📣Tomorrow (wed18) I will be presenting the last news in the #radare2 ecosystem and showcase some real world #reverseengineering usecases with #r2ai @NowSecure
#Connect25 — https://infosec.exchange/@NowSecure/114597238407822896
Vulnerability Researcher and amateur home chef. Also I once forged a knife.
I think you're getting old when the excitement of having a certain piece of tech (phone, tablet, laptop, etc.) working for as long as possible is 100x greater than thinking of getting something new. This did not used to be like this 15 years ago 😂.
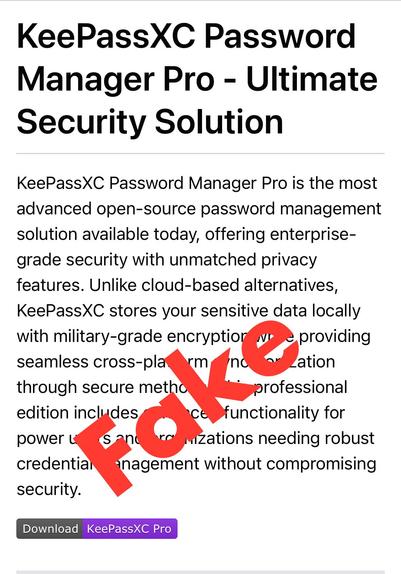
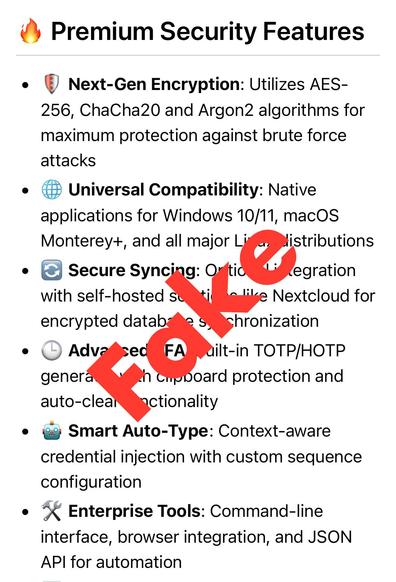
🚨 *Attention!* We were made aware of a fake “KeePassXC Password Manager Pro” repository on GitHub that links to unverified external binary downloads.
- There is NO Pro version of KeePassXC!
- You get all the “Pro” features with the regular version.
Please download KeePassXC only from trusted distribution channels linked on https://keepassxc.org/ !
Quick note: https://arm.jonpalmisc.com/ has been updated to the latest version of the Arm spec. Any changes should be strictly improvements, but let me know if something seems off.
Excited to be traveling again to meet old and new friends ✈️. Love the social side of this industry (despite sometimes being socially awkward 😑).
@osxreverser gl&hf!
Now everyone is coming up with their own theories of what happened. I'm pretty sure it was somebody with a Flipper Zero and a half cooked "disconnect Europe from power grid" payload.
After 10h without power, and almost no cell network nor Internet I can't decide if it was super enjoyable or a bit worrying 🧐🧐🧐. Maybe both?
@lanodan @andrewrk @cadey I know part of the story: at some point even longer ago, they ran out of space in the original `struct _IO_FILE` and had to come up with a horrible hack to enlarge it without breaking old binaries. (See libio/old*.c in the glibc source code.) So, in the new enlarged version, they put a bunch of padding at the end to make room for future enlargements. The weird size calculation is meant to cause a compile error if they ever run out of space again.
With bluesky (mostly) going down for a few hours today, I got to wondering about how decentralized the fediverse really is in terms of where its servers are hosted. I grabbed a server list from fedidb, with network information coming from ipinfo.io .
[EDIT: I did a better analysis on a dataset of 10x as many servers, see https://discuss.systems/@ricci/114400324446169152 ]
These stats are by the number of *servers* not the number of *users* (maybe I'll run those stats later).
fedidb currently tracks 2,650 servers of various types (Mastodon, pixelfed, lemmy, misskey, peertube, etc)
The fediverse is most vulnerable to disruptions at CloudFlare: 24% of Fediverse servers are behind it. Also note that this means that I don't have real data on where this 24% are located or hosted, since CloudFlare obscures this by design.
Beyond CloudFlare, the fediverse is not too concentrated on any one network. The most popular host, Hertzner, only hosts 14% of fediverse servers, and it falls off fast from there.
Here are the top networks where fediverse servers are hosted:
504 Cloudflare, Inc.
356 Hetzner Online GmbH
130 DigitalOcean, LLC
114 OVH SAS
56 netcup GmbH
55 Amazon.com, Inc.
55 Akamai Connected Cloud
36 Contabo GmbH
33 SAKURA Internet Inc.
32 The Constant Company, LLC
31 Xserver Inc.
28 SCALEWAY S.A.S.
24 Google LLC
23 Oracle Corporation
16 GMO Internet Group, Inc.
14 IONOS SE
14 FranTech Solutions
11 Hostinger International Limited
10 Nubes, LLC
Half of fediverse servers are on networks that host 50 or fewer servers - that's pretty good for resiliency.
There is even more diversity when it comes to BGP prefixes, which is good for resiliency: for example, the cloud providers that have multiple availability zones will generally have them on different prefixes, so this gets closer to giving us a picture of the specific bits of infrastructure the fediverse relies on.
The top BGP prefixes:
55 104.21.48.0/20
50 104.21.16.0/20
48 104.21.64.0/20
41 104.21.32.0/20
41 104.21.0.0/20
38 104.21.80.0/20
32 172.67.128.0/20
31 172.67.144.0/20
28 172.67.208.0/20
28 162.43.0.0/17
27 104.26.0.0/20
26 172.67.192.0/20
26 172.67.176.0/20
23 172.67.160.0/20
19 116.203.0.0/16
17 172.67.64.0/20
17 159.69.0.0/16
16 65.109.0.0/16
14 88.99.0.0/16
14 49.13.0.0/16
13 78.46.0.0/15
13 167.235.0.0/16
13 138.201.0.0/16
11 95.217.0.0/16
11 95.216.0.0/16
11 49.12.0.0/16
11 135.181.0.0/16
10 37.27.0.0/16
10 157.90.0.0/16
75% of fediverse servers are behind BGP prefixes that host 10 or fewer servers, meaning that the fediverse is *very* resilient to large network outages.
Top countries where fediverse servers are hosted:
871 United States
439 Germany
156 France
148 Japan
75 Finland
57 Canada
49 Netherlands
38 United Kingdom
26 Switzerland
26 South Korea
21 Spain
19 Sweden
18 Austria
17 Australia
15 Russia
12 Czech Republic
10 Singapore
10 Italy
And finally, a map of the locations of fediverse servers:
https://ipinfo.io/tools/map/91960023-e8c6-4bee-9b07-721f2c8febab
@pancake alias whothefuckwrotethisshit="git blame"
@codecolorist sorry to hear that, man. It sucks having to be vigilant all the time when you're out in the city to avoid shit like this happening.
Just packaged and tested @RevEngAI 's plugin for @radareorg the service is still under testing so you can join the waitlist to get some api keys, it looks promising, and i'm always happy to see more tools and services being integrated with R2! #reverseengineering #ai
@kenkeiras oh nice! good to hear!
After being away from here for quite a while I felt I wanted to be back and see if I can actually migrate here. Is this still as active as it was during the last wave from X?
NK targeting researchers was the reason I initially left Twitter. Seems like they're starting to have a mastodon presence as well (https://blog.google/threat-analysis-group/active-north-korean-campaign-targeting-security-researchers/, thanks @codecolorist for pointing out the mastodon IOC) :( there's no escape from these fucks
2022 was a good year for me (among other things, I became a dad) and I hope that 2023 brings good health, a lot of love and wonderful new opportunities for everyone! I wish you all a happy 2023! 🥂🎊🍾
Merry Xmas to all of you that celebrate them, and happy holidays to those that don't! Enjoy some time off if you can and spend time with your loved ones. 🎅🎄
@fidgetingbits Thank you! It was a fun bug to play with, nice discovery!
As promised, here's the blogpost about the exploitation of #CVE_2022_32250 on Linux kernel 5.18.1. Hope you like it! (any feedback is welcome): https://blog.exodusintel.com/2022/12/19/linux-kernel-exploiting-a-netfilter-use-after-free-in-kmalloc-cg/