connect-Secure-Policy-Secure-ZTA-Gateways-CVE-2025-22457?language=en_US
Note that according to Ivanti, the vulnerability was patched in a Feb 11, 2025 release. However, a large set of what is affected are older Pulse Connect Secure 9.x (end-of-support as of December 31), without a patch.
We are observing CrushFTP CVE-2025-2825 exploitation attempts based on publicly available PoC exploit code. You can track attempts on our Dashboard at https://dashboard.shadowserver.org/statistics/honeypot/vulnerability/time-series/?date_range=7&host_type=src&vendor=crushftp&vulnerability=cve-2025-2825&dataset=unique_ips&limit=1000&group_by=geo&style=stacked
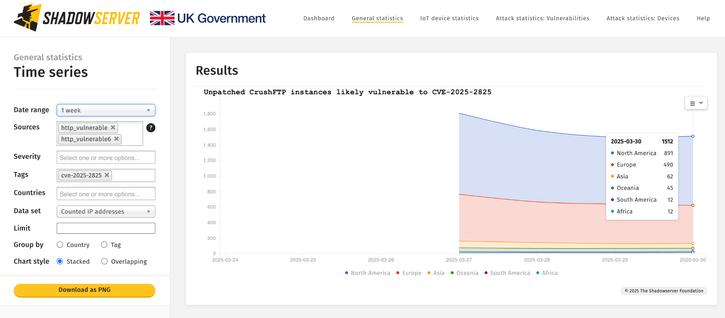
Still 1512 unpatched instances vulnerable to CVE-2025-2825 seen on 2025-03-30
CrushFTP versions 10.0.0 through 10.8.3 and 11.0.0 through 11.3.0 are affected. Make sure to check for signs of compromise and update: https://crushftp.com/crush11wiki/Wiki.jsp?page=Update
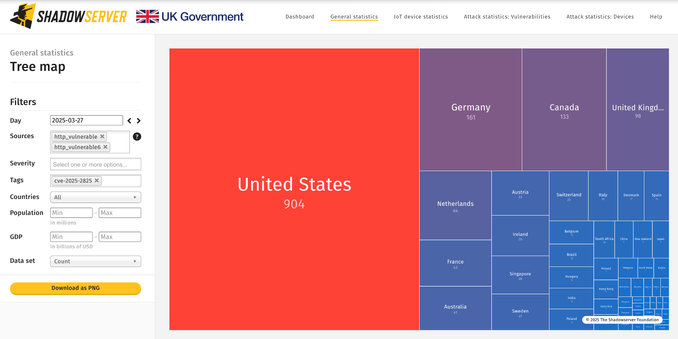
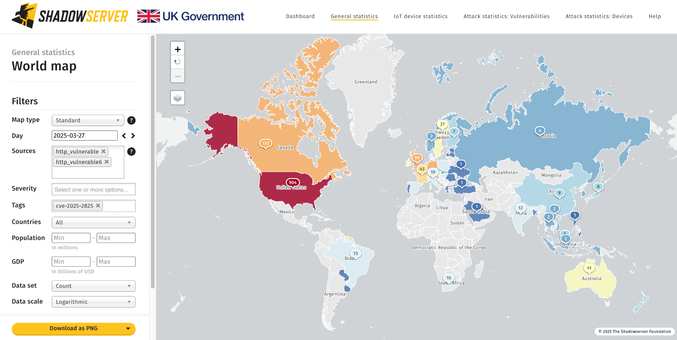
We are sharing unpatched CrushFTP instances likely vulnerable to CVE-2025-2825 (CVSS 9.8) that may allow unauthenticated remote attackers to bypass authentication via HTTP(S) requests. We see ~1800 unpatched instances worldwide, with over 900 in the US.
World map of vulnerable instances: https://dashboard.shadowserver.org/statistics/combined/map/?map_type=std&day=2025-03-27&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-2825%2B&geo=all&data_set=count&scale=log
IP data shared in our Vulnerable HTTP report, tagged 'cve-2025-2825': https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
CrushFTP versions 10.0.0 through 10.8.3 and 11.0.0 through 11.3.0 are affected. Make sure to update: https://www.crushftp.com/crush11wiki/Wiki.jsp?page=Update
Tree map geo breakdown: https://dashboard.shadowserver.org/statistics/combined/tree/?day=2025-03-27&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-2825%2B&geo=all&data_set=count&scale=log
Switch on automatic updates if possible
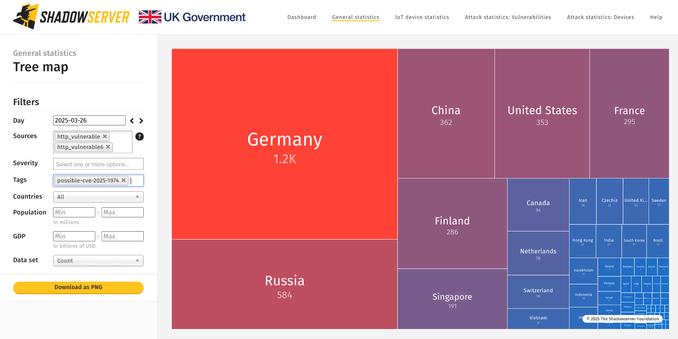
For the last few days we are also scanning & reporting out exposed Ingress NGINX Controller for Kubernetes (Admission Controller feature). These may possibly be also vulnerable to CVE-2025-1974 & other recently disclosed vulnerabilities.
We see around 4000 IPs exposed.
Data is shared in the Vulnerable HTTP report & tagged as `possible-cve-2025-1974`. Note that the validating Admission Controller should not be exposed to the Internet regardless of any additional vulnerabilities! We also report these out in our Device Identification report.
Vulnerable HTTP report: https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
Device Identification (device model is set to Kubernetes Admission Controller): https://www.shadowserver.org/what-we-do/network-reporting/device-identification-report/
Dashboard tree map view: https://dashboard.shadowserver.org/statistics/combined/tree/?day=2025-03-26&source=http_vulnerable&source=http_vulnerable6&tag=possible-cve-2025-1974%2B&geo=all&data_set=count&scale=log
Patch info: https://kubernetes.io/blog/2025/03/24/ingress-nginx-cve-2025-1974/
Background: https://www.wiz.io/blog/ingress-nginx-kubernetes-vulnerabilities
We are excited to welcome Arctic Security @arcticsecurity to the Shadowserver Alliance (Silver tier)!
We look forward to this partnership to raise the bar on cybersecurity.
Learn more about Arctic Security: https://arcticsecurity.com
Become a Shadowserver Alliance Partner today: https://www.shadowserver.org/partner/
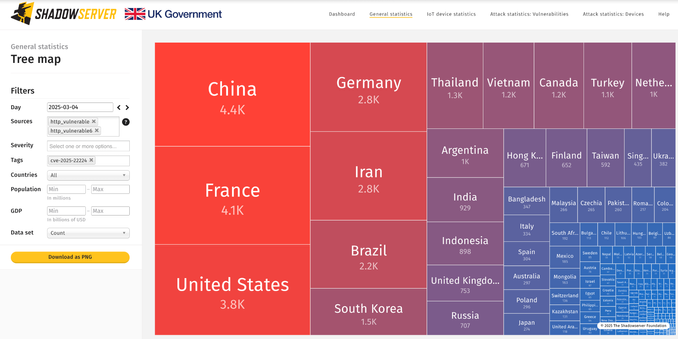
We are scanning & reporting out VMware ESXi CVE-2025-22224 vulnerable instances ("a malicious actor with local admin privileges on a virtual machine may exploit this to execute code as virtual machine's VMX process running on host").
Nearly 41.5K found vulnerable on 2025-03-04.
IP data shared in our Vulnerable HTTP report, tagged 'cve-2025-22224' : https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
Dashboard tree map breakdown: https://dashboard.shadowserver.org/statistics/combined/tree/?day=2025-03-04&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-22224%2B&geo=all&data_set=count&scale=log
Track patching progress here: https://dashboard.shadowserver.org/statistics/combined/time-series/?date_range=7&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-22224%2B&dataset=unique_ips&style=stacked
This vulnerability is known to be exploited in the wild and on @cisacyber KEV list: https://www.cisa.gov/known-exploited-vulnerabilities-catalog
Patch info from Broadcom: https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/25390
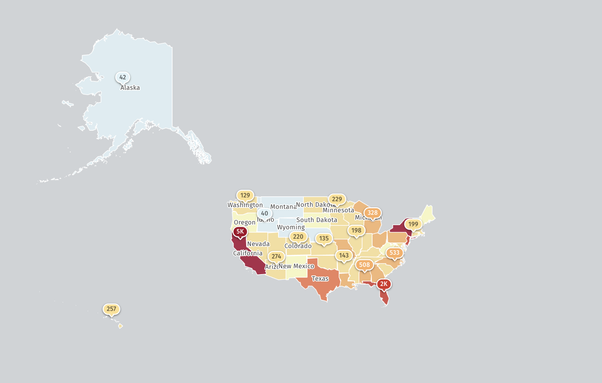
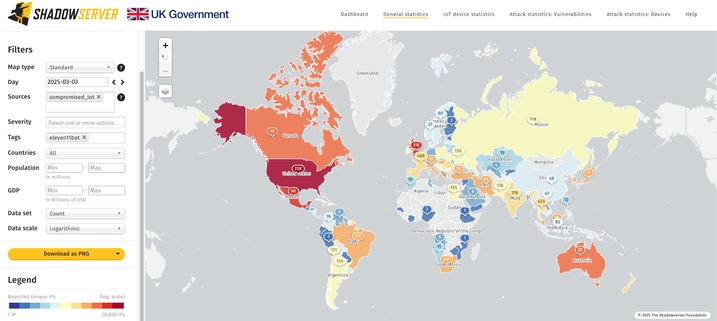
We started scanning for IoT devices compromised by the Eleven11bot DDoS botnet, with ~86.4K discovered on 2025-03-03. IP data is shared daily in our Compromised IoT report https://www.shadowserver.org/what-we-do/network-reporting/compromised-iot-report/
Top affected: US (24.7K), UK (10.8K).
Dashboard map view: https://dashboard.shadowserver.org/statistics/combined/map/?map_type=std&day=2025-03-03&source=compromised_iot&tag=eleven11bot%2B&geo=all&data_set=count&scale=log
For background, please see Nokia Deepfield Emergency Response Team (ERT) @deepfield announcement: https://infosec.exchange/@deepfield/114086567369833954
Dashboard breakdown by US state:
We are scanning for & reporting Nakivo Backup & Replication CVE-2024-48248 (arbitrary file read) vulnerable instances in our Vulnerable HTTP report: https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/.
~208 vulnerable instances seen 2025-02-26
Data is tagged 'vulnerable-nakivo-backup' since 2025-02-13 thanks to @watchtowrcyber
We have also added the 'cve-2024-48248' tag as well today.
If you run Nakivo, make sure to update your instance to the latest version! (vulnerability was silently patched 2024-11-04).
For an in-depth analysis of the vulnerability, please read the @watchtowrcyber blog at https://labs.watchtowr.com/the-best-security-is-when-we-all-agree-to-keep-everything-secret-except-the-secrets-nakivo-backup-replication-cve-2024-48248/
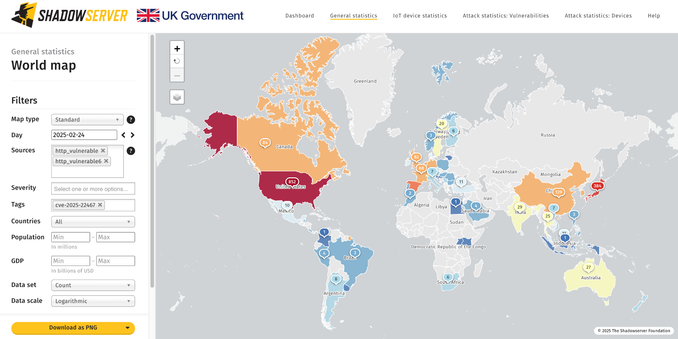
We started scanning & reporting out Ivanti Connect Secure CVE-2025-22467 vulnerable (unpatched) instances in our daily feeds. ~2850 IP seen unpatched worldwide in our daily scans.
Top affected: US (852) & Japan (384)
Dashboard world map view: https://dashboard.shadowserver.org/statistics/combined/map/?map_type=std&day=2025-02-24&source=http_vulnerable&source=http_vulnerable6&tag=cve-2025-22467%2B&geo=all&data_set=count&scale=log
CVE-2025-22467 is stack-based buffer overflow in Ivanti Connect Secure before version 22.7R2.6 allows a remote authenticated attacker to achieve remote code execution.
This is a version based check.
See advisory from Ivanti on this & other vulns: https://forums.ivanti.com/s/article/February-Security-Advisory-Ivanti-Connect-Secure-ICS-Ivanti-Policy-Secure-IPS-and-Ivanti-Secure-Access-Client-ISAC-Multiple-CVEs?language=en_US
We share IP level data on CVE-2025-22467 in our Vulnerable HTTP report for your network/constituency: https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-http-report/
Not receiving our free daily feeds? Subscribe here: https://www.shadowserver.org/what-we-do/network-reporting/get-reports/
At last week’s UN #OEWG on ICT,
@shadowserver and
@globalcyberalliance represented
@commongoodcyber on a panel discussing “Cybersecurity for the Common Good: Strengthening Nonprofits Engagement in a Permanent UN Mechanism on ICT Security” hosted by @EU_ISS
Read more about Common Good Cyber: https://commongoodcyber.org
@WACREN We are excited to collaborate with WACREN
and Deutsche Gesellschaft für Internationale Zusammenarbeit (GIZ) GmbH on our joint project to strengthen the cyber resilience, situational awareness and incident response of the West African research & education sector!