@raptor gold!
Security Chief Rocka @ X41
"Your malware is fake!" That's correct. Here's a small tool to generate payloads out of YARA rules: https://github.com/persistent-security/reverseyara
We use it as part of a testsuite for detection & monitoring.
X41 performed an audit of Hickory DNS which is an open source Rust based DNS client, server, and resolver. We were sponsored by the great folks at @ostifofficial and supported by @ProssimoISRG
Our full report can be downloaded here: https://x41-dsec.de/security/research/job/news/2025/03/10/hickory-review-2025/
Join me in October at hardwear.io for a training about eSIM! Register at https://hardwear.io/netherlands-2024/training/eSIM-eUICC-security-for-securitys-experts.php #esim #euicc
@G33KatWork @x41sec Unfortunately the collab with @q3k never happened......yet! ;-)
We just published our research on the use of power side channel analysis for fuzzing:
https://x41-dsec.de/news/2024/05/21/chipfuzz/
A cool bypass of "phishing proof" Okta MFA: https://www.persistent-security.net/post/when-phish-proof-gets-hooked
@briankrebs You realize this is known in various instances (DNS, DHCP, static routes, auto network discovery) since nearly two decades? There was a BH talk last year (https://tunnelcrack.mathyvanhoef.com/details.html), people tweeted about it (https://twitter.com/0xjomo/status/929044137957052416), conference submissions (me in 2011). Even the old Cisco VPN client (!) used to have a built-in mitigation for this.
The memory loss in infosec is one of our biggest problems today!
Chilkat PRNG Vulnerability Impact on E2EE Messenger ginlo https://x41-dsec.de/news/2024/04/09/ginlo/
Advisory X41-2024-001: Weak Chilkat PRNG
https://x41-dsec.de/lab/advisories/x41-2024-001-chilkat-prng/
There's also libc implementations written in Rust, a quite elaborate trolling. ;-)
Here's the project you all were wondering why it doesn't exist yet: https://digipres.club/@foone/111948980229300662, https://ioc.exchange/@azonenberg/110849751773610561
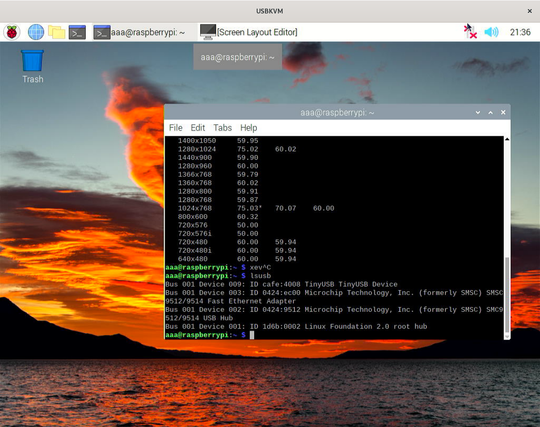
Introducing USBKVM! A keyboard, screen and mouse that all fit in your the palm of your hand!
It's built around the MS2109 HDMI to USB capture chip and its I²C interface connected to an STM32 MCU that takes care of the keyboard and mouse emulation.
While the hardware is fully functional, firmware and software are in a proof-of-concept stage. Stay tuned…
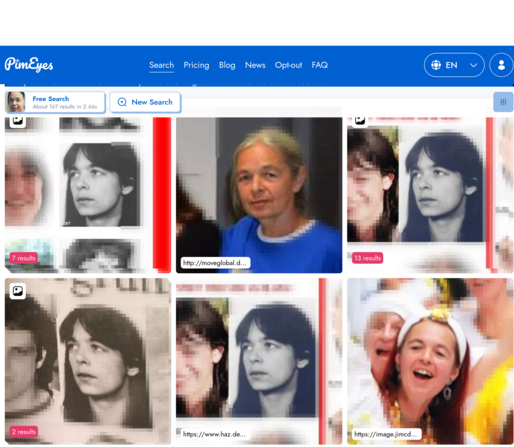
German police caught Daniela Klette from the RAF after 30 years on the run. Turns out she was living in the middle of Berlin, got a Facebook account and if you put her image into even one of the public biometric search engines, you can find her without much effort.
Ever wondered how to binary diff router firmwares to write n-day exploits?
Learn how @thezero and @suidpit combined unblob, binexport, ghidra, Qiling, and an Asus router to write an exploit for CVE-2023-39228.
The outcome was unexpected ...
While attending @silviocesare training at @cybersaiyan's RomHack @thezero and @suidpit chose to do some practice. While looking at the news they discovered about some recently disclosed ASUS routers unauthenticated RCEs.
They quickly bin-diffed the firmware versions, found the vulnerabilities, emulated the vulnerable firmware, and wrote and exploit for one of them.
This was so fast they had a working exploit even before jumping off the wayback 🚂.
Once at home they used their research budget to buy a real device and prove the vulnerability there too, but ... it was not working 🤯
Know what? The vulnerability was not unauthenticated on the physical device!
After some intense debugging sessions they discovered that not only that one but also a lot of other ASUS routers' vulnerabilities were probably incorrectly deemed as unauthenticated.
Apparently most of the researchers are either keeping an authentication bypass private or they do their research in emulated environments only and no one ever checked the vulnerabilities before issuing the CVE numbers and releasing the advisories.
TL;DR
Product security folks: do not blindly trust the attack requirements shared by the researchers.
Security researchers: when testing embedded devices make sure to mimic correctly all their configurations (i.e. the NVRAM content).
https://www.shielder.com/blog/2024/01/hunting-for-~~un~~authenticated-n-days-in-asus-routers/
We've posted two new blogs today about #security in #BIND. Check them out!
One specifically relates to the vulnerabilities disclosed yesterday: https://www.isc.org/blogs/2024-bind-security-release/
The other reports on our recent BIND 9 security audit: https://www.isc.org/blogs/2024-bind-audit/
We just released the results of our audit of BIND9, sponsored by ISC. Another interesting audit with @marver. Thanks to @ondrej for the support.
https://x41-dsec.de/news/security/research/source-code-audit/2024/02/13/bind9-security-audit/
X41 reviewed the source code of BIND9 for security issues on behalf of the @iscdotorg . More details and the full report are available here:
https://www.x41-dsec.de/news/security/research/source-code-audit/2024/02/13/bind9-security-audit
@marver and @mumblegrepper will provide a training NULLCON Berlin 2024. Register now: https://nullcon.net/berlin-2024/training/the-application-security-tool-stack