CMIYC (https://contest.korelogic.com/) will not make it to DEF CON this year. https://passwordvillage.org/ will be there! We intend to do a contest later this year.
KoreLogic's password cracking contest at DEFCON
Defcon contest @CrackMeIfYouCan might be a bit slower for me this year
:fire_angry:
My plan for eliminating 10-12 of my 12 year old servers seems to be coming together.
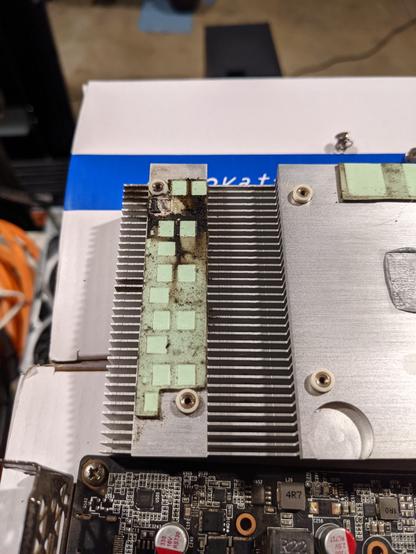
Currently for Defcon's @CrackMeIfYouCan contest (among other things) I have a modest gpu cluster on standby for running hashcat. That cluster is a collection of old desktops with supermicro x9 generation motherboards with xeon e5-v2 era cpus. Each server in my collection can fit 1-2 GPUs with the exception being a 1U box that I crammed 3x 2080ti in to.
I am spending just as much power on server side architecture as I am running a GPU in hashcat.
Solution? Less "server" for more GPU. Thankfully the bitcoin mining industry has made high gpu density a thing, and converged AI is making all the old mining rigs outmoded. I scored this 8 slot mining rig with PSU for ~$150 shipped on ebay.
The onboard celeron and 8g memory consume a few watts leaving the rest of the power draw purely on the GPUs.
Pictured below is the initial test setup with a few spare GPUs I had laying around before the hashcat season starts. Not running 12 extra E5-2650v2 CPUs is going to save a lot of power and heat this summer.
We just dropped a couple inter-related advisories for VICIdial, open-source software used by call centers: https://korelogic.com/Resources/Advisories/KL-001-2024-011.txt and https://korelogic.com/Resources/Advisories/KL-001-2024-012.txt
Add some broth, a potato; baby you've got a stew going.
@lakiw I think we win! =)
We've added a page w/info about the password sets, encrypted files, and hints: https://contest-2024.korelogic.com/password-info.html
Ok, official results are official:
Pro: HashMob super narrow victory over hashcat, Cynosure Prime taking third.
Street: ThatOnePasswordWas40Passwords dominated.
Thanks to both our returning contestants, and new! Hope you will be back next year.
We'll post more details about hash breakdowns, data sources used, and crack rates per data source, etc. in the coming weeks.
Scoreboard adjustments, maybe not finished.
We're (so far) not going to ban the rule violators but rather, void any successful cracks starting from the time they started heavily spamming us (thousands of invalid submissions, clearly just trying to bruteforce guess). Which means we can't know that they earned any of their cracks from that point forward.
When a hint file reveals the first few chars of a plaintext, that's not an invitation to stuff 40k iterations per submission...
You know who you are. Reaching for the ban hammer.
We're idling on https://discord.gg/dpKSjtTw and will kick off a post-contest talk at probably 11:30a DEF CON time; will post links in that discord.
Teams: 2h left!
And one final tidbit for you at https://contest-2024.korelogic.com/downloads.html
@tychotithonus I think I slept through the outage? We've got multiple people keeping an eye on the human contact email, though.
A note about the striphash type. Generally we try to be accommodating of reasonable variations on formatting of hashes submitted as long as the plain is correct and we can automate the normalization.
But for that hash type, the bad formatting is the _point_. IYKYK. So you must submit back the actual hash we provided, with your crack.
Teams: Another download is available.
These people really need to observe the Stringer Bell Rule.
Teams: Another leak at https://contest-2024.korelogic.com/downloads.html
Teams: please resubmit any cracks you think you are missing credit for.
This particular issue should be resolved; teams have gotten (or will get upon next submission that contains them) credit for valid radmin3/shiro2/saph512/other cracks that had been previously incorrectly reported as repeats.
issue was radmin3 user:plain that were also used for other hash types - something that years ago we'd decided would Never Happen, which the submission-handling code enforced. But the DB didn't enforce (no UNIQUE key for those for example) so when I forgot and loaded up radmin3 data that violated that late after full score-testing, it did not error.
Anyway, workaround deployed that I _think_ covers all such cases. Replayed some submissions that I knew were impacted, but could easily not have gotten them all. Plus, need fresh inputs in order to have any _remaining_ issues jump out.
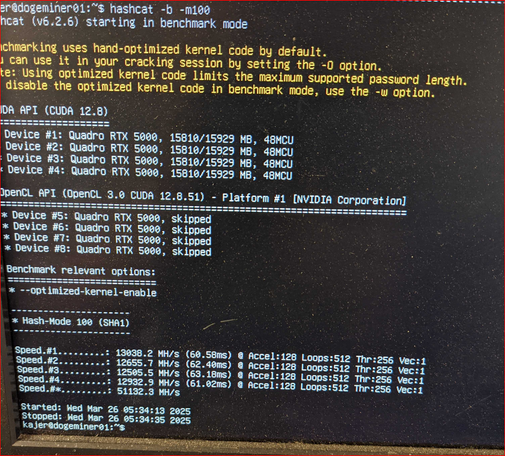
@kajer funny that's how running it looks too (obvs)
This is how you compete in @CrackMeIfYouCan
They are in fact the same problem. The fix is easy; potential unintended consequences are not. So small fix + big testing before we push to prod.
inb4 yololetsgooofuckitweball
Teams: Check the downloads page, new mix tape just dropped.