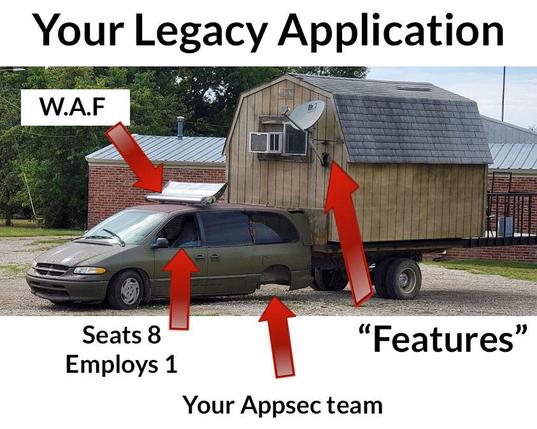
Legacy apps....
Author of Alice and Bob Learn Secure Coding AND Alice and Bob Learn Application Security!
She/her/lady/woman. shehackspurple.ca
Secure Coding Training and Public Speaking Inquiries & other:
Tanya (at) shehackspurple (dot) ca
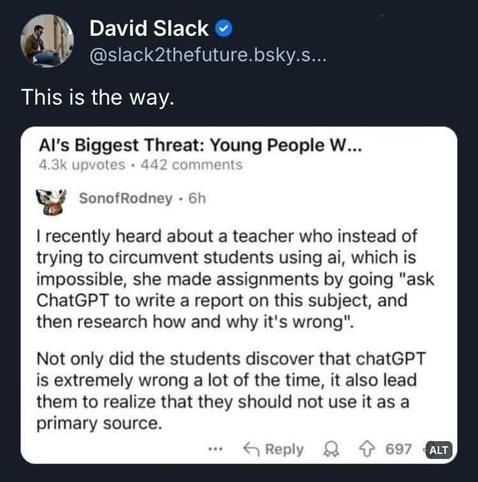
Teacher asks students to get AI to write a report for them, then research all the ways it's wrong. Thoughts?
@sternecker 💔 I wish you weren't right
Do you think the industry is better or worse at secure development now than it was 5 years ago? Why? Why not? #talkappsectome
@rjohnston Fixed! Phew
The Psychology of Bad Code
In this blog series I will explore several known bad developer behaviors that lead to insecure software, as well as how we can combat them by applying behavioral economic interventions. This series is an expansion upon my thoughts from my conference talk ‘Threat Modeling Developer Behavior: The Psychology of Bad Code’.
https://shehackspurple.ca/2025/11/27/the-psychology-of-bad-code/
@rjohnston thank you for telling me. How's strange. One sec
@sephster 💜💜💜
The Psychology of Bad Code, part one of a very long blog series on why we write insecure code, and how I hope we can do better. Includes slides from my new talk: Threat Modeling Developer Behaviour: The Psychology of Bad Code!
@0x58 I think once we've finalized it. It's still open for comment.
My ask:
✅ Download the doc
✅ Start conversations with your dev & security teams about what to do, not just what to avoid. 🙏
https://twp.ai/9PYCKl
5/5
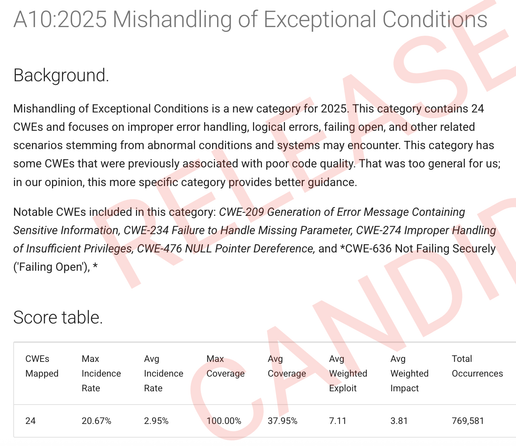
BRAND NEW:
A10 Mishandling of Exceptional Conditions. Error handling MATTERS, and it’s time we talk about it, and how to do it correctly and safely.
4/5
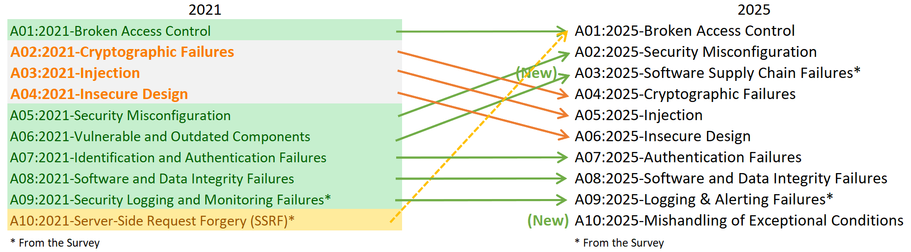
In this edition:
• A01 Broken Access Control remains #1: the most serious risk we’re facing.
• A02 Security Misconfiguration moves up to #: configuration mistakes keep happening.
• A03 Software Supply Chain Failures is significantly expanded. It's more than dependencies!
3/5
Why does it matter? Because we've updated the items to match wasn't happening RIGHT NOW in industry. Breaches keep happening, and we need updated advice.
2/5
Me: puts on music while making content
Also me: gets distracted, music is too good! Turns it off.
5 minutes goes by...
Me: I should put on music....
@rjohnston I think you're saying that you wish you knew how to threat model. I should create content on this!!
@trevdev you can do it!!!! 💪💪💪💪