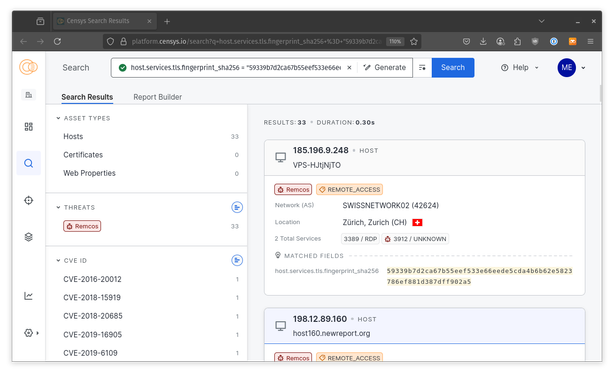
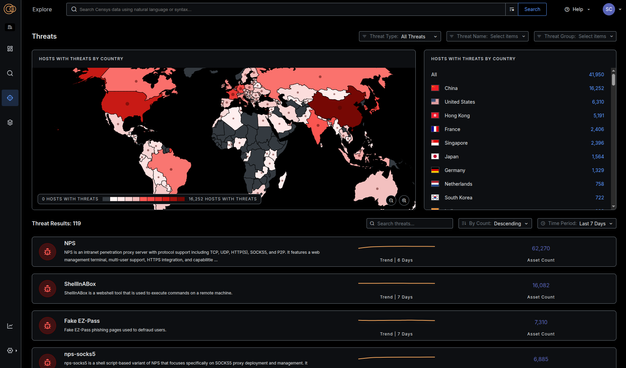
We used the new Censys Threat Hunting Module to investigate a Colombian threat actor, uncovering a series of remote access trojan (RAT) C2 servers.
We also show how to use this information to create a set of IOCs for defensive measures:
https://censys.com/blog/unmasking-the-infrastructure-of-a-spearphishing-campaign