How it started, how it's going
#RightToRepair
Simple, automated security tools and guidance for individuals and companies of all sizes.
Good cybersecurity shouldn't be an enterprise feature.
Sometimes a bot, sometimes not.
Security flaw reported in Cl0p ransomware gang data theft tool
It's a weird day when security researchers report a flaw in software used in criminal operations. Security researchers are reporting a vulnerability in the Cl0p ransomware gang's Python-based data exfiltration utility that could potentially allow command injection attacks against the cybercriminals' own infrastructure.
**Obviously, we don't really care if the criminals patch their software. But this is a prime example that all software can be flawed, and that input validation IS ALWAYS A GREAT IDEA.**
#cybersecurity #infosec #advisory #ransomware
https://beyondmachines.net/event_details/security-flaw-reported-in-cl0p-ransomware-gang-data-theft-tool-p-i-l-6-r/gD2P6Ple2L
Not sure that I would call #sohamgate a scandal.
But the memes are making themselves
Catwatchful stalkerware platform vulnerable to SQL Injection exposes 62,000 customers
An SQL injection vulnerability in the Catwatchful stalkerware operation exposed the entire customer database containing personal information of over 62,000 customers who used the service to secretly surveil approximately 26,000 victim devices, revealing plaintext passwords, device identifiers, and the identity of the operation's administrator Omar Soca Charcov in Uruguay.
**People managing spyware platforms are not great at security. Check your phone from time to time for any weird applications.**
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/catwatchful-stalkerware-platform-vulnerable-to-sql-injection-exposes-62000-customers-k-u-0-1-b/gD2P6Ple2L
Cisco patches critical hardcoded credentials vulnerability in Unified Communications Manager
Cisco reports a maximum-severity vulnerability (CVE-2025-20309) in its Unified Communications Manager platforms caused by hardcoded static SSH credentials for the root account. The flaw allows unauthenticated remote attackers to gain complete administrative control over enterprise IP telephony networks.
**Obvious first step - isolate the SSH port of your CUCM and make it accessible from trusted networks only. Then VERY QUICLY update to versions 15.0.1.13010-1 through 15.0.1.13017-1, or apply the patches. Just isolating the CUCM isn't enough - the hardcoded password can be abused by malicious insiders, or other devices with access to trusted networks can be breached and the attackers can then breach CUCM.**
#cybersecurity #infosec #advisory #vulnerability
https://beyondmachines.net/event_details/cisco-patches-critical-hardcoded-credentials-vulnerability-in-unified-communications-manager-i-k-5-m-e/gD2P6Ple2L
@GrahamDowns intentional. There's a method to the madness
WordPress Plugin flaw exposes over 600,000 websites to potential remote takeover
A critical vulnerability (CVE-2025-6463) in the Forminator WordPress plugin affecting over 600,000 installations allows unauthenticated attackers to delete arbitrary files, including critical WordPress files like wp-config.php. The flaw enable site takeover by forcing installations into setup mode after deleting wp-config.php and then connecting to a database they control.
**If you're using the Forminator WordPress plugin, immediately update to version 1.44.3 or later. Your WordPress site is exposed to the internet by design, so attackers will find it very quickly. Don't delay, updating a plugin in WordPress is quite easy. Then check your form submission logs for any suspicious entries that might indicate your site was already targeted.**
#cybersecurity #infosec #advisory #vulnerability
https://beyondmachines.net/event_details/wordpress-plugin-flaw-exposes-over-600000-websites-to-potential-remote-takeover-l-f-1-0-v/gD2P6Ple2L
@cjust i'm sure pun not intended
@lp0_on_fire @rysiek start worrying if you find a void bullet
Centers for Medicare & Medicaid warn 103,000 beneficiaries of unauthorized Medicare.gov account creation
The Centers for Medicare & Medicaid Services (CMS) disclosed a security incident involving unauthorized creation of Medicare.gov accounts affecting approximately 103,000 beneficiaries, discovered on May 2, 2025, when confused beneficiaries began calling about account creation letters they never requested. Malicious actors systematically created fraudulent accounts between 2023-2025 using legitimate beneficiary information obtained from unknown sources, exposing sensitive healthcare data which can be abused for scams and identity theft.
**As an individual, be very careful what data is available online about you. Be very selfish with your data, because it can be abused to impersonate you. As a developer, consider that an attacker can scrape data for someone else, and implement controls that can stop such impersonation by mechanisms for extra verification.**
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/centers-for-medicare-medicaid-warn-103000-beneficiaries-of-unauthorized-medicare-gov-account-creation-u-0-w-v-r/gD2P6Ple2L
@realn2s When you have three locks on your door and leave one unlocked.
When burglars tamper with the locks they unlock two and lock one.
Australia's Qantas Airways suffers cyberattack affecting up to 6 million customers
Australia's Qantas Airways suffered a cyberattack discovered on June 30, 2025, that potentially compromised personal information of up to 6 million customers through a third-party customer service platform breach. Cybersecurity experts are noting similarities to Scattered Spider ransomware tactics. The airline's CEO issued a public apology while the company works with Australian authorities to investigate the "significant" amount of stolen data.
****
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/australia-s-qantas-airways-suffers-cyberattack-affecting-up-to-6-million-customers-z-e-b-b-7/gD2P6Ple2L
@realn2s that's intentional 🤡
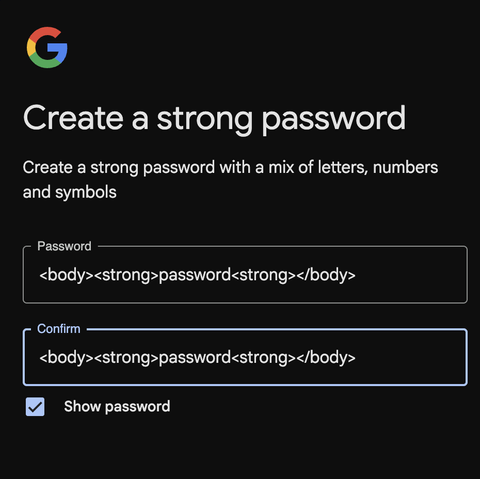
so hackers will try to close the strong and fail login!
@rysiek If you are willing to unpack a lot, i have a file 42.zip for you 😈
Strong Password Policy 101
Edit: for bonus points it messes with your OCD. There's a method to the madness
Virginia student loan administrator Southwood Financial hit by ransomware attack
Southwood Financial, a student loan administrator in Virginia, was hit by an Akira ransomware attack, that compromised sensitive borrower information. The company is providing credit monitoring services to affected individuals and has established a dedicated helpline.
****
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/virginia-student-loan-administrator-southwood-financial-hit-by-ransomware-attack-d-7-i-8-f/gD2P6Ple2L
Critical remote code execution flaw reported in Anthropic's MCP Inspector tool
Cybersecurity researchers disclosed a critical vulnerability (CVE-2025-49596, CVSS 9.4) in Anthropic's Model Context Protocol (MCP) Inspector debugging tool that allows remote code execution on developer machines through browser-based attacks exploiting the "0.0.0.0 Day" vulnerability and lack of authentication in default configurations. Attackers can compromise developer systems by tricking them into visiting malicious websites that send unauthorized commands to locally running MCP Inspector instances.
**If you're using Anthropic's MCP Inspector for AI development upgrade to version 0.14.1 or later. There is a fairly trivial exploit of your MCP Inspector tool that only requires you to visit a malicious site for your laptop to be fully compromised. So don't ignore this, update your MCP Inspector.**
#cybersecurity #infosec #advisory #vulnerability
https://beyondmachines.net/event_details/critical-remote-code-execution-flaw-reported-in-anthropic-s-mcp-inspector-tool-j-z-u-3-t/gD2P6Ple2L
Cyberattack in Missouri healthcare provider Esse Health exposes data of over 263,000 patients
Esse Health, a physician group serving the Greater St. Louis area, suffered a cyberattack discovered on April 21, 2025, that compromised personal and medical information of 263,601 individuals. The attack disrupted the organization's electronic medical record system and phone communications, forcing them to use manual processes and alternative communication channels.
****
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/cyberattack-in-missouri-healthcare-provider-esse-health-exposes-data-of-over-263000-patients-f-8-g-0-x/gD2P6Ple2L
@cR0w agreed. Yet since our objective is to get more people to click update we accept being less accurate.