Let's try Ghidra development with the new Claude Code Web!
#Ghidra
I had this script where I thought I fixed a bug by referencing X.y.z instead of X.z. Except nothing changed, the buggy behavior is still there (the file output contains garbage).
I add logging, the logs appear and show everything is fine.
Add more logs, exceptions even (to stop at a specific state). They run and show all is fine.
After I restart Ghidra the bug is gone.
To be clear: there must be some kind of bytecode caching that affects my object reference but does not affect additional logging/exception throwing??
Any ideas?
🎹🔧 Ah yes, a "gentle introduction" to the thrilling world of #hacking 40-year-old synth #firmware with Ghidra—because who doesn't want to spend their weekend squinting at ancient hex code? 😴 Just remember, you don't need the actual DX7 to follow along, because nothing says "fun" like emulating obscure 80s #tech. 🙃
https://ajxs.me/blog/Introduction_to_Reverse-Engineering_Vintage_Synth_Firmware.html #synths #Ghidra #retro #emulation #HackerNews #ngated
Bonus: There is a predefined `writer` stream object that you can use to log to the GUI console.
The recording of our @Defcon talk is now available. We shared our approach to reversing IoT and OT malware written in Go using a hybrid toolkit that blends AI with traditional analysis methods using #Radare2 , #Ghidra, and #BinaryNinja. Thanks to everyone who came out and stayed engaged through the technical hiccups that the venue had. We had to improvise and share a link for the slides on the spot.
New post: Advantech printer driver heap bug, likely LPE. Details + repro: https://neurowinter.com/security/2025/10/09/Multiple-Expliots-in-Advantech-Printer-Driver/ #infosec #Windows #LPE #PrinterDriver #Advantech #ReverseEngineering #WinDbg #Ghidra #CWE190 #VulnerabilityResearch #Security
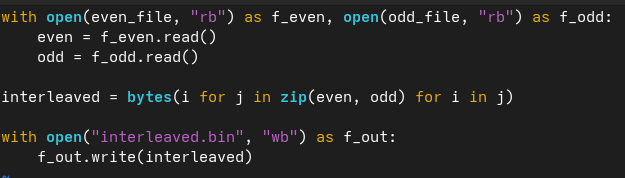
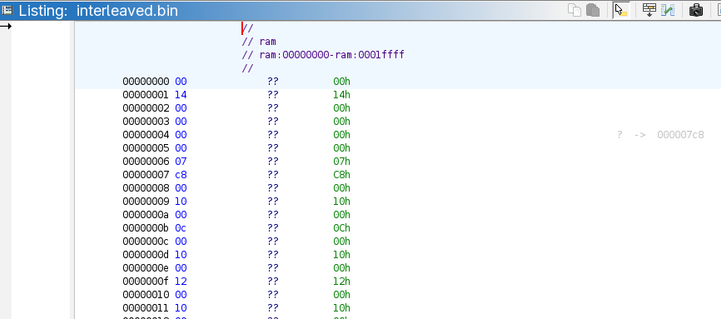
Time to analyze these even/odd roms. After some bit fiddling with Python, I have a single "interleaved.bin" that can be loaded into Ghidra.
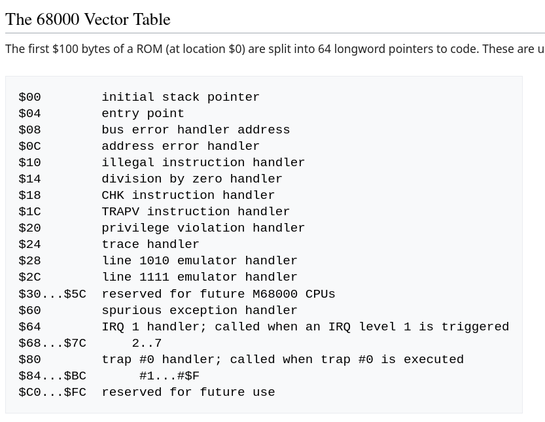
After loading it into Ghidra we can immediately see a first hint - address $0x04 contains a number: 0x7c8.
Beginning of the MC68k memory (first 0x100 bytes) contain a vector table and address 0x04 points to the "entry point".
And if we scroll to the address 0x7c8, we can see valid MC86k code.
As is becoming usual, when I don't understand what a new platform is doing, I reach for #ghidra first and ask questions later.
It has revealed the "save/restore screen" code emitted by TIGCC, as well as some hardware/OS version checks that I didn't know were there. That explains why my Hello World binary was larger than expected.
Further, it confirms that absolute addresses are stored as all-zeros, to be fixed up later (at program launch?) by the calculator OS's internal relocating-loader. (There is some mysterious binary junk at the end of the executable that looks like it might be a table involves somehow in these fixup's.)
Malware analysis and threat hunting live!
Let's do some reverse engineering and threat hunting!
Outstanding update on Iaito, due to some missers from my side this went wrong on previous version, once the issue was sorted out things got back on par.
radare2/r2dec_js/r2ghidra and Iaito all updated for 32bit and 64bit, on riscv64 Iaito fails to build due to an issue with llvm12. Enjoy :)
radare2-6.0.4
r2dec_js-6.0.0
r2ghidra-6.0.2
iaito-6.0.4
#HaikuOS #haikuports #radare2 #Iaito #ghidra #reverseengineering #decompiler #opensource #software
#ghidra JS scripting API when
We are finally able to publicly release our emulator!
https://stumbl.ing/posts/styx-emulator-release/
https://infosec.exchange/@styx_emulator/115255413979870869
#emulation #rust #embeddedsystems #linux #reverseengineering #embeddeddevices #ghidra
On Thursday, attend my workshop at BruCON on r2ai and ghidraMCP over various #CTF challenges.
Human requirements:
- You have already reversed a few #binaries before, OR you have basic to good understanding of one #assembly.
- Brains, because #AI won't do it all for you :P
Laptop Requirements:
- a laptop ;P
- latest version of #Radare2
- latest version of #Ghidra
- #exegol or #docker installed
- some extra free space for some installs
cc: @radareorg
(if time, there's radare-mcp in bonus :)
Live now reverse engineering and threat hunting with ReVa!
AirStrike 3D, retro Windows game analysis / #reverseengineering toolkit github.com/e-gleba/airs... #retrodev #ghidra #retrogaming #retrocomputing
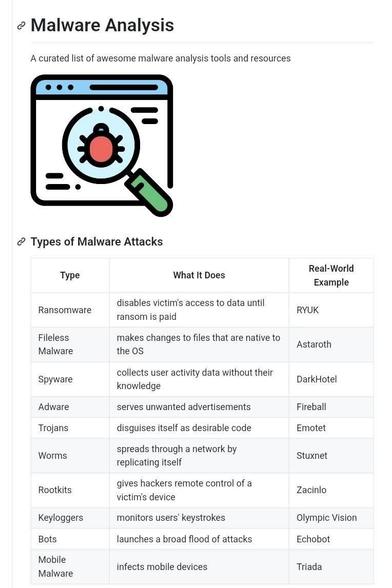
🔎 Malware Analysis Tools & Resources — Lab-Only Guide (Defensive) ☣️🛡️
Malware analysis is the practice of studying suspicious files and binaries to understand capabilities, indicators, and containment actions — always inside isolated, offline labs. 🧪💻 Below are trusted tools and resources analysts use to triage, unpack, and investigate malicious samples, plus learning hubs to level up your skills.
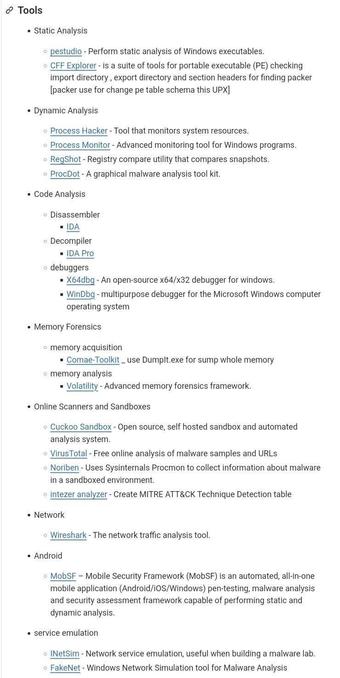
For static analysis (examining files without running them) analysts rely on tools like strings, file, ssdeep, PEStudio, Detect It Easy (DIE), Ghidra, and r2 / radare2 to inspect headers, imports, embedded strings, and binary structure. 🧩 For dynamic analysis (safe execution), sandboxes such as Cuckoo Sandbox, Any.Run, and instrumented VMs with Process Monitor, Process Explorer, Procmon, Sysmon, API monitor, plus network capture (Wireshark/tshark, tcpdump) reveal runtime behavior and network indicators. 🔬📡
Memory & forensic analysis uses Volatility / Volatility3, Rekall, and tools to capture RAM and extract artifacts. For unpacking and debugging native code, analysts use x64dbg, WinDbg, GDB, and deobfuscation helpers; for Java/.NET, tools like jadx and dnSpy help reverse engineered bytecode. 🧠⚙️
Threat intel & enrichment resources accelerate investigation: VirusTotal, Hybrid Analysis, MalwareBazaar, Malpedia, AbuseIPDB, OTX (AlienVault), and MISP provide samples, IOCs, yara rules, and community knowledge. 🗂️📊 Combine these with YARA for signature matching and Sigma for log detections. 🔎🧰
Learning resources & safety: follow vendor blogs (Microsoft Defender, Cisco Talos, CrowdStrike), training platforms (Practical Malware Analysis labs, REMnux VM, FLARE VM), and courses (SANS/GIAC tracks, online DFIR courses). Always run samples in air-gapped / host-only VMs, snapshot before/after, and capture PCAPs & memory for reproducibility. 📚🔐
#MalwareAnalysis #DFIR #ThreatHunting #Volatility #CuckooSandbox #Ghidra #VirusTotal #CyberSecurity #InfoSec #DigitalForensics #YARA
Live now and working on ReVa for Ghidra! An AI assistant for reverse engineering!
#Ghidra #ReverseEngineering #MCP #modelcontextprotocol #VTuber #malware #ReVa
https://twitch.tv/cyberkaida
https://github.com/cyberkaida/reverse-engineering-assistant
FlatOut 2 and FlatOut: Ultimate Carnage #decompilation effort github.com/ZackWilde27/... See also FlatOut Joint community: discord.com/invite/YAhWJ... #reverseengineering #retrodev #ghidra #programming #gamedev #retrogaming
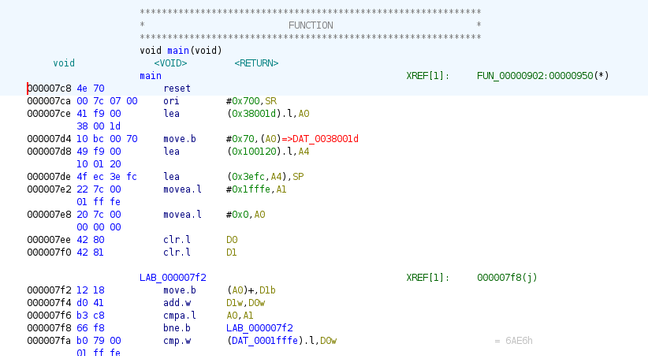
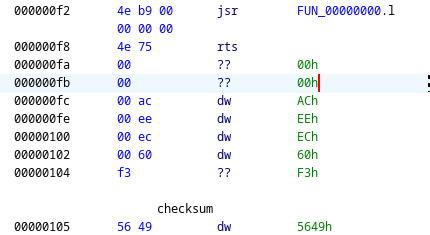
![Motorola 68k assembly listing in Ghidra, taken from a TI-92+ "Hello World" program.
save_screen XREF[1]: 0000003c(j)
0000004c 48 52 pea (A2)
0000004e 4f ef f1 00 lea (-0xf00,SP),SP
00000052 48 78 0f 00 pea (0xf00).w
00000056 48 78 4c 00 pea (0x4c00).w
0000005a 48 6f 00 08 pea (0x8,SP)
0000005e 24 68 09 a8 movea.l (0x9a8,A0),A2
00000062 4e 92 jsr (A2)
call asm_main
00000064 4e b9 00 jsr FUN_00000000.l
00 00 00
0000006a 48 78 0f 00 pea (0xf00).w
0000006e 48 6f 00 10 pea (0x10,SP)
00000072 48 78 4c 00 pea (0x4c00).w
00000076 4e 92 jsr (A2)
00000078 4f ef 0f 18 lea (0xf18,SP),SP
0000007c 24 5f movea.l (SP)+,A2
0000007e 4e 75 rts](https://files.mastodon.social/cache/media_attachments/files/115/363/652/544/655/034/small/97be23c7d3c0051c.png)