Are #cybersecurity incidents growing more costly?
Cyentia Institute's recent Information Risk Insights Study points to a 15-fold increase in the cost of #incidents and #databreaches over the last 15 years.
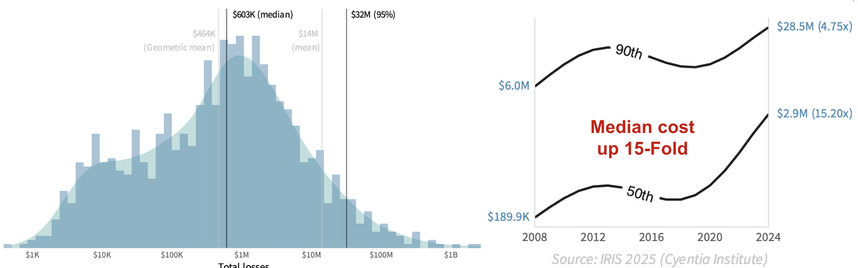
The chart on the left shows the distribution of known/reported financial losses from incidents across the time period of the study. The typical (median) incident costs about $600K, while more extreme (95th percentile) losses swell to $32M. Note that the chart uses a log scale, so the tail of large losses is a lot longer than it appears.
The chart on the right trends the escalating costs of cyber events over time. Median losses from a security incident have absolutely exploded over the last 15 years, rising 15-fold from $190K to almost $3 million! The cost of extreme events has also risen substantially (~5x). So, yeah—cyber events are definitely growing more costly.
That said, this picture looks a lot different among different types and sizes of organizations. How are financial losses and other #cyberrisk factors trending for orgs like yours?
Download the full IRIS 2025 to find out!
Free with no reg req'd - though you can join Cyentia's free membership forum for bonus analytical content related to the report.