To escape a locked-down Citrix environnement, team member SAERXCIT (https://twitter.com/SAERXCIT) wrote a basic shellcode loader in OpenEdge ABL, a 40 years old english-like programming language. We're sharing it in the off chance someone else might one day need it:
Offensive Security team at Almond
@sigabrt @yeswehack This issue was assigned CVE-2024-52531. While the CVE description states that the vulnerability cannot be reached from the network, it seems, in fact, possible (check the blogpost for details).
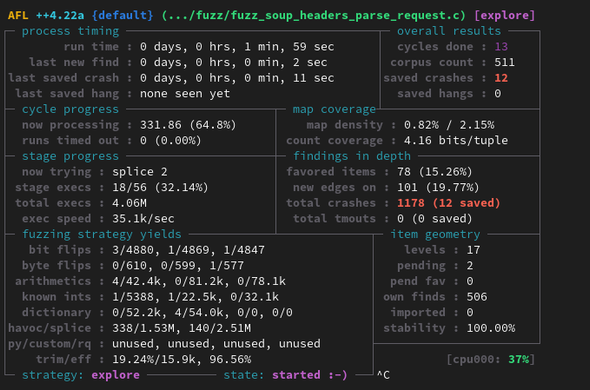
Team member @sigabrt describes a fuzzing methodology he used to find a heap overflow in a public @yeswehack bug bounty program for Gnome: https://offsec.almond.consulting/using-aflplusplus-on-bug-bounty-programs-an-example-with-gnome-libsoup.html
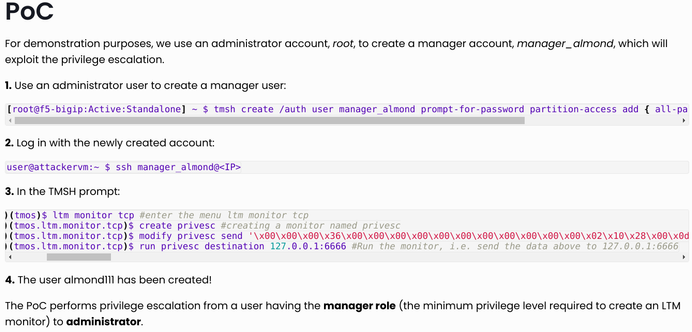
New article on F5! A write-up on CVE-2024-45844 a privilege escalation vulnerability in BIG-IP by team member @myst404
https://offsec.almond.consulting/privilege-escalation-f5-CVE-2024-45844.html
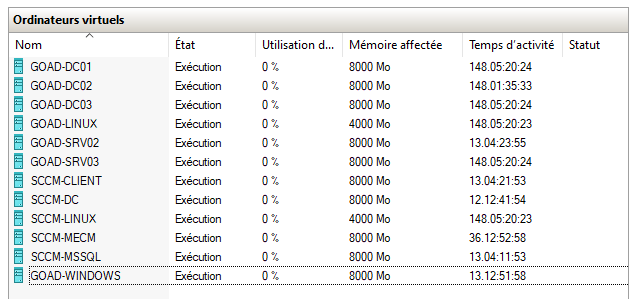
If you are lucky enough to have a Windows Server Datacenter with Hyper-V, you can automatically activate @M4yFly 's GOAD VMs, so rebuilding the lab every 180 days is no longer needed. We POCed a Vagrant-style script here:
How does F5's Secure Vault, its "super-secure SSL-encrypted storage system" work? Response in this article by team member @myst404
https://offsec.almond.consulting/deep-diving-f5-secure-vault.html
Got root, what now? Practical post-exploitation steps on an F5 Big-IP appliance, by team members @drm and @myst404
https://offsec.almond.consulting/post-exploiting-f5-BIG-IP.html
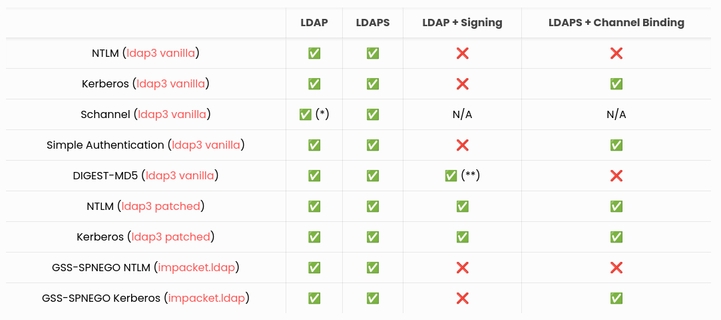
Good news dear LDAP hackers 🎉 #ldap3 is now compatible with Channel Binding and LDAP Signing. You can use the library against hardened domain controllers. Thanks cannatag and CravateRouge.
Get the last version: https://github.com/cannatag/ldap3
More info: https://offsec.almond.consulting/ldap-authentication-in-active-directory-environments.html
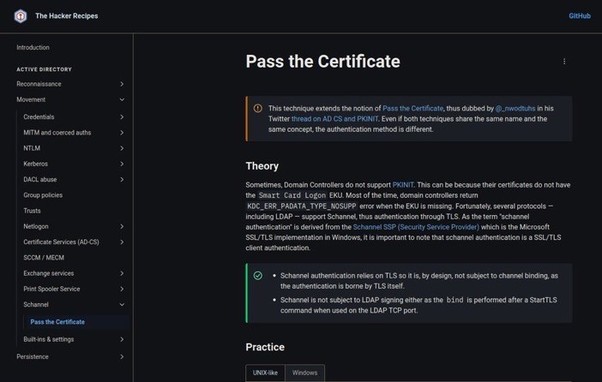
#PassTheCertificate (schannel edition) has now is own recipe! https://www.thehacker.recipes/ad/movement/schannel/passthecert
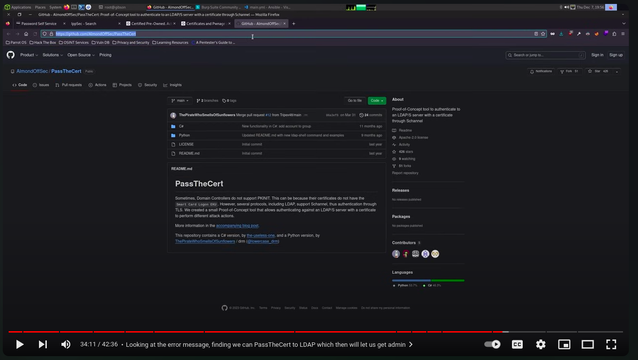
Stoked to see #PassTheCert featured in ippsec ‘s solution to HackTheBox Authority🧑⚖️!
Video: https://www.youtube.com/watch?v=7AF5riqLy-8
Find the tool here: https://github.com/AlmondOffSec/PassTheCert
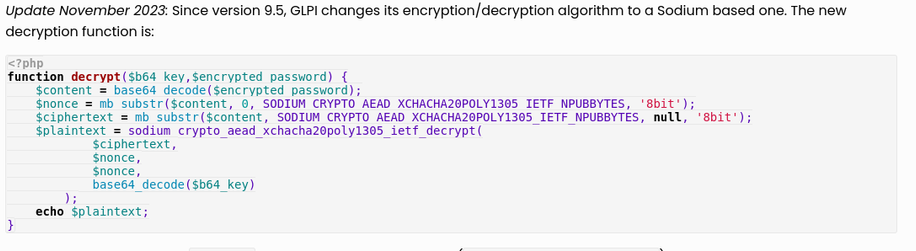
We updated this old gem by @myst404 to include the new #GLPI decryption algorithm.
https://offsec.almond.consulting/multiple-vulnerabilities-in-glpi.html
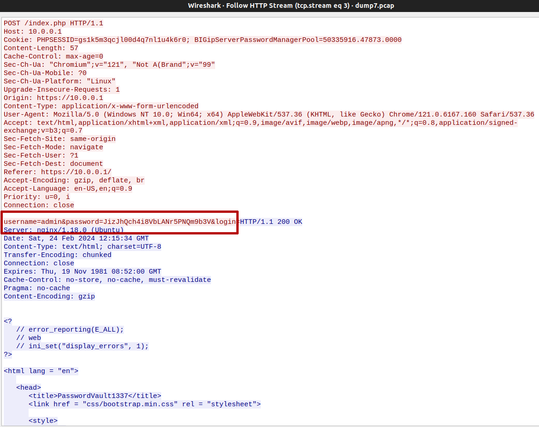
Understanding the different types of LDAP authentication methods is fundamental to apprehend subjects such as relay attacks or countermeasures. This post by @drm introduces them through the lens of Python libraries.
https://offsec.almond.consulting/ldap-authentication-in-active-directory-environments.html
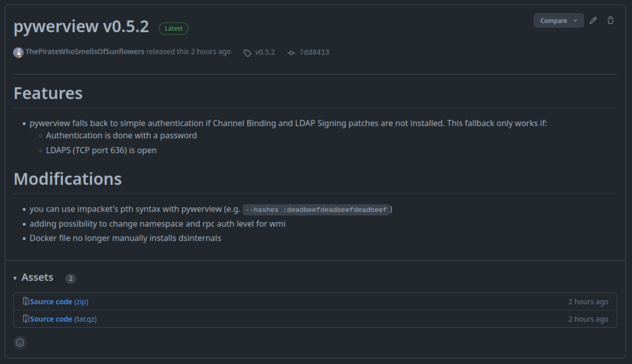
pywerview v0.5.2 is out! It implements, among other things, the "simple authentication trick" to use the tool against hardened DCs and without install custom ldap3 lib.
🌻
To fix the bypass, @matrix hardened the CSP by restricting allowed domains to reCAPTCHA related ones.
https://github.com/matrix-org/matrix-react-sdk/security/advisories/GHSA-xv83-x443-7rmw
PoC:
```
<iframe srcdoc="<body><script src="https://www.gstatic.com/fsn/angular_js-bundle1.js"></script><div ng-app> {{'a'.constructor.prototype.charAt=[].join;$eval('x=eval(atob(`YWxlcnQodG9wLmxvY2F0aW9uKSAK`))');}}</div></body>"></iframe>bbbb
```
The final payload that worked for the web app and the electron-based one used a base64 encoded string within the eval method. An iframe tag is used because the application is a SPA.
This version is vulnerable to sandbox escape with "{{'a'.constructor.prototype.charAt=[].join;$eval('x=alert(1)');}}" (originally found by Gareth Heyes). However, this payload is known to bug if the eval contains a "." (dot character).
Original CSP included a "script-src https://gstatic.com 'unsafe-eval'" directive. gstatic CDN still hosts out of date libraries such as AngularJS 1.3.20.
A few months ago, Cadence Ember found an HTML injection in the matrix-react-sdk, mostly used by the @element client. The CVE advisory stated that the implemented Content-Security-Policy mitigated the risk of XSS. So, team member S1m poc'ed a bypass. 🧵
A look back at CVE-2020-0911, a Windows Installer EoP found by jonasLyk with team member @clavoillotte:
https://offsec.almond.consulting/windows-msiexec-eop-cve-2020-0911.html