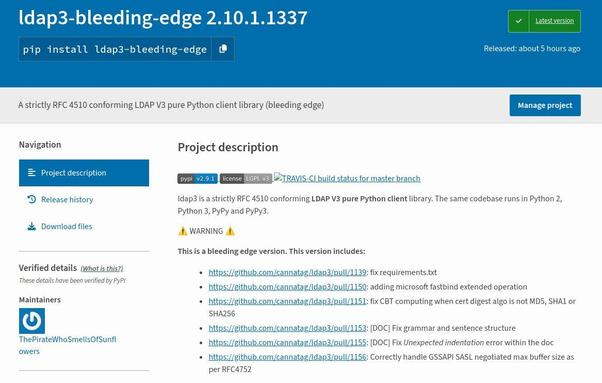
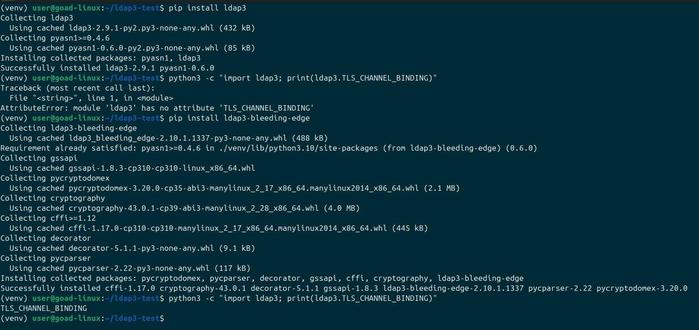
Yet another toot about #ldap3: I have created the pipy package ’ldap3-bleeding-edge’. This package is based on ldap3 2.10.1 (unreleased on pipy) + 6 pending PRs. It may be unstable but... "works on my machine" 🤷
sources: https://github.com/ThePirateWhoSmellsOfSunflowers/ldap3/tree/bleeding_edge
🌻