@ge0rg thanks!
software developer at Hex-Rays*, hobby reverse engineer. Advanced cleartext hacker. 日本語おk *For Hex-Rays support/inquiries: http://hex-rays.com/contact
A few more additions to that famous 'wat? javascript' talk:
>>> [] * 2
0
>>> [] + []
""
>>> {} + {}
NaN
>>> {} * 2
Unexpected token '*':1
WANTED: Intel Architecture Labs 1990’s CD-ROM’s. They appear to have maybe been monthly. They contained a mirror of Intel’s ‘download.intel.com’ ftp server, specifically the /ial/ subdirectory which is not in the 2014 backup of the site on archive.org.
Lots and lots of white papers and design guideline documents in there. Especially looking for ones from the late 1990’s (1998-ish onward) if they exist. I’ve seen references in mailing lists to them that lead me to believe they do.
Example gem: intel trying to cover its ass after the FDIV bug, and have some more FDIV
P.S. it seems the compression algorithm is called "RELC": https://www.fujitsu.com/downloads/JP/archive/imgjp/group/fei/services/fei/compress/relcfmc16.pdf
TIL that most people cannot in fact bend their thumb in both directions, it's just the most useless genetic superpower ever. Never even realized it's not normal.
https://en.wikipedia.org/wiki/Hitchhiker%27s_thumb
Add that to the list of weird genetic traits like sneezing because of the sun or thinking that cilantro tastes like soap.
Dear lazywebs:
I wish I could find this old story from Internet Lore, but there was a compression challenge posted on...I think usenet? or something, for coming up with an algorithm to compress a file of the author's choosing. Basically, someone posted that 'anything can be compressed', this actual computer scientist chimed in that that's not true. The 'anything can be compressed' person offered to prove their claim.
So the gauntlet was thrown, the CS person created a good random data file and said lots of luck. The noob 'compressed' the data by simply splitting it up across multiple files. They found some coincidental sequence in the random data that occurred more often than others (like, a sequence of 3 bytes in a row, happening a few times in the data), and split the data into a new file each time the pattern occured.
They didn't win of course, since by splitting the data into files requires filesystem overhead (inodes, filenames, all of which take up more space than was gained back through ommiting the N-byte sequence).
It was a great writeup for me as a young computer science person though, got me to think about a lot of stuff all at one time.
I'm betting someone on here has a link to the story...
@ge0rg Thanks! Judging by the readable text fragments, it's most likely some variation of LZSS or LZ77 but I didn't manage to figure out the exact parameters so far.
@ge0rg got firmware images?
Paged Out! #6 has arrived! And it's jam-packed with content!
You can download it here:
https://pagedout.institute/?page=issues.php
@joxean gnutella maybe?
✅ Fixed a bug today by squinting really hard at 6 kernel addresses and spotting a pattern
Wait, what? 😯
#curl can send email? Damn... @bagder I'm impressed (not that I didn't expected that), curl just keeps on giving. 😁
curl --url "smtp://$SMTP_SERVER:$SMTP_PORT" \
--ssl-reqd \
--mail-from "$SMTP_USER" \
--mail-rcpt "$EMAIL" \
--upload-file "$LOG_FILE" \
--user "$SMTP_USER:$SMTP_PASSWORD" \
--insecure
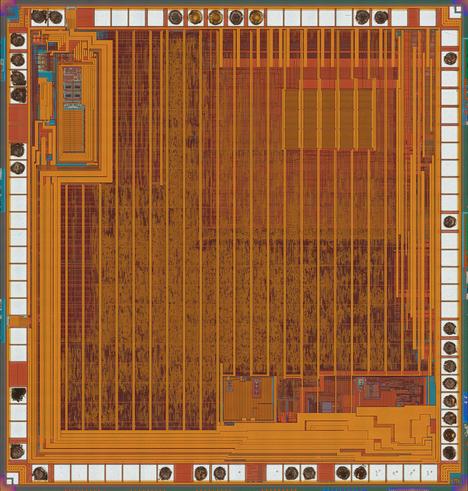
I guess we'll do a #namethatchip here at Mastodon. Looking to ID the whole package.
This came out of a two-die package with custom marking; both dies were made by Renesas. Die markings in top left read: 24, (c) Renesas electronic corp., 2012. Markings in bottom right read: PMF.
Please boost for reach!
@lucabtz I made a Lua decompiler ~25y ago after getting stuck in Escape from Monkey Island (the GrimE engine used Lua for scripting the game). It was pretty straightforward because there was no optimization and byte code patterns could be easily lifted back to the source code. I imagine nowadays it might be a little more difficult.
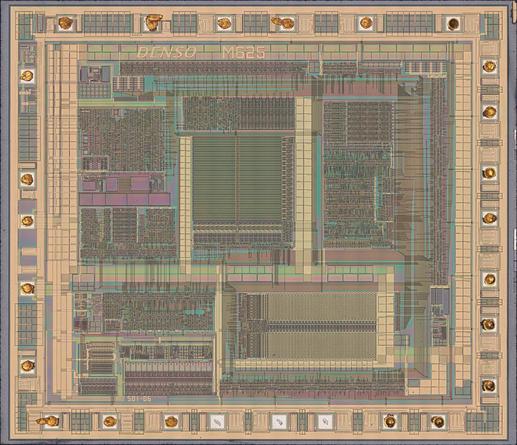
I pretty much missed the #nakeddiefriday but here is something to compensate for that.
This is one of Denso-branded MCUs, for which no documentation is publicly available. If anyone can recognize the CPU core used here, or can provide any other info, that'd be much appreciated. The chip was marked as MT0990, though that might not help in any way. Another chip marked MT6750 had the same die, probably only differing in the mask ROM set.
Hi-res: https://siliconpr0n.org/map/denso/mt0990/infosecdj_mz_nikpa20x/
Remember: IDN is crazy. And just not just a little.
@bluedevil Sorry I don’t do tech support on my personal account. Please use the official channels.
Hey,
#curl -v https://google.com as a metal song is a must see and hear experience. A masterpiece. I just love it.
"A DSL for Peephole Transformation Rules of Integer Operations in the PyPy JIT", new blog post on the PyPy blog: https://pypy.org/posts/2024/10/jit-peephole-dsl.html