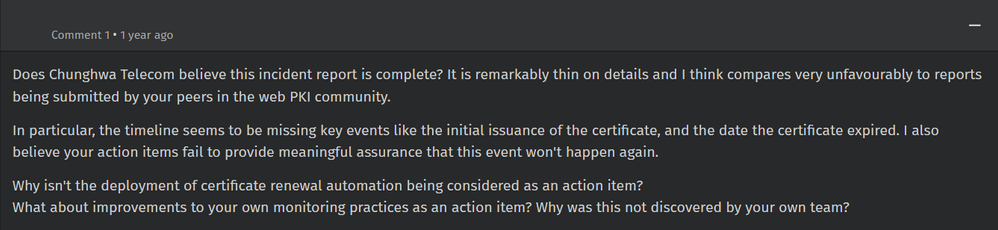
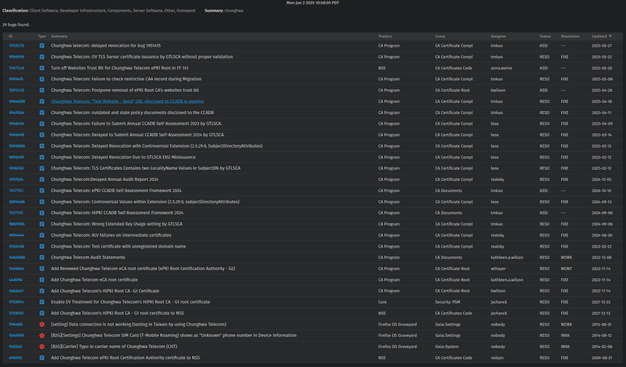
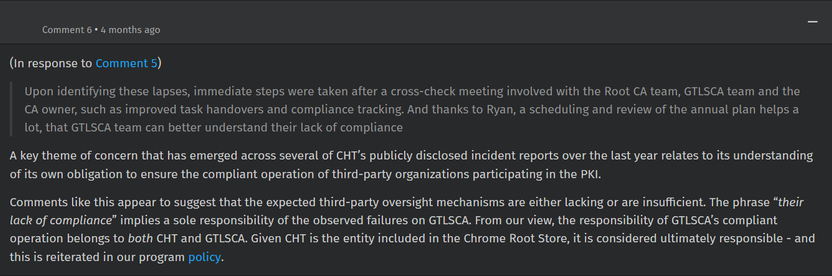
The Taiwan Ministry of Digital Affairs (MoDA) has issued a press release today stating that MoDA was made aware of CHT's improper conduct in March, and have since begun migrating to another Root CA provider (possibly Taiwan CA, another major Root CA that had worked with TW govs).
Meanwhile, CHT has also published a statement and attempting to downplay the situation by claiming "only" Chrome is affected and none of the other browsers like Apple's and Microsoft's (curiously, Firefox was not explicitly mentioned), and that they are "attempting to work with Chrome to get Root CA trust back in March 2026."
Source:
https://newtalk.tw/news/view/2025-06-03/974334
https://www.cht.com.tw/home/enterprise/news/latest-news/2025/0602-1810