🚨 RIFT Update:
We’ve boosted our compiler detection! 🛠️
Now with sharper insights into binaries built using GNU, MinGW, and MSVC toolchains.
More enhancements are on the way—stay tuned! 🔍✨
#ReverseEngineering #MalwareAnalysis #RIFT #malware #msft
Malware Analyst, Reverse Engineer, Software Developer, Mathematician, Teacher, Podcaster, send cat pics
@thomrstrom not sure what books you are looking for exactly, but I recently enjoyed Essentialsm by Greg McKeown
Did you know that new #Emoji can be proposed by anyone, simply by following some guidelines laid out by the #Unicode consortium? There's a time window each year where they accept proposals, and a select few might make it into future sets.
This year I turned one in: "Circuit Board", which I was surprised to find 1. didn't exist and 2. had not been proposed before (though CPU and Microchip have both been submitted and declined in the last 5 years)
You can read my proposal here:
https://storage.googleapis.com/greg-kennedy.com/Proposal%20for%20Emoji%20%E2%80%9CCircuit%20Board%E2%80%9D.pdf
and you can see the Unicode emoji proposal guidelines here:
https://www.unicode.org/emoji/proposals.html
Anyway, the odds aren't great of getting accepted, but if it IS then you can say "hey! I know the guy who submitted that one!"
Attached are the sample images I drew up for the proposal - which, incidentally, are now Public Domain as well. Enjoy!
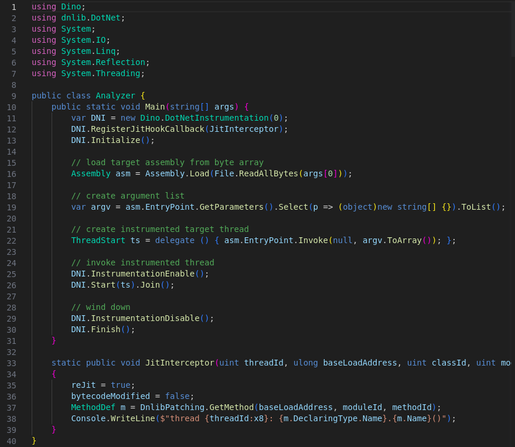
@SebastianWalla, Steffen Haas, @tillmannwerner, and myself will present a .NET instrumentation framework tomorrow at @recon 2025 in Montreal. Here's a humble brag sneak peek demo-ing how easy it is to write a function tracer!
For "all my new followers" here: if you are able to understand German, I'm podcasting since a couple of years now. Throughput is limited but we are at 10 episodes now (and counting). Chris' and my format is somewhere in between "two guys just talking" and "reading a lecture script". Hence the limited throughput: we just need a bit of time to prepare each episode.
Anyway, here's the URL: https://armchairinvestigators.de/ you can listen to it directly on the site or just search for "Armchair Investigators" on your favorite Podcast platform (how to actually get your self-hosted Podcast distributed is also a funny story, but more for a blag post, I think).
Oh yeah: our goal is to make cyber accessible to everyone (even your parents) while still being interesting for the average nerd. Topics for example are the Triton/Trisis case, cyber operations by the GRU, Olympic Destroyer, etc.
If you can't understand German but might have people who do, I'd very much appreciate a forward or mention 🙇
RULECOMPILE - Undocumented Ghidra decompiler rule language
New preprint (joint work with Albin Ahlbäck): "Fast basecases for arbitrary-size multiplication"
Abstract: Multiple precision libraries typically use assembly-optimized loops for basecase operations on variable-length operands. We consider the alternative of generating lookup tables with hardcoded routines for many fixed sizes, e.g. for all multiplications up to 16 by 8 words. On recent ARM64 and x86-64 CPUs, we demonstrate up to a 2x speedup over GMP for basecase-sized multiplication and a 20% speedup for Karatsuba-sized operands. We pay special attention to the computation of approximate products and demonstrate up to a 3x speedup over GMP/MPFR for floating-point multiplication.
@G33KatWork we have machine readable markup for metadata at home...
Check out the Red Team Tool Analysis Stream from this past Saturday https://www.youtube.com/watch?v=-zvTLBtMd1Q where we setup our analysis environment and began to take a look at the Sliver and Havoc C2 frameworks. Enjoy!
@mr_daemon did I already recommend DeArrow? Really changed my YouTube experience entirely.
postmerkOS for Meraki switches (MS220, MS225) is not affected by the recent xz compromise. I'm sure that comes as a relief to all 3 users of the custom firmware.
Concerning the xz affair, I am struggling on how to explain this to a normal person. The best approach so far:
This is as if an attacker succeeded in manipulating the manufacturer of a small part that is built into every car worldwide. Every car that would have been built in the future, the attacker could crash upon pressing a button.
And we noticed only because a car fanatic took a prototype to the racetrack and noticed that when he drives it backward through with hand brakes applied, the lap time would be half a second off.
@Ange @tychotithonus That difference took longer to spot than I'd like to admit. (hAcKS != hEcKS)
In search for some inspiration, I scrolled through https://www.garykessler.net/library/file_sigs.html and font files piqued my interest. I'll start with a generic rule for the OpenType font format. It is, as one might expect starting with "Open" and all, a registered trademark of Microsoft. This signature matches on the file magic and then puts some sensible boundaries in place that I've observed in font files on my local installation.
```
rule OpenTypeFontFile {
meta:
description = "Generic signature for the OpenType font format, excludes some unexpected but valid files to reduce false-positive rate"
author = "@larsborn"
date = "2024-03-10"
reference = "https://en.wikipedia.org/wiki/OpenType"
example_hash = "09bcc57b0f2b1518758831018922eadb2b3f279b56d13e1ba9aae04c1927a763"
DaysofYARA = "26/100"
condition:
uint32be(0) == 0x4f54544f // OTTO
and 4 < uint16be(4) and uint16be(4) < 100 // sensible range for table count
and uint16be(6) & 0xf == 0 // search range is often divisible by 16
}
```
async - await - async - await
IN THE JUNGLE, THE MIGHTY JUNGLE
THE CLIENT AWAITS THE CALL
🎶