@hacktobeer Hahaha perfect, I'm pretty sure a lot of people will be in agreement. Maybe the discount should be capped?
@benmontour no worries at all! Thanks for putting time into this. Sounds pretty cool, looking forward to what you’re coming up with!
@benmontour Here's the link! https://github.com/yeti-platform/yeti/discussions/919
@benmontour hey! That’s a very good point. We have some normalization requirements (like having “source” in context, which you’ve fixed- thanks for that :)) but other than that not really. Even the links between entities are a bit free form; the idea was to stay very flexible. I’d say let’s move this to a GitHub discussion to see where we’re lacking and what we can bring in.
@benmontour sure thing! Thanks for bringing it up :)
@benmontour hey, thanks a lot! This sounds like a bug indeed, you’re supposed to be able to do exactly that (attribute=blah). It’s probably because we do a 1:1 match and not really a substring search. Do you mind opening an issue in the repo so we can track it? https://github.com/yeti-platform/yeti/issues otherwise I’ll get to it tomorrow. Thanks!!
Please feel free to use (and tell us when you do! we love hearing about people's use-cases), file lots of bugs, and feel free to contribute: guides, documentation, even cool screenshots, everything is welcome.
We are looking forward to integrating formats such as https://dfiq.org, shipping tighter integrations with DFIR platform tools like
@TimesketchProj,
@TurbiniaProj and CTI platforms like @MISPProject
(and hopefully many more!)
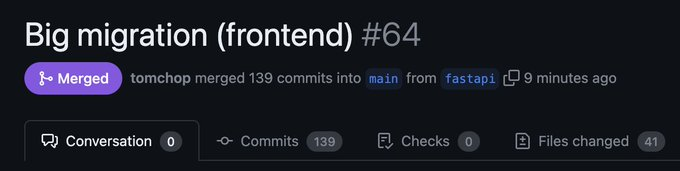
139 commits to the frontend SPA
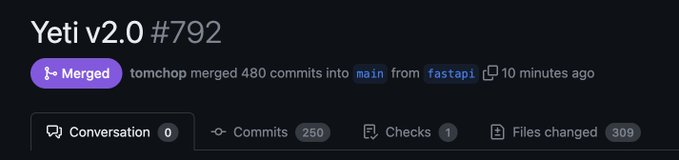
The changes in the codebase have been massive (remember, it's only 2 people working on this): 480 commits to the API server
This version marks the start of a focus shift away from classic CTI and towards a platform for DFIR teams wishing to integrate CTI in their pipelines for incident response, threat hunting, and detection, and to be able to collate "forensics intelligence" to share with other teams.
This has been years in the making, literally.
@sebdraven
and I are happy to announce the release of #Yeti 2.0 ✨ 🍰 (after we promised an EOM release at
@hack_lu
last month 😅)
Website: https://yeti-platform.io
Release: https://github.com/yeti-platform/yeti/releases/tag/2.0
mini-🧵👇🏼
@Sebdraven @hack_lu We're also running a workshop about it two days later. https://pretalx.com/hack-lu-2023/talk/7G8EKN/, in case you wanna see all this in action!
I haven't had time to talk about it, but @Sebdraven and I are giving a talk this week at @hack_lu about some cool new changes coming to Yeti: https://pretalx.com/hack-lu-2023/talk/JAKAKS/
It's going to be fun to talk about this project that has been on my todo list for 10+ years! 😅 #DFIR
@iaintshootinmis Thanks! The github is here: https://github.com/google/dfiq. I've asked about the PR process, and was told it was being worked on :)
My team just released https://dfiq.org, which is "a collection of Digital Forensics Investigative Questions and the approaches to answering them."
The idea came from the will to organize investigative approaches to similar cases to increase consistency across response efforts. #dfir #infosec
I'm very excited to announce the release of #Yeti 2.0-Alpha. Yeti is undergoing major changes, one of them is a ✨brand new ✨ frontend based on VueJS.
Please feel free to take it for a spin, but don't take it too seriously: many more improvements are to come! 🚀 #CTI #DFIR #Automation #threatintel
https://github.com/yeti-platform/yeti/releases/tag/2.0-Alpha
hack.lu 2023 - 16-19 October 2023 is back and will take place physically in Luxembourg. The call for papers/presentation is now open and we will be glad to receive your proposals.
🔗 CfP : https://pretalx.com/hack-lu-2023/
🔗 https://2023.hack.lu/
@martijn_grooten Thanks for the great talk! I’d love to chat a bit more about all you’re doing. I’ll be around all three days of the conference :)
Given that I woke up at 6:30 to catch a train, this year's #NapChallenge might be a bit harder than usual. (or easier for @saadk)