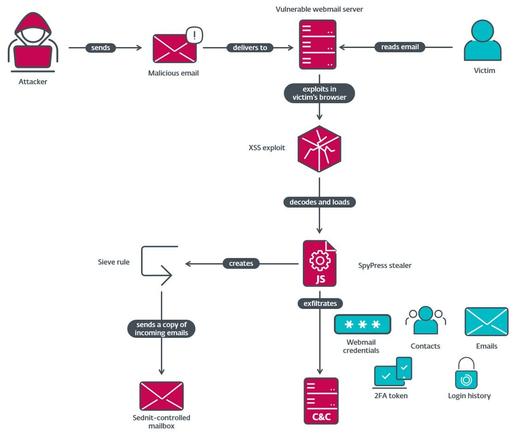
#ESETresearch publishes its investigation of Operation RoundPress, which uses XSS vulnerabilities to target high-value webmail servers. We attribute the operation to Sednit with medium confidence. https://www.welivesecurity.com/en/eset-research/operation-roundpress/
In 2023, Operation RoundPress only targeted Roundcube, but in 2024 it expanded to other webmail software including Horde, MDaemon, and Zimbra.. For MDaemon, Sednit exploited the zero-day XSS vulnerability CVE-2024-11182.
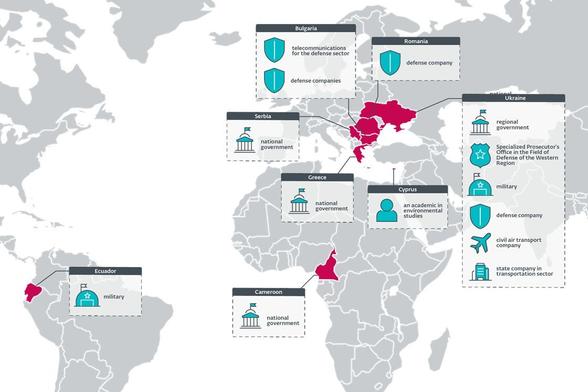
Most victims were governmental entities and defense companies in Eastern Europe, although we have observed governments in Africa, Europe, and South America being targeted as well.
Our blogpost provides an analysis of the JavaScript payloads, which we named SpyPress. They are able to steal webmail credentials, and exfiltrate contacts and email messages from the victim’s mailbox. IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/operation_roundpress 5/5
Threats n stuff.
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: https://volatilityfoundation.org/announcing-the-official-parity-release-of-volatility-3/
In the course of its investigations, @volexity frequently encounters malware samples written in Golang. This reflects the increase in popularity of the Golang generally, and presents challenges to reverse engineering tools.
Today, @volexity is releasing GoResolver, open-source tooling to help reverse engineers understand obfuscated samples. @r00tbsd & Killian Raimbaud presented details at INCYBER Forum earlier today.
GoResolver uses control-flow graph similarity to identify library code in obfuscated code, leaving analysts with only malware functions to analyze. This saves time & speeds up investigations!
Check out the blog post on how GoResolver works and where to download it: https://www.volexity.com/blog/2025/04/01/goresolver-using-control-flow-graph-similarity-to-deobfuscate-golang-binaries-automatically/
#dfir #reversing #malwareanalysis
In this blog post, Michael Hale Ligh & Andrew Case (@attrc) break down how @volexity used #memoryforensics to discover two #0days being chained together to achieve unauthenticated remote code execution in Ivanti Connect Secure VPN devices. More details here: https://www.volexity.com/blog/2024/02/01/how-memory-forensics-revealed-exploitation-of-ivanti-connect-secure-vpn-zero-day-vulnerabilities
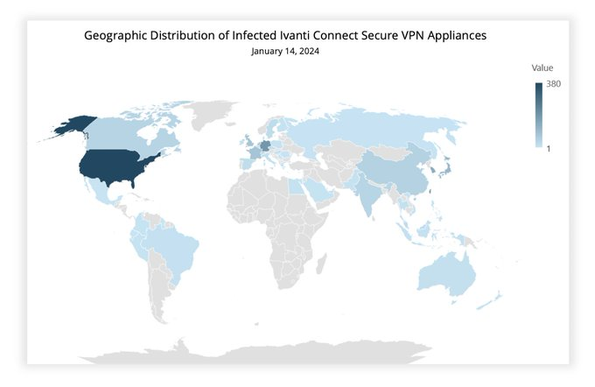
Last week, we shared details concerning a threat actor (UTA0178) exploiting #Ivanti Connect Secure 0-days. Initially few devices were compromised. Since Thursday the exploitation goes global. We identified over 1700 compromised appliances in the world.
All the sectors are concerned: small and big organizations. Private and public sectors. If you haven't already done, apply the mitigation provided by the vendor. Run the integrity checker tool to check if you have any mismatches... More details: https://www.volexity.com/blog/2024/01/15/ivanti-connect-secure-vpn-exploitation-goes-global/
End of last year we worked on an incident response where a TA exploited 2 0-days to compromised Ivanti Connect Secure (previously Pulse Connect Secure).
The first vulnerability (CVE-2023-46805) was abused to bypass the authentication. The second vulnerability (CVE-2024-21887) was used to execute commands on the device.
The TA remount the filesystem to enable the write permissions. Then, the attackers modified an existing JavaScript and deployed two webshells.
They modified lastauthserverused.js, a script that is legitimately used in the logon page. The modification exfiltrates the username and the password. The two webshells use the HTTP request parameters to execute code.
Takeovers: monitor your network (outbound connections via curl was perfected on multiple occasion), check your logs (store your logs outside of the appliance via syslog), use the in-build integrity checker tool.
More details & IOCs in our blog post: https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/
@volatility New Release: #volatility3 v2.5.0 - visit https://github.com/volatilityfoundation/volatility3/releases for details and downloads.
Don't miss @tlansec's talk at 12:00 BST tomorrow, Oct 5, at #VB2023 in London! He will share @volexity's research and observations of a North Korean #apt using unique, persistent #socialengineering techniques to target victims. More here: https://www.virusbulletin.com/conference/vb2023/abstracts/sharptongue-pwning-your-foreign-policy-one-interview-request-time/ #threatintel #dfir
ICYMI, on Friday our team @volexity put out a report on APT activity targeting mobile devices (Android and likely iOS). The attackers distributed the malware by creating purpose-built websites, online communities and fake personas to assist in distribution.
https://www.volexity.com/blog/2023/09/22/evilbamboo-targets-mobile-devices-in-multi-year-campaign/
@volexity's #theatintel team works with some of the most targeted groups in the world. Today, at the LABScon conference, we are sharing details of a long-running campaign by EvilBamboo. We have also just published details on our blog: https://www.volexity.com/blog/2023/09/22/evilbamboo-targets-mobile-devices-in-multi-year-campaign/.
Our analysis has uncovered evidence of the attacker building online communities on various social media & messaging platforms, creating fake personas on social media sites, and using other #socialengineering techniques in order to distribute #Android malware, including #BADBAZAAR. Additionally, there is strong evidence of #iOS device targeting and likely exploitation using IRONSQUIRREL.
Donut, an open-source project, is a set of tools to generate position-independent code to obfuscate, load & execute embedded/remote payloads. Today, @volexity released "donut-decryptor" to help analyze payloads created with Donut: http://github.com/volexity/donut-decryptor
The Volexity donut-decryptor tool, created by Sr. Malware Reverse Engineer @oldetymer, consists of a Python module + a command-line utility for enabling simple usage. Both the tool and cipher implementation are available for download.
If you were a user of the
@volexity onenoteextractor project, please note that we've moved it into its own dedicated repository here now:
#Microsoft has published an advisory with mitigation guidance related to an actively exploited remote code execution vulnerability in Microsoft Office now covered by CVE-2023-36884. @volexity's #threatintel team identified this zero-day, related infrastructure, and malware and is credited in the report: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36884
Volexity recommends following Microsoft's mitigation advice ASAP until a patch is made available.
If you missed it yesterday, Microsoft released an advisory concerning the CVE-2023-36884: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36884. This RCE is currently used by a TA and there is no patch. You should apply the mitigation described in the advisory.
With @tlansec we suspected a 0d and we notified MS few days ago. The infection chain was insane... Instead of a endless explanation you can check this graphic.
The final stage was a malware we named PEAPOD. It shares similarities with RomCom RAT such as COM object hijacking, the string obfuscation logic, the C2 channel protocols (ICMP/socket/HTTP). But the malware core and the final stage are different. PEAPOD works with two libraries: 1 stored on disk (you should monitor what happens inside %PUBLIC%) and 1 stored in the registry. They are loaded in memory and communicate together via a named pipe.
The perfect confirmation dialog does not exist…
The @volexity #threatintel team continues to see various #threatactors using Microsoft OneNote (.one) files to distribute #malware, sometimes password-protecting them to avoid analysis. We have updated our one-extract tool to support password-encrypted notebooks: https://github.com/volexity/threat-intel/tree/main/tools/one-extract.
On Wednesday, May 10th (next week), Tom Lancaster and I will be in Reston presenting some of our latest research at Volexity’s next Cyber Session. The event is free to attend, and will be in a very relaxed atmosphere. Full details here:
https://www.meetup.com/volexity-cyber-sessions/events/291852488/
The @volatility in-person Malware & Memory Forensics Training is filling up! All course material is based on the instructors’ experience detecting + responding to some of the most sophisticated threat groups in the world. More details here: https://volatility-labs.blogspot.com/2023/01/the-return-of-in-person-volatility-malware-and-forensics-training.html
We're learning some important opsec lessons from Teixeira. For instance, if you want to clandestinely show your internet friends pics of Top Secret files, don't do it on your own Discord server that you paid for with your credit card that has your name and home billing address.
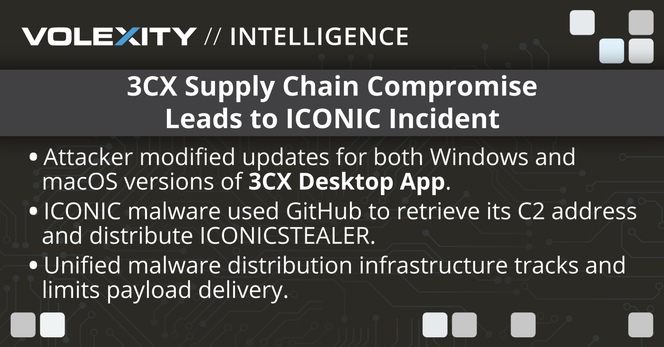
The @volexity #threatintel team takes a look at the #3CX supply chain compromise: the malware delivered, the infrastructure used & the initial set up of the attack. Here's what we know so far: https://www.volexity.com/blog/2023/03/30/3cx-supply-chain-compromise-leads-to-iconic-incident/
#dfir