@jnkrtech Thank you!
Hacker at heart | Discovered KRACK and FragAttacks | Prof. Computer Science at @KU_Leuven (Belgium) | Did Postdoc at NYUAD | Network Security & Applied Crypto | Open to consultancy
Our research on open tunneling servers got nominated for the Most Innovative Research award :)
The work will be presented by Angelos Beitis at Black Hat and also at USENIX Security
Brief summary and code: https://github.com/vanhoefm/tunneltester
Paper: https://papers.mathyvanhoef.com/usenix2025-tunnels.pdf
Disclosure timeline is on X/twitter: reported in 2012, but no real response because it was considered theoretical. They weren't given access to a train's test track facility, so impossible to confirm ethically in practice. Devices now considered end of life. Replacement is maybe here in 2027..
Yikes. Turns out you can send a plaintext radio signal to cause any train in the USA to do an emergency break. The original 'security' was just a checksum, no encryption or authentication. Reporting this took them 12 years (!) because the vendor dismissed it initially https://www.cisa.gov/news-events/ics-advisories/icsa-25-191-10
The attempts by law enforcement & governments to subvert end-to-end encryption are ongoing. The European Commission is going to spend a year thinking about their new "Roadmap for law enforcement access to data", and they are (genuinely) asking for people to join their expert group to help. Here I urge you to join that group (also because I can't): https://berthub.eu/articles/posts/possible-end-to-end-to-end-come-help/
Reminder to apply to be part of the artifact evaluation committee of NDSS'26! And share with your colleagues :) We'll likely close this form around the end of next week. https://docs.google.com/forms/d/e/1FAIpQLSdQGc5NsZnYqEW7MQw4ciXOc0UIIP4cxSo82WQxJpej42qlKA/viewform
All papers should publish their code. Help realize this by becoming an artifact reviewer at NDSS'26, apply here: https://docs.google.com/forms/d/e/1FAIpQLSdQGc5NsZnYqEW7MQw4ciXOc0UIIP4cxSo82WQxJpej42qlKA/viewform
You'll get to review artifacts of accepted top papers. We especially encourage junior/senior PhD students & PostDocs to help.
Awards will be given to distinguished reviewers.
@FritzAdalis The more pages, the faster the Wi-Fi!
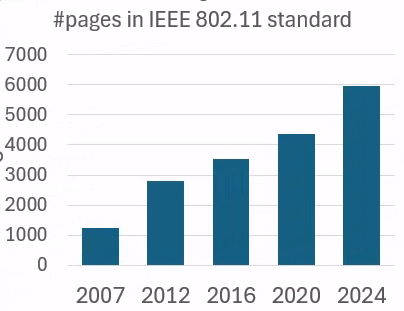
New version of the IEEE 802.11 standard that underpins Wi-Fi has been released. A total of 5969 pages!
The number of pages clearly keeps increasing. That includes more features to defend networks, but also more features to potentially abuse 👀
One of the most amazing things #demoscene has produced is creating art with insane platform / size limitations. Most of the time the constraints are coming from the platform or the rules, but sometimes they're self-imposed: Just because everyone else is doing bloaty stuff you don't have to.
Here are couple of my all time favourite intros/demos that totally blew my mind not only for their amazing presentation, design and technical execution but also for their insanely small size:
- RGBA & TBC: Elevated (intro, 4KB): https://www.youtube.com/watch?v=jB0vBmiTr6o
- Farbrausch: fr-041: debris (demo, 177KB): https://www.youtube.com/watch?v=jY5Vrc5G0lk
- Alcatraz: Remnants (intro, 256 bytes): https://www.youtube.com/watch?v=A9jn6ExjDw8
- Mercury - fermi paradox (intro, 64KB): https://www.youtube.com/watch?v=gX7ESVZ7T6Y
@jtk @jeroen @adulau @circl We were aware of your great work (cited in the paper!) and it's indeed surprising how long this has been an issue (I was not aware of the public feed though, thx!). With the new scanning methods we used, and the other tunneling protocols we also tested, this really uncovered a lot of vulnerable hosts... and many new DDoS attacks are possible. Hopefully the scans and notifications by Shadowserver will help at least bit, but realistically it seems like it will be a problem for a long time...
New @vanhoefm paper just dropped https://papers.mathyvanhoef.com/usenix2025-tunnels.pdf
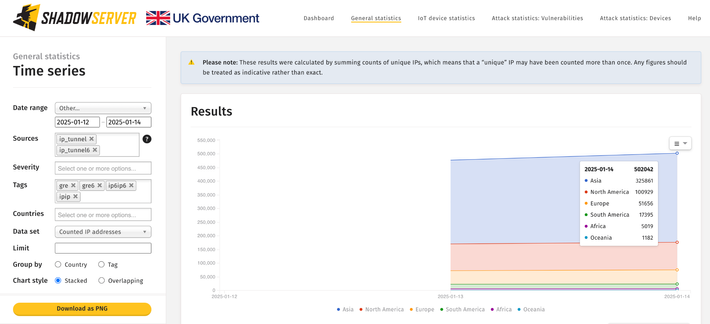
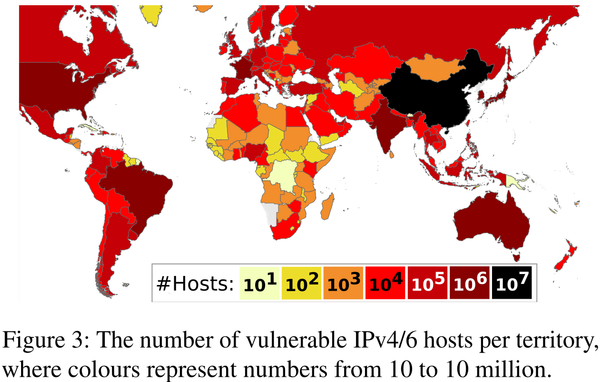
Around 4 million hosts seem to accept various tunneled packets arbitrarily.
Now sharing open IP tunnel hosts in a new daily Open IP-Tunnel report https://shadowserver.org/what-we-do/network-reporting/open-ip-tunnel-report/
These hosts accept tunnelling packets such as IPIP, GRE without authenticating the source IPv4 or IPv6 addr, which can be abused for DoS/other attacks
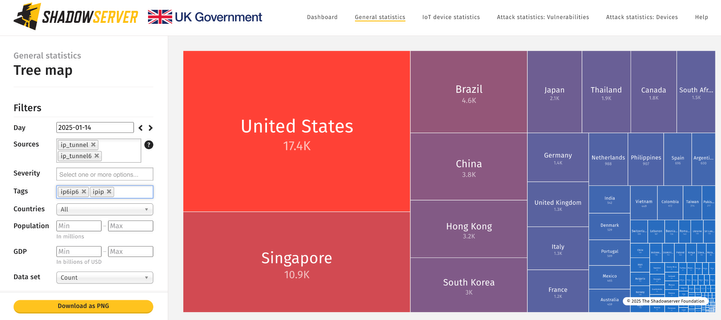
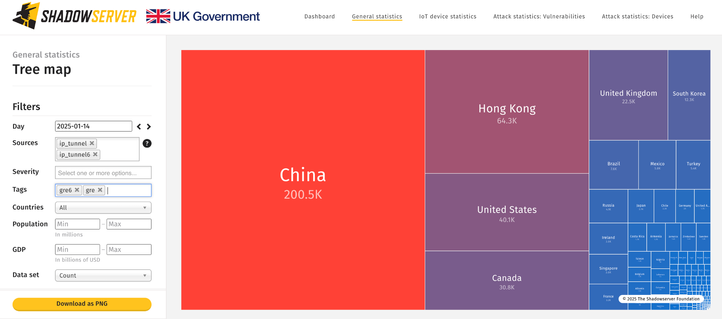
~436K GRE & ~66K IPIP vulnerable IPs found on 2025-01-14
Geo breakdown (GRE/GRE6):
Geo breakdown (IPIP/IP6IP6):
These vulnerabilities were discovered by Angelos Beitis and Mathy Vanhoef @vanhoefm at the DistriNet Reseach Unit at KU Leuven University in Belgium. Thank you for the collaboration!
You can find more details on the vulnerabilities at: https://github.com/vanhoefm/tunneltester
For more info and a demo video, see the article at https://www.top10vpn.com/research/tunneling-protocol-vulnerability/
IT admins can request access to our code to test servers (code is not yet public to prevent abuse): https://github.com/vanhoefm/tunneltester
Academic paper: https://papers.mathyvanhoef.com/usenix2025-tunnels.pdf
After an embargo of 8 months, we are glad to finally share our USENIX Security '25 paper! We found more than 4 MILLION vulnerable tunneling servers by scanning the Internet.
These vulnerable servers can be abused as proxies to launch DDoS attacks and possibly to access internal networks.
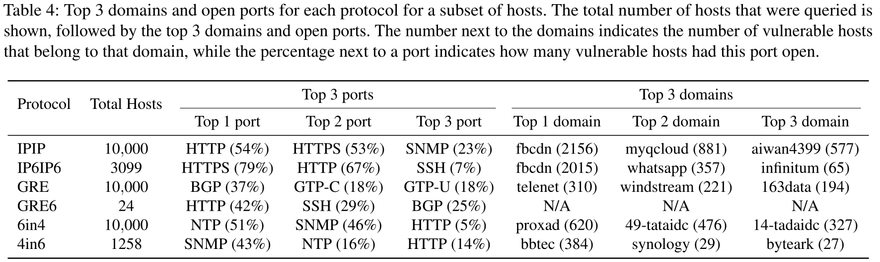
We investigated the owners of some of these vulnerable tunneling servers. This revealed that notable domains, such as Facebook’s content delivery network (CDN) and Tencent’s cloud services were affected. The home routers of some national ISPs were also affected.
@lasagne Yeah probably not the first time. Having concrete write-ups or proofs are useful to convince others this really happens, so those are always welcome :)
Wow, an adversary first compromised a neighbor of the target, and then attacked the target over Wi-Fi (with stolen password).
This is the first observed case of the #AntennaForHire attack that AirEye hypothesized.
Any Wi-Fi attack is now a remote attack!
The "lawful" intercept systems at AT&T and Verizon were targeted, and possibly breached, in a hack attributed to a Chinese state backed hacking group.
For me this incident just drives the point in that those systems should not exist in the first place. Security researchers have warned forever that backdoors eventually will be used by others.
https://www.wsj.com/tech/cybersecurity/u-s-wiretap-systems-targeted-in-china-linked-hack-327fc63b
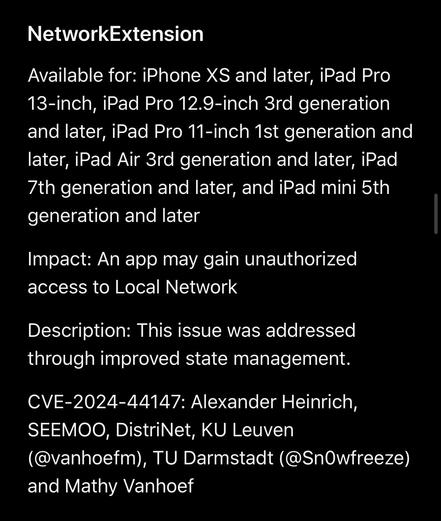
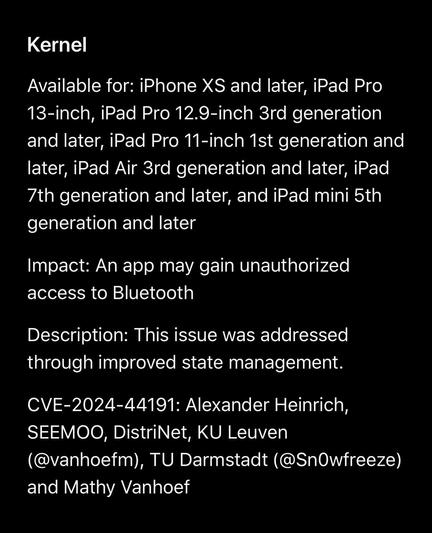
Two issues that we reported to Apple have been fixed in iOS 18 😊
It was a great collaboration with @vanhoefm and his team.
@ajabep I've not yet used 6GHz Wi-Fi. So I'd actually be curious to hear your experience :)